A representative of the company is selling the purported source code for the third iteration of Knight ransomware to a single buyer on an online hacker forum.
A , a re-brand of the Cyclops operation, was introduced as Knight ransomware at the end of July 2023. It was intended for Windows, macOS, and Linux/ESXi systems.
Because it offered info-snatchers and a “lite” version of its encryptor  to lower-tier affiliates who attacked smaller organizations, it gained some traction.
Threat analysts at the cyber-intelligence company KELA  noticed the advertisement two days ago that was posted on RAMP forums under the alias Cyclops and identified as a Knight ransomware gang representative.
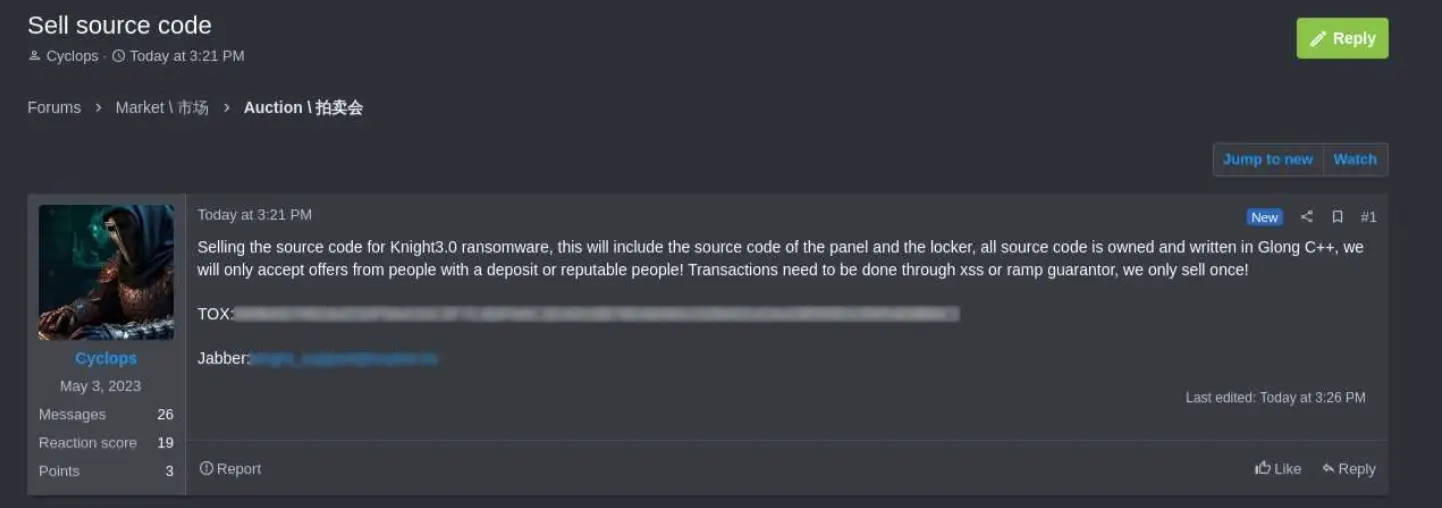
Cyclops writes in the post,” Selling the source code for Knight 3.0 ransomware, this will include the panel and locker source codes.  ,
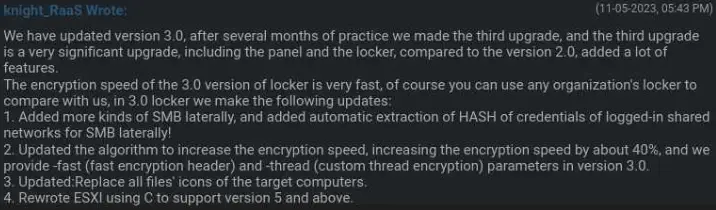
On November 5, 2023, Knight’s locker version 3.0 was made available, adding features like 40 % faster encryption, a rewritten ESXi module for add , support for more recent hypervisor versions, and many more.  ,
The threat actor emphasized that the source code would only be sold to one buyer, maintaining its value as a private tool, but he did not specify the ABSP or price.
According to Cyclops, trustworthy users would receive a deposit priority, and transactions would be guaranteed on the RAMP or XSS hacker forums.
For potential buyers to get in touch with and negotiate a final deal, the seller has posted contact information for Jabber and TOX messaging services.
The Jabber is new andnbsp, according to KELA, but the TOX ID listed on the forum post was previously associated with Knight, giving the sale legitimacy.
Knight’s representatives have not been active on any forums since December 2023, despite the fact that the motivation for selling the source code for Knight ransomware is still unknown.
The most recent victim was listed on February 8; the victim extortion portal for the ransomware operation is also currently offline. Knight asserted to have violated 50 organizations since July  , 2023.
The Knight ransomware operation appears to have been dormant for some time, according to KELA’s information, suggesting that the organization may be considering closing its doors and selling its assets.











