Less than a week after law enforcement hackers compromised their servers, the LockBit gang is resuming its ransomware operation on new infrastructure and has threatened to concentrate more of its attacks on the government.
The gang published a lengthy message about their negligence in allowing the breach and the plans for the operation going forward under an fictitious FBI leak in an effort to draw attention.
Attacks by LockBit ransomware continue.
Authorities demolished LockBit’s infrastructure on February 19 along with 34 servers that hosted the data leak website and its mirrors, victim data, cryptocurrency addresses, decryption keys, and the affiliate panel.
In order to make their infrastructure more resistant to hacking, LockBit is back five days later and offers information about the breach and how they plan to run the company.
The gang confirmed the breach right away, claiming that only PHP-based servers were lost and that backup systems were unaffected.
Operation Cronos was disrupted by law enforcement due to “personal negligence and irresponsibility,” according to a damage control communication released by LockBit on Saturday.
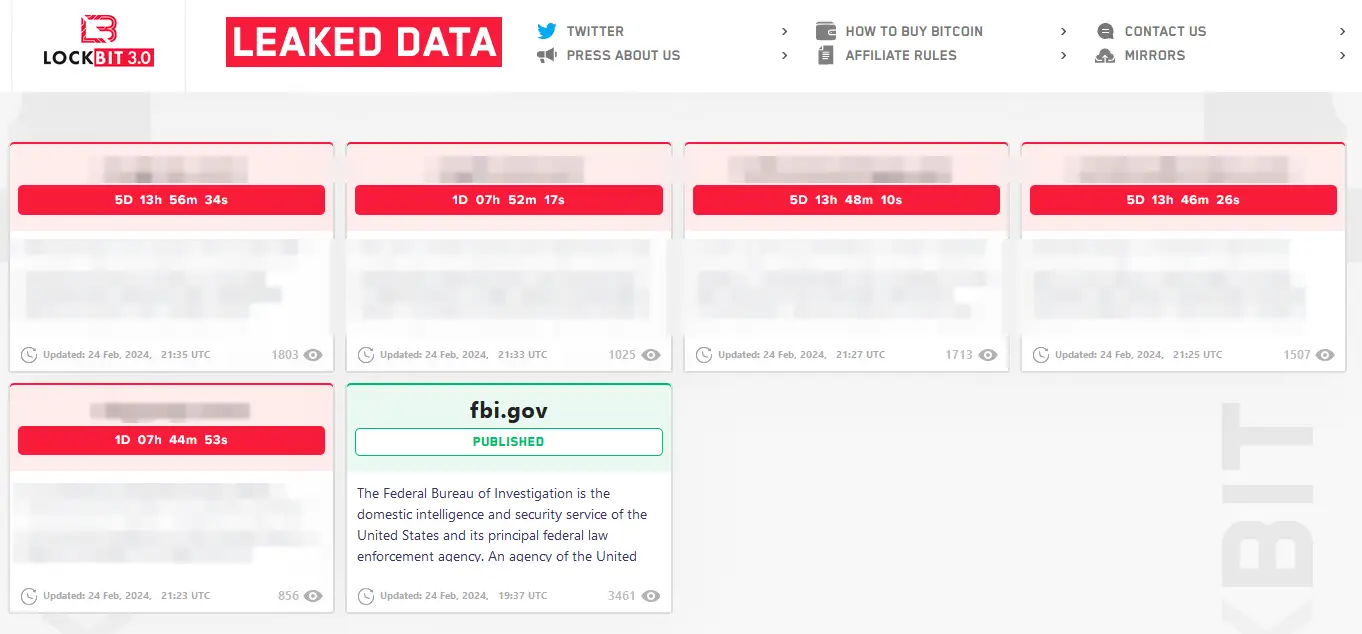
Five victims with countdown timers for publishing stolen information are listed at the new .onion address where the gang relocated its data leak site while maintaining the brand name.
On the “leaked data” page of LockBit, some organizations seem to have been the targets of well-known attacks.  ,
BleepingComputer is the source.
PHP server that is outdated
According to LockBit, the FBI—as a whole—broke into two main servers “because for five years of swimming in money I became very lazy.”
” I relaxed and did not update PHP in time because of my own carelessness and irresponsibility.” According to the threat actor, a critical vulnerability known as CVE-2023-3824 was most likely used to hack the victim’s admin, chat panel, and blog servers, which were all running PHP 8.1.2.
According to LockBit, the PHP server has been updated, and anyone who discovers a flaw in the most recent version will be rewarded.
The cybercriminal speculates that” the FBI” compromised their infrastructure as a result of the ransomware attack on Fulton County in January, which raised the possibility of information leakage regarding” a lot of interesting things and Donald Trump’s court cases that could affect the upcoming US election.”
This gave LockBit the idea that by attacking” the .gov sector” more frequently, they would be able to force the FBI to demonstrate its gang-attacking prowess.
According to the threat actor, law enforcement “obtained a database, web panel sources, locker stubs that are not sources as they claim, and some unprotected decryptors.”
affiliate panels that are decentralized
More than 1,000 decryption keys were gathered by the authorities during Operation Cronos. According to LockBit, there were nearly 20,000 decryptors on the server, or roughly half of the roughly 40, 000 generated over the course of an operation, from which the police obtained the keys.
Unprotected decryptors, according to the threat actor, are variants of file-encrypting malware that are typically used by low-level affiliates who demand ransoms as low as$ 2, 000 and do not have the “maximum descryption protection” feature enabled.
In addition to hosting the affiliate panel on multiple servers and giving its partners access to various copies depending on their level of trust, LockBit intends to improve infrastructure security and switch to manually releasing decryptors and trial files.
LockBit’s lengthy message appears to be an effort to repair credibility for a damaged reputation and damage control.
Even though the gang was able to restore the servers, affiliates still have good reason to be wary.











