Over 8, 000 legitimate internet domains and 13, 000 subdomains are used in the massive ad fraud campaign” SubdoMailing,” which uses up to five million emails per day to make money through fraud and deceit.
Threat actors use abandoned subdomains and domains owned by well-known companies to send their malicious emails as part of the campaign known as” SubdoMailing.”
These domains benefit from being able to get around spam filters and, in some cases, use configured SPF and DKIM email policies to let secure email gateways know that the emails are legitimate and not spam because they are owned by reputable businesses.
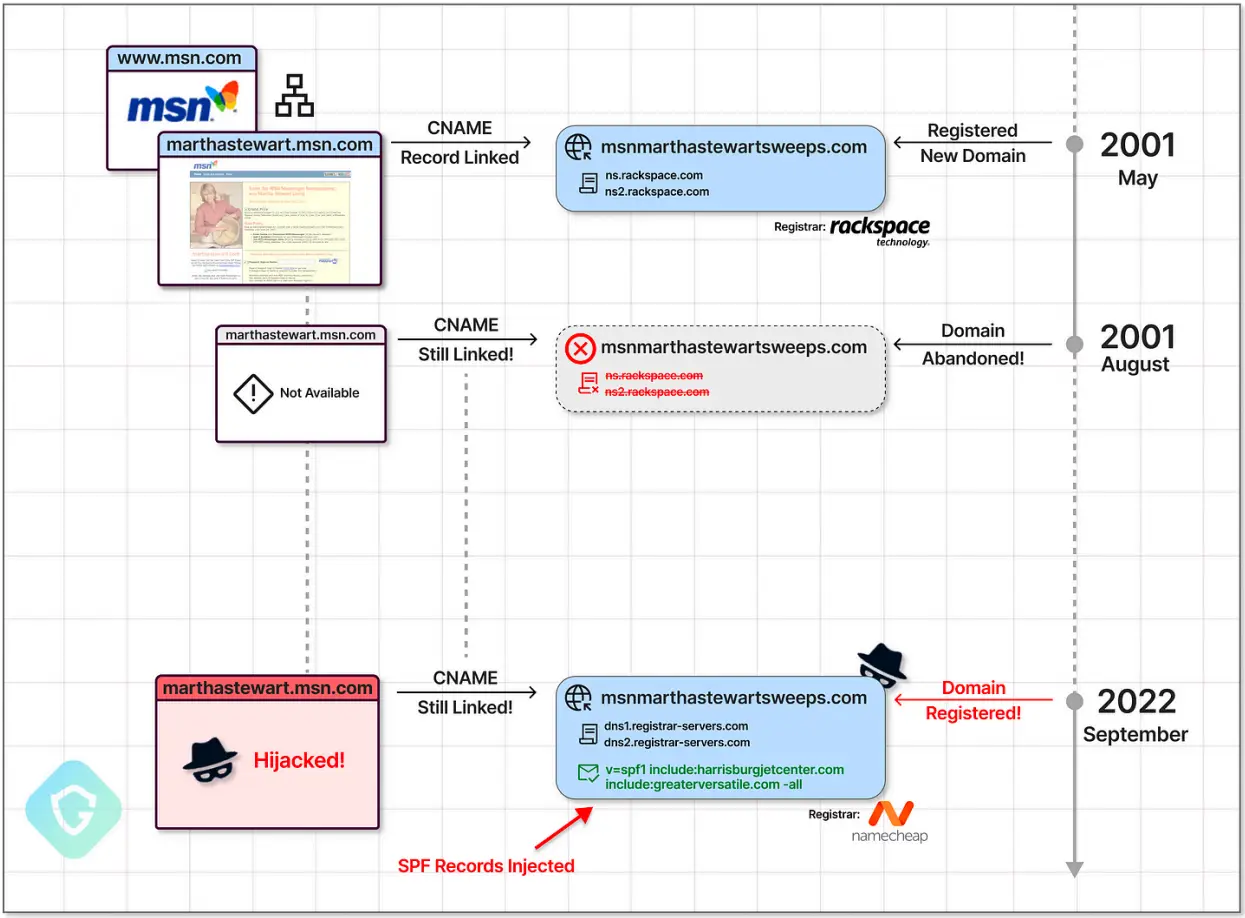
This domain hijacking campaign affected a number of well-known brands, including MSN, VMware, McAfee, The Economist, Cornell University, CBS, and NYC. Better Business Bureau, Unicef, ACLU, Symantec, Java, PWC, Pearson, and government. eBay, Marvel, and Net.  ,
These well-known companies unintentionally give the fake emails legitimacy and aid in filtering them.
