A critical severity privilege escalation flaw known as CVE-2024-21410 that hackers are actively exploiting may expose up to 97 000 Microsoft Exchange servers.
On February 13, after it had already been leveraged as a zero-day, Microsoft addressed the problem.  , 28, 500 servers have all been found to be at risk at the moment.
Exchange Server, which offers  , email, calendar, contact management, and task management services, is frequently used in business settings to facilitate user communication and collaboration.
Due to the security flaw, remote, unauthenticated actors can attack Microsoft Exchange Servers using NTLM relays and increase system privileges.
Threat monitoring service Shadowserver announced today that 97, 000 potentially vulnerable servers have been found by its scanners.
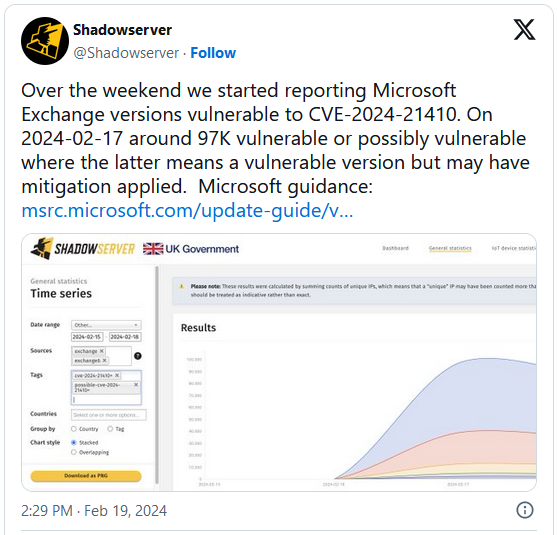
Out of the total 97, 000 servers, 28, 500 are confirmed to be CVE-2024-21410 vulnerable, with an estimated 68,500 servers depending on whether administrators applied and nbsp mitigations.
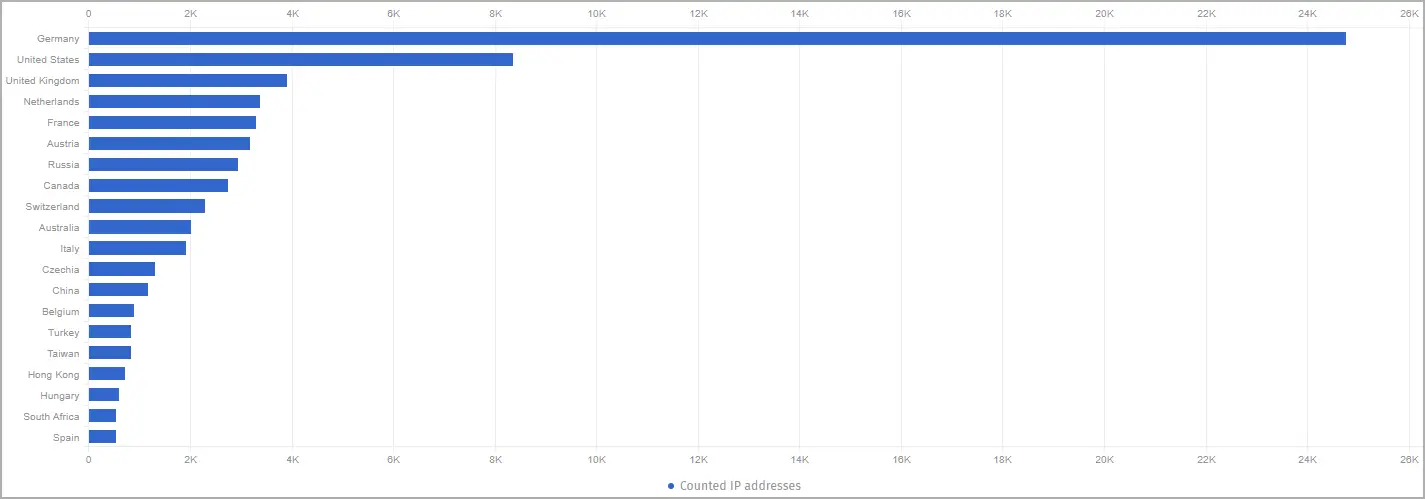
Germany ( 22, 903 instances ), the United States ( 434), the UK (3, 665 ), France ( 37 ), Austria ( 2787 ), Russia ( 771 ) ), Canada ( 571 ), and Switzerland ( 119 ), are the nations most affected.
The number of attackers using the flaw in attacks is somewhat constrained because there is currently no publicly accessible proof-of-concept ( PoC ) exploit for CVE-2024-21410.
System administrators are advised to use the Exchange Server 2019 Cumulative Update 14 ( CU14 ) update, which enabled NTLM credentials Relay Protections, to address CVE-2024-21410.
Federal agencies have until March 7, 2024 to apply the available updates or stop using the product, according to the U.S. Cybersecurity &, Infrastructure Security Agency’s ( CISA )” Known Exploited Vulnerabilities” catalog.
Attackers with elevated permissions on an Exchange Server can access sensitive information like email communication and use the server as a launchpad for additional network attacks, so exploitingCVE-2024-21410 can have serious repercussions for an organization.











