Your cart is currently empty!
Author: Omar

Microsoft Confirms Russian Hackers Stole Source Code, Some Customer Secrets
NewsroomCyber Attack / Threat Intelligence On Friday, Microsoft announced that the Kremlin-supported group known as Midnight Blizzard (also called APT29 or Cozy Bear) accessed some of its source code repositories and internal systems after a hack discovered in January 2024. “Recently, we have seen proof that Midnight Blizzard is using information taken from our…

The Week in Ransomware – March 8th 2024 – Waiting for the BlackCat rebrand
We saw another ransomware operation shut down this week after first getting breached by law enforcement and then targeting critical infrastructure, putting them further in the spotlight of the US government. What makes this strange is that this seems to be a common routine for the DarkSide, I mean BlackCat/ALPHV, ransomware operation which tends to…

Critical Fortinet flaw may impact 150,000 exposed devices
Scans on the public web show that approximately 150,000 Fortinet FortiOS and FortiProxy secure web gateway systems are vulnerable to CVE-2024-21762, a critical security issue that allows executing code without authentication. America’s Cyber Defense Agency CISA confirmed last month that attackers are actively exploiting the flaw by adding it to its Known Exploited Vulnerabilities (KEV)…

QNAP warns of critical auth bypass flaw in its NAS devices
QNAP warns of vulnerabilities in its NAS software products, including QTS, QuTS hero, QuTScloud, and myQNAPcloud, that could allow attackers to access devices. The Taiwanese Network Attached Storage (NAS) device maker disclosed three vulnerabilities that can lead to an authentication bypass, command injection, and SQL injection. While the last two require the attackers to be authenticated on…

Some Change Healthcare store companies are up online thanks to United Health.
Following next month’s terrible BlackCat malware attack, which caused widespread disruption to the US healthcare system, Optum’s Change Healthcare has begun to restore systems to normal operation. The largest American health insurance company is United Health Group ( UGG), and its subsidiary, Optum Solutions, runs the Change Healthcare system. The US’s largest settlement exchange platform…

Microsoft claims that Russian hackers hacked into its systems and obtained source code.
According to Microsoft, the Soviet” Midnight Blizzard” hacking group recently used identification secrets stolen from a cyberattack in January to access some of its internal systems and resource code libraries. After launching a password-spy assault that gained access to a legacy non-production check tenant account in January, Microsoft revealed that Midnight Blizzard ( also known…
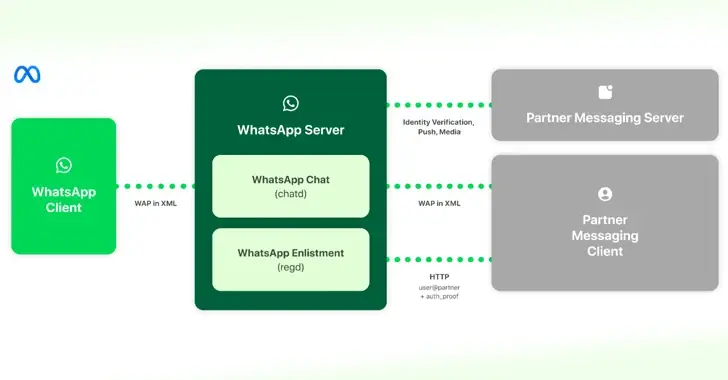
Information WhatsApp and Messenger Interoperability to Follow EU’ s DMA Regulations
Mar 08, 2024NewsroomInteroperability / Cryptography Meta has offered details on how it intends to implement interoperability in WhatsApp and Messenger with third- party messaging services as the Digital Markets Act ( DMA ) went into effect in the European Union. ” This allows customers of third- group providers who choose to allow interoperability ( interop…

Techniques Sensei: Defending Management Obstacles
Mar 08, 2024The Hacker NewsSecrets Management / Access Control In the realm of cybersecurity, the stakes are sky-high, and at its core lies secrets management — the foundational pillar upon which your security infrastructure rests. We’re all familiar with the routine: safeguarding those API keys, connection strings, and certificates is non-negotiable. However, let’s dispense with…

Cisco releases a piece for the Secure Client High-Severity VPN Hijacking Bug.
Mar 08, 2024NewsroomNetwork Security / Risk Cisco has released patches to handle a higher- intensity security flaw impacting its Secure Client software that could be exploited by a threat actor to start a VPN session with that of a qualified user. The networking equipment company described the vulnerability, tracked as CVE- 2024- 20337 ( CVSS…

Exploited as a routing device for a network of companies
NewsroomEndpoint Security / Network Security / Mar 08, 2024 During a cyberattack aimed at an unknown “large business,” risk actors have been spotted using the QEMU open-source equipment emulator as tunneling software. The growth marks the second QEMU that has been employed for this purpose, despite the fact that adversaries have already used a number…