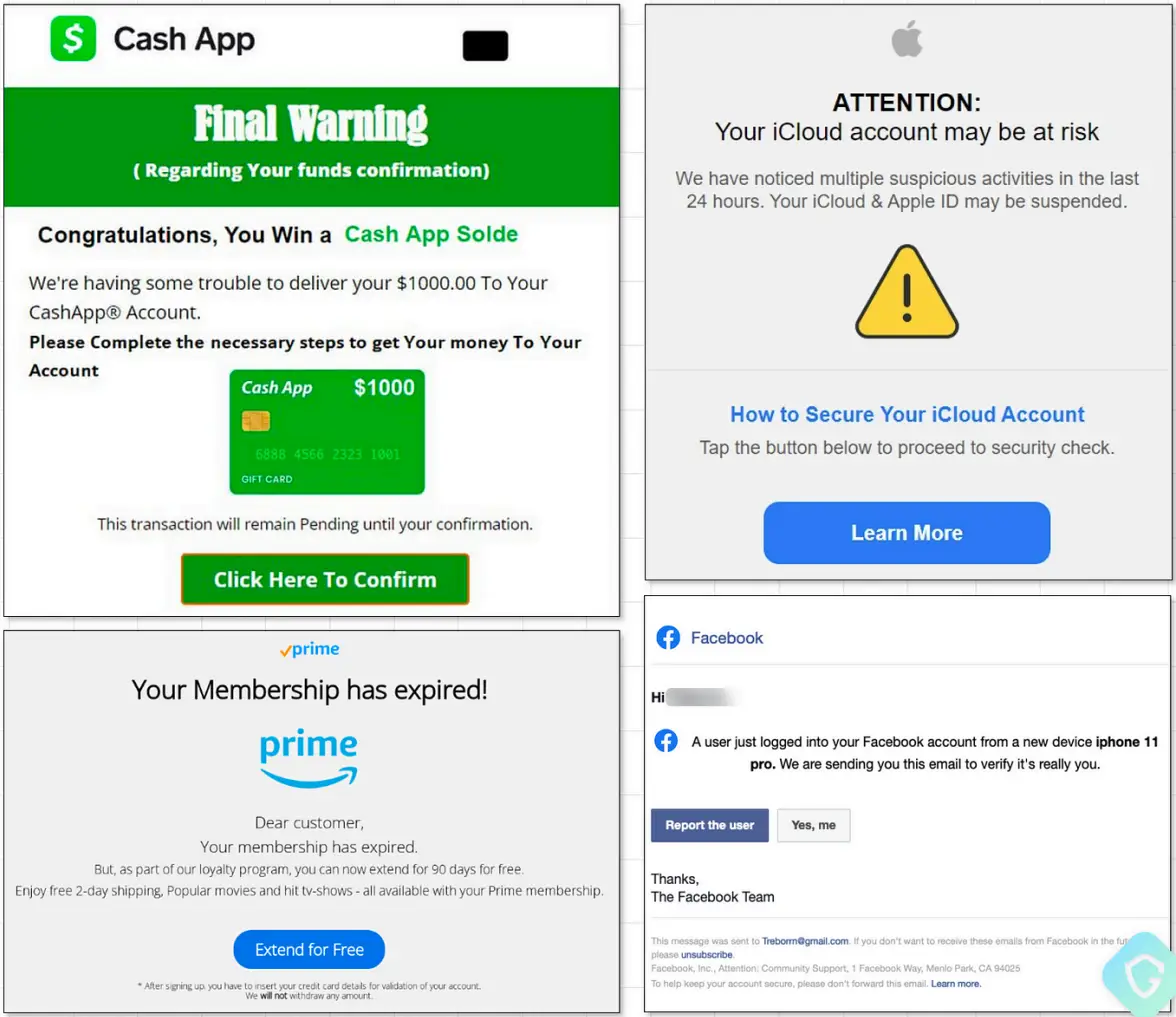
Users are directed through a series of redirections when they click on the embedded buttons in emails, which helps the threat actors make money by generating false clicks on their ads. In the end, the user encounters fictitious giveaways, security checks, surveys, or affiliate scams.
