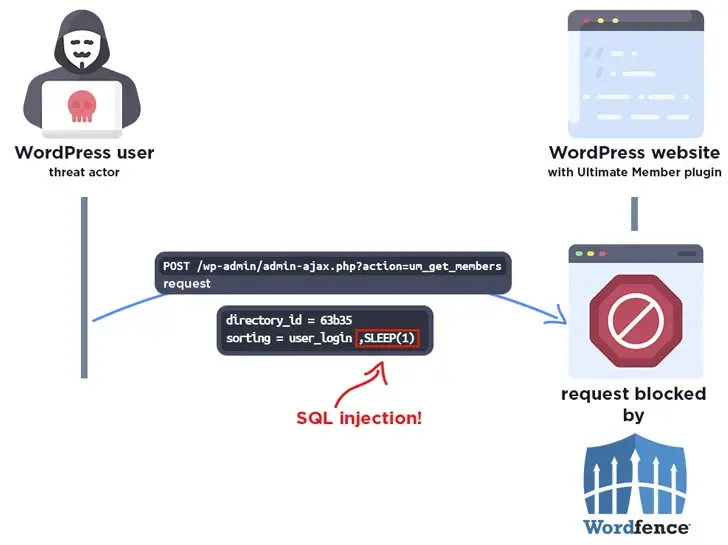
A well-known WordPress plugin called Ultimate Member, which has over 200 000 installed users, has a critical security flaw.
A CVSS score of 9.8 out of a maximum of 10 is associated with the vulnerability, tracked as CVE- 2024- 1071. Christiaan Swiers, a security researcher, is credited with finding and reporting the error.
Due to insufficient escaping on the user-provided parameter and lack of preparation for the existing SQL query, WordPress security company Wordfence stated in an advisory released last week that the plugin is “vulnerable to SQL Injection via the’sorting ‘ parameter in versions 2.1.3 to 2.2.8.2”.
Unauthenticated attackers could then exploit the flaw to add more SQL queries to already-existing queries and extract sensitive data from the database.
Users who have checked the” Enable custom table for usermeta” option in the plugin’s settings should be aware of the issue.
With the release of version 2. 8.3 on February 19, a fix for the flaw was made available by the plugin developers following responsible disclosure on January 30, 2024.
Users are advised to update the plugin to the most recent version as soon as possible, especially given that Wordfence has already blocked one attack trying to exploit the flaw over the past 24 hours.
Threat actors actively exploited another flaw in the same plugin ( CVE- 2023- 3460, CVSS score: 9.8 ) to create rogue admin users and seize control of vulnerable websites in July 2023.
A new campaign that makes use of compromised WordPress sites to directly encrypt users using crypto drainers like Angel Drainer or redirect site visitors to Web3 phishing sites that contain drainers is gaining popularity with this development.
According to Sucuri researcher Denis Sinegubko,” These attacks use phishing tactics and malicious injections to exploit the Web3 ecosystem’s reliance on direct wallet interactions,” putting a significant risk on both website owners and the security of user assets at risk.
Additionally, it comes as a result of the discovery of a brand-new drainer-as-a-service ( DaaS ) program called CG ( short for CryptoGrab ), which has a 10, 000-strong affiliate program made up of speakers of Russian, English, and Chinese.
According to a report released late last month, one of the actors ‘ controlled Telegram channels “refers attackers to a telegram bot that enables them to conduct their fraud operations without any third-party dependencies.”
The bot provides Cloudflare protection for that new domain, enables a user to obtain a domain for nothing, clone an existing template for the new domain, and set the wallet address where the scammed funds are supposed to be sent.
Additionally, a threat group has been spotted utilizing two unique Telegram bots, SiteCloner and CloudflarePage, to clone an existing, legitimate website and add Cloudflare protection, respectively. These pages are then primarily distributed using X ( previously Twitter ) accounts that have been compromised.