Your cart is currently empty!
Author: Omar
Cutout worth$ 20 million. On a data breach forum, private user data was leaked.
Cutout for AI services. A data breach at Pro exposed the personal data of 20 million users, including email addresses, passwords that have been hashed and salted, IP addresses, and names. Cutout. For content generation, image enhancement, background removal, diffusion, colorization, old photo restoration, and content generation, Pro is an AI-powered photo and video editing…
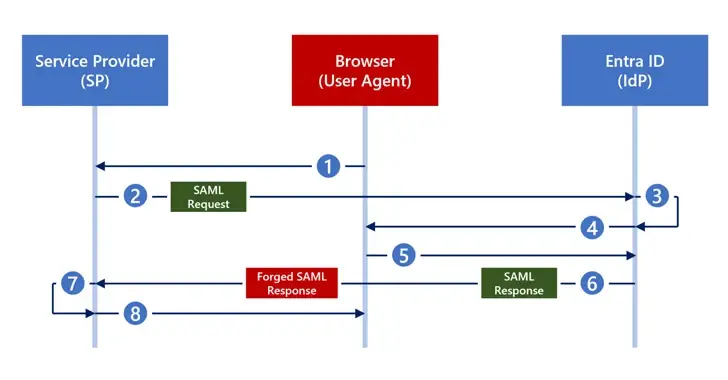
Golden SAML defenses in identity systems are undermined by a new Silver SAML attack.
NewsroomThreat Intelligence / Cyber Threat on February 29, 2024 Silver SAML, a new attack strategy developed by researchers in cybersecurity, is capable of succeeding even when Golden SAML mitigations have been used. In a report shared with The Hacker News, Semperis researchers Tomer Nahum and Eric Woodruff claimed that Silver SAML “enables the exploitation of…
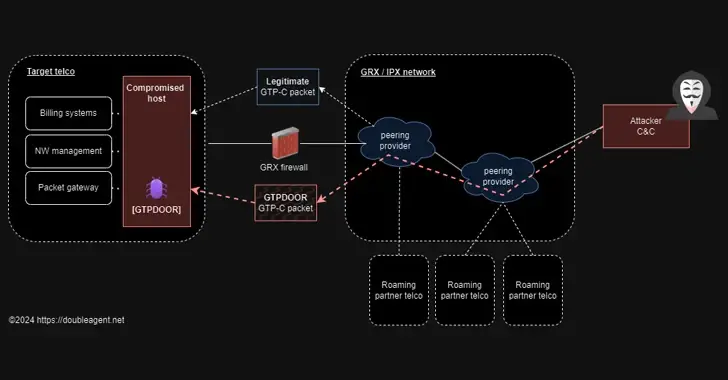
Exploiting GPRS Roaming Networks, GTPDOOR Linux Malware targets telecoms
29-Feb-2024 NewsroomLinux / Network Security GTPDOOR, a new Linux malware that is intended to be used in telecom networks close to GPRS roaming exchanges ( GRX ), has been discovered by threat hunters. The <a href="https://doubleagent.net/telecommunications/backdoor/gtp/2024/02/27/GTPDOOR-COVERT-TELCO-BACKDOOR” rel=”noopener” target=”_blank”>malware’s use of the GPRS Tunnelling Protocol ( GPP ) for command-and-control ( C2 ) communications is novel.…

In recent attacks, lazarus hackers exploited the Windows Kernel Flaw as Zero-Day.
Feb 29, 2024NewsroomRootkit / Threat Intelligence The notorious Lazarus Group actors exploited a recently patched privilege escalation flaw in the Windows Kernel as a zero- day to obtain kernel- level access and disable security software on compromised hosts. The vulnerability in question is CVE- 2024- 21338 ( CVSS score: 7.8), which can permit an attacker…

A Risk-Based Approach to Prioritizing Cybersecurity Spending for the Highest ROI
Feb 29, 2024The Hacker NewsAttack Surface / Incident Response As an IT leader, staying on top of the latest cybersecurity developments is essential to keeping your organization safe. But with threats coming from all around — and hackers dreaming up new exploits every day — how do you create proactive, agile cybersecurity strategies? And what…

Linked to Indian Diplomatic Events: New Backdoor Targeting European Officials
29-Feb-2024NewsroomCyber Espionage / Malware SPIKEDWINE, an undocumented threat actor known as SPIKEDWINE, has been spotted using a new backdoor called WINELOADER to target officials in European nations with Indian diplomatic missions. According to a report from Zscaler ThreatLabz, the adversary sent allegedly from the Indian ambassador a PDF file inviting diplomatic staff to a wine-tasting…
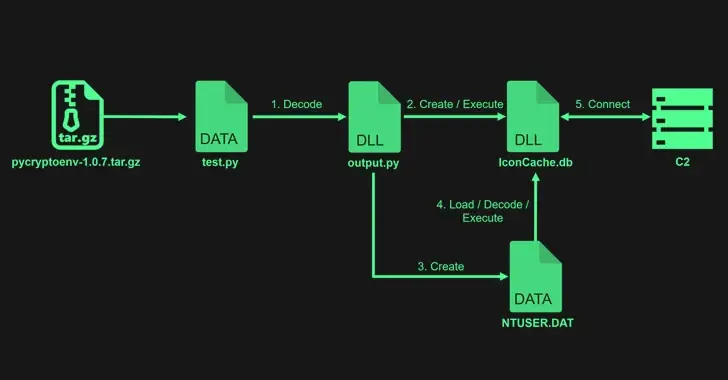
PyPI malware is smuggled into Dev systems by Lazarus via Typos.
29-Feb-2024 NewsroomMalware/Endpoint Security In order to infect developer systems with malware, the notorious North Korean state-backed hacking organization Lazarus uploaded four packages to the Python Package Index ( PyPI ) repository. Pycryptoenv, pycryptoconf, quasarlib, and swapmempool are the now-defunct packages. Together, they have been downloaded 3, 269 times, with pycryptoconf accounting for 1, 351 of…
Chinese Hackers
Chinese hackers are deploying new The exploitation of security flaws in Ivanti Connect Secure VPN devices has been linked to at least two different suspected China-linked cyber espionage clusters, identified as UNC5325 and UNC3886. UNC5325 distributed a wide range of brand-new malware called LITTLELAMB using CVE- 2024- 21893. According to Mandiant, Woolea, PITSTOP, PITDOG, PITJET,…

Biden, the president, blocks the transfer of personal information to high-risk countries.
U. S. President Joe Biden has issued an Executive Order that prohibits the mass transfer of citizens ‘ personal data to countries of concern. The Executive Order also “provides safeguards around other activities that can give those countries access to Americans ‘ sensitive data”, the White House said in a statement. This includes sensitive information…

Anycubic 3D printers were used to discover security flaws all over the world.
Image: Midjourney Someone hacked their 3D printers to warn them against attacks, according to a wave of online reports from Anycubic customers. A hacked_machine_readme was added by the person responsible for this incident. A critical security bug has been discovered in a device’s gcode file, which typically contains 3D printing instructions, alerting the affected users…