The ad fraud campaign was discovered by Guardio Labs  researchers Nati Tal and Oleg Zaytsev, who also reported that it had been going on since 2022.
 , Guardio Labs is the source.
spamming domain hijacking
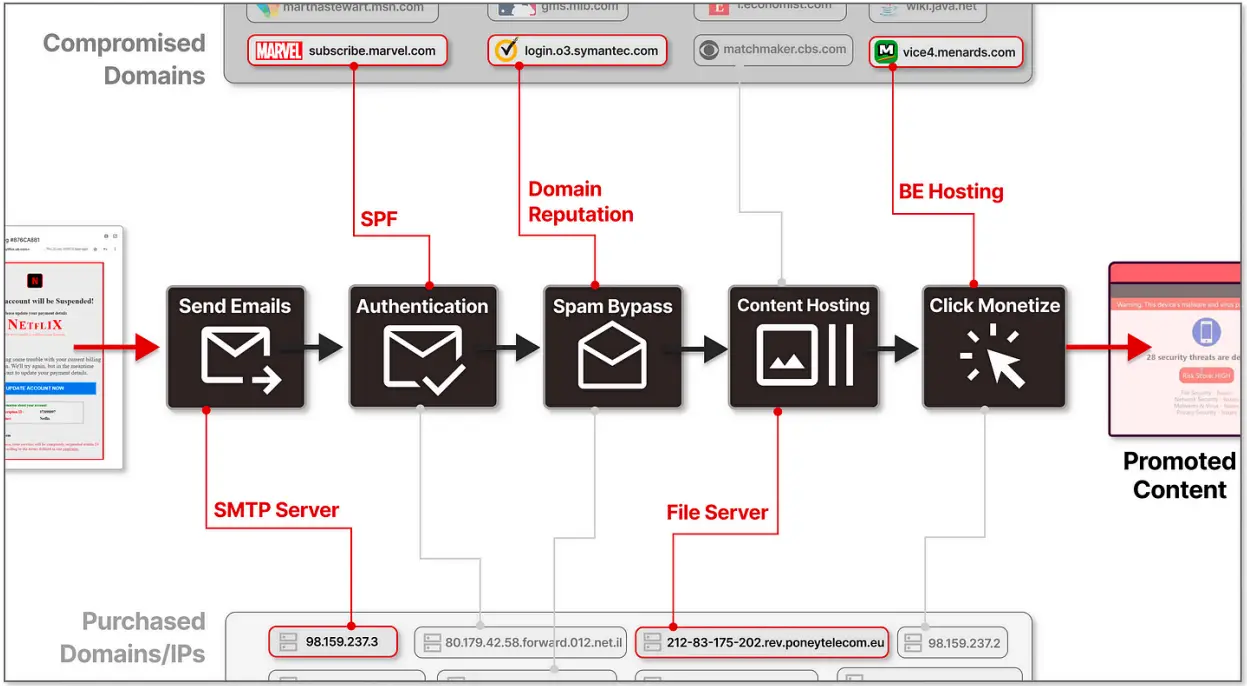
A significant subdomain hijacking operation was discovered as a result of Guardio Labs ‘ investigation, which started with the discovery of unusual patterns in email metadata.
The attackers used a variety of strategies, including abusing SPF ( Sender Policy Framework ) checks, DKIM ( DomainKeys Identified Mail ), and DMARC ( Domain-based Message Authentication, Reporting, and Conformance ) protocols, to make their emails appear legitimate and get around MSN’s false authorization.
These email policies are used to demonstrate to email gateways that an email’s sender is legitimate and should n’t be regarded as spam.
 , Guardio Labs is the source.
The SubdoMailing campaign primarily uses CNAME hijacking and SPF record exploitation to target domains and subdomains of reputable organizations.
Threat actors look for subdomains of well-known brands with CNAME records pointing to external, no-registered domains in order to carry out an attack on them. The NameCheap service is then used by them to register these domains.
 , Guardio Labs is the source.
