Update: Changed title and content to understand that this is a Flipper Zero-style phishing attack that could be carried out on other devices.
Researchers demonstrated how to hack Tesla accounts, unlock cars, and start them using a Man-in-the-MiTM ( MiTM) phishing attack. The attack is compatible with the most recent versions of the Tesla game, version 4.30.6, and the latest versions of the Tesla software, version 11.1 2024.2.7.
Security experts Talal Haj Bakry and Tommy Mysk  created a new” Phone key” that could be used to gain access to the Tesla as part of this invasion.
Tesla, which claims that connecting a automobile to a new phone lacks proper authentication safety, is the subject of a report from the researchers to. The automaker, but, determined that the document was inappropriate.
The researchers used a Flipper Zero to carry out this hacking attack, but it could also be carried out using different hardware, such as a computer, a Raspberry Pi, or Android devices.
Phishing strike
A hacker at a Tesla compressor place could use an SSID known as” Tesla Guest,” which is prevalent in Tesla service locations and Tesla car owners are familiar with.
The WiFi system can be broadcast using a Raspberry Pi or different products with WiFi hotspot features, according to Mysk, who only recently used a Flipper Zero to do so.
A false Tesla registration page that asks users to log in using their Tesla accounts credentials is displayed once the target logs into the spoofed network. The intruder can see on the Dolphin Zero anything a prey enters on the spoofing page in real time.
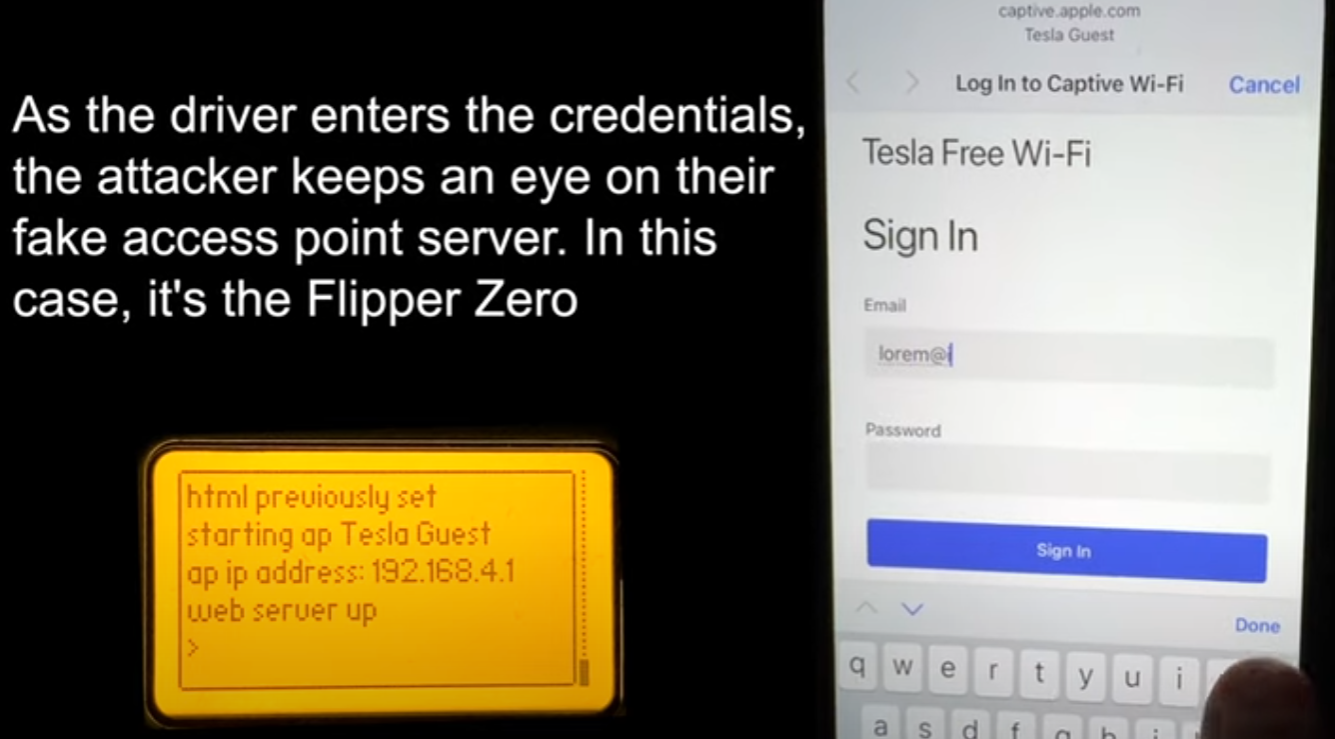
The hacking site asks for the Tesla account’s one-time password in order to enable the attacker to pass the two-factor authentication protection after receiving the account credentials after entering the account information.
Before the OTP expires, the perpetrator must use the stolen credentials to log into the Tesla software. The risk artist has the ability to track the location of the car in real-time once it has been captured in the account.
Adding a fresh code
The attacker can create a new” Phone Key” with access to the murderer’s Tesla bill. They may be a dozen feet away from the car in order for this to occur.
Phone Keys uses the car owner’s smartphone and Tesla’s mobile app to instantly unlock and lock the vehicle via a secure Mobile connection.
Tesla automobiles even employ Card Keys, which are small RFID cards that must be inserted into the core console’s RFID reader. Even though they are safer, Tesla uses them as a backup plan when the phone code is dead or in use.
According to Mysk, adding a fresh Phone Key via the software does not require the car’s smartphone or unlock, which creates a major security gap.
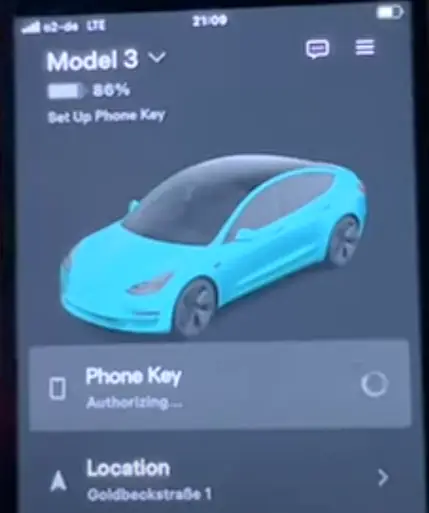
Even worse, once a fresh Phone Key is added, the Tesla user is not notified via the application or the car’s touchscreen when an alert is displayed.
The perpetrator can unlock the car and unlock all of its components with the fresh Phone Key, enabling them to leave as if they were the car’s owner.
embedded content ]
Mysk information that the Tesla Model 3 attack was successful. The scholar notes in the statement to the car manufacturer that the primary driver must already be connected to a Phone Key and that the stolen Tesla account must already be there.
The researchers contend that adding a bodily Tesla Card Key when adding a fresh Phone Key would increase safety by adding a level of authentication for the new phone.
Without the Tesla software requiring me to use a key cards to confirm the program on the new iPhone, I was able to put a second phone key. The game activated the smartphone key after I gave it access to the area services on the new iPhone using only my username and password, according to Tommy Mysk and ’s Talal Haj Bakry in a report to Tesla.
The company responded by stating that the investigation revealed the desired behavior and that the Tesla Model 3 manager’s guide does not require a key cards to include a phone essential.
We have never heard back from Tesla, but BleepingComputer has contacted them with questions regarding the above and whether they intend to release an OTA upgrade that introduces safety measures to stop these problems.