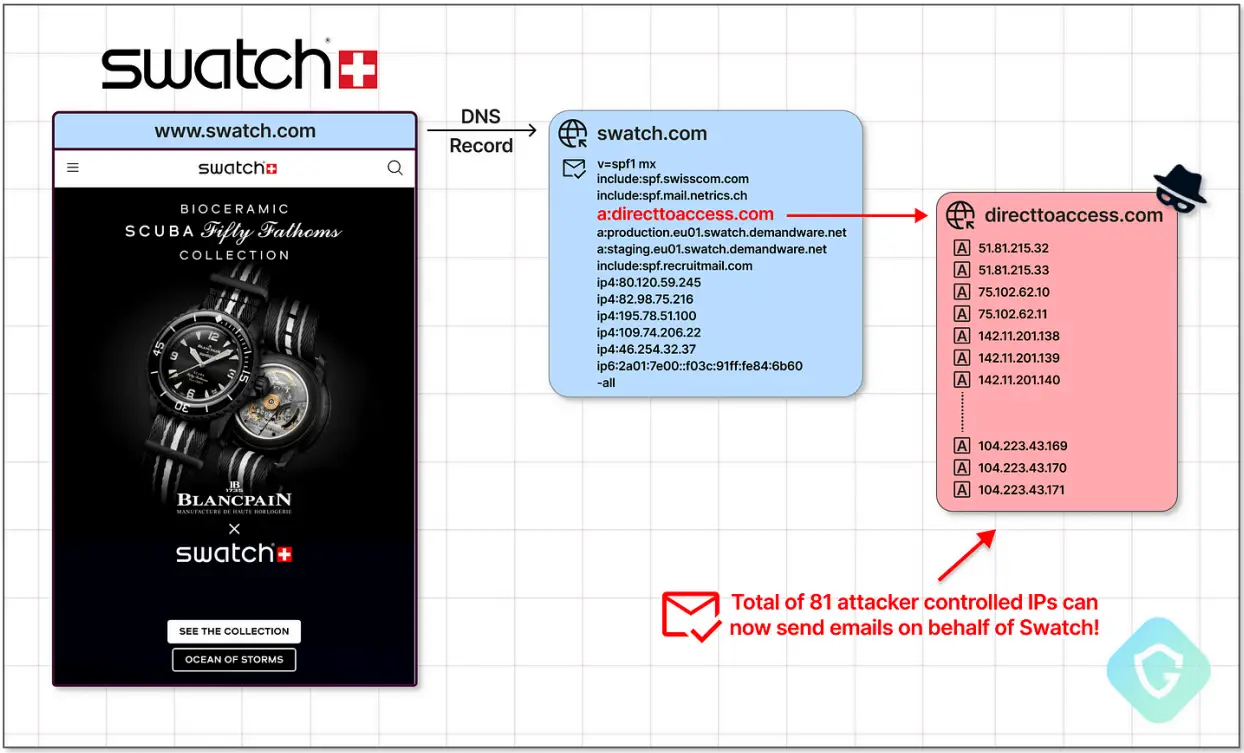
The second approach involves examining the SPF records of target domains that use the “include :”configuration option to point to revoked external domain registrations.
The threat actor now has control over the external domain, which is used to import authorized email senders using the SPF include option.
These domains are registered by attackers, who then modify their SPF records to give their own malicious email servers permission. As a result, it appears that the threat actor’s emails are legitimately coming from MSN or another reputable domain.
 , Guardio Labs is the source.
The operation typically hosts phishing pages, sends spam emails, and hosts deceptive advertising content using the hijacked domains.
a sizable campaign
Guardio Labs credits a threat actor they refer to as” ResurrecAds” with the campaign. He routinely searches the web for hijacked domains, finds new hosts and IP addresses, and purchases targeted domain names.
To maintain the operation’s scope and complexity, the threat actor regularly updates a sizable network of seized and acquired domains, SMTP servers, and IP addresses.
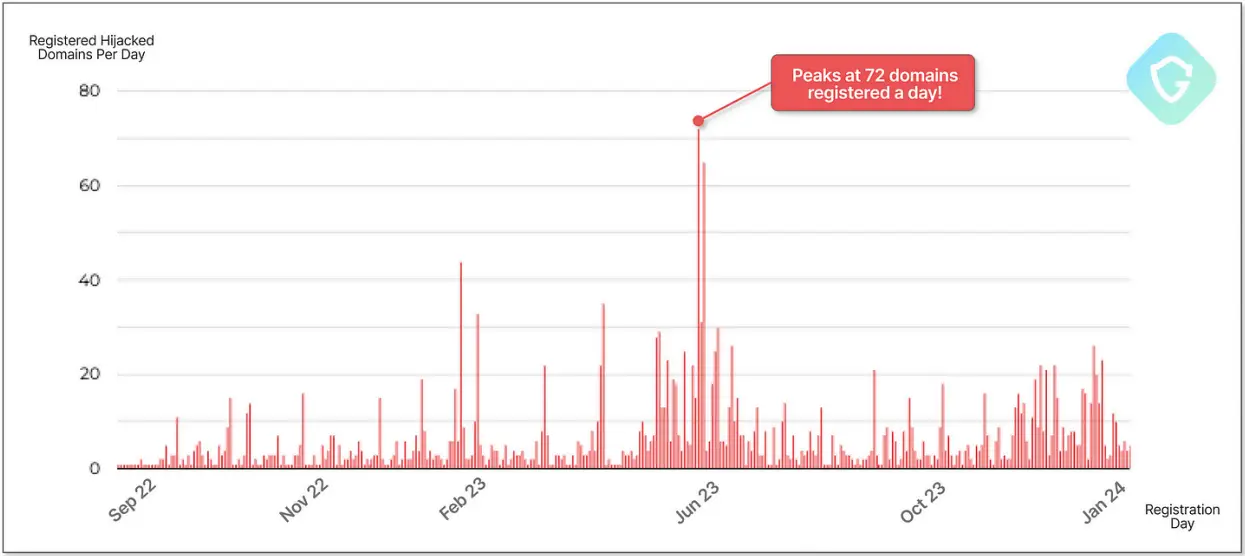
 , Guardio Labs is the source.
According to Guardio Labs, SubdoMailing makes use of nearly 22, 000 distinct IP addresses, 1,000 of which appear to be home proxies.
Currently, the campaign uses widely dispersed SMTP servers that are set up to spread fake emails over an extensive network of 8, 000 domains and 13, 000 subdomains.
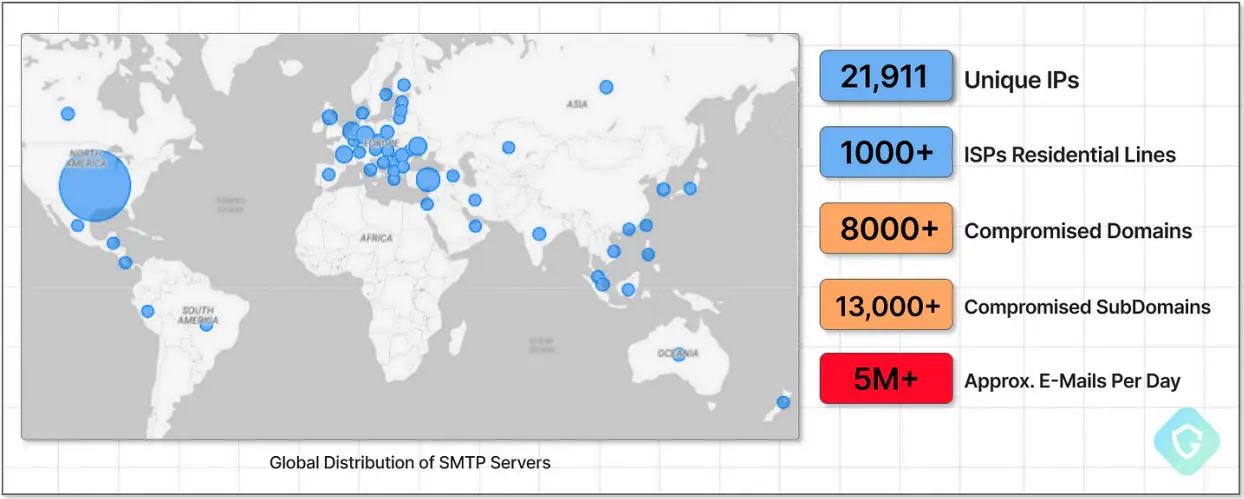
 , Guardio Labs is the source.
Over 5,000, 000 emails are delivered to targets each day. The size and volume of the fraudulent emails are undeniably enormous, even though it is impossible to estimate the attacker’s profit from this.
To help domain owners identify when their brand is being abused and take action to stop or prevent it, Guardio Labs has developed the a , SubdoMailing, and nnpsv checker site.











