Your cart is currently empty!
Author: Omar

Major brand-wide hacking subdomains were used in a massive spam campaign.
To send up to five million emails a day through scams and malvertising,” SubdoMailing,” a massive ad-fraud campaign, uses over 8, 000 legitimate internet domains and 13, 000 subdomains. The threat actors use abandoned subdomains and domains owned by well-known companies to send their obtrusive emails under the name” SubdoMailing.” Because these domains belong to…

5 million emails are spammed daily by the SubdoMailing campaign using 8k hijacked domains.
Over 8, 000 legitimate internet domains and 13, 000 subdomains are used in the massive ad fraud campaign” SubdoMailing,” which uses up to five million emails per day to make money through fraud and deceit. Threat actors use abandoned subdomains and domains owned by well-known companies to send their malicious emails as part of the…

Hackers from North Korea are using malicious npm packages to target developers.
Feb 26, 2024The Hacker NewsSoftware Security / Cryptocurrency A set of fake npm packages discovered on the Node.js repository has been found to share ties with North Korean state-sponsored actors, new findings from Phylum show. The packages are named execution-time-async, data-time-utils, login-time-utils, mongodb-connection-utils, and mongodb-execution-utils. One of the packages in question, execution-time-async, masquerades as its…

Three Ways to Prevent AI Accidents in Your Secrets
Last year, the Open Worldwide Application Security Project (OWASP) published multiple versions of the “OWASP Top 10 For Large Language Models,” reaching a 1.0 document in August and a 1.1 document in October. These documents not only demonstrate the rapidly evolving nature of Large Language Models, but the evolving ways in which they can be…
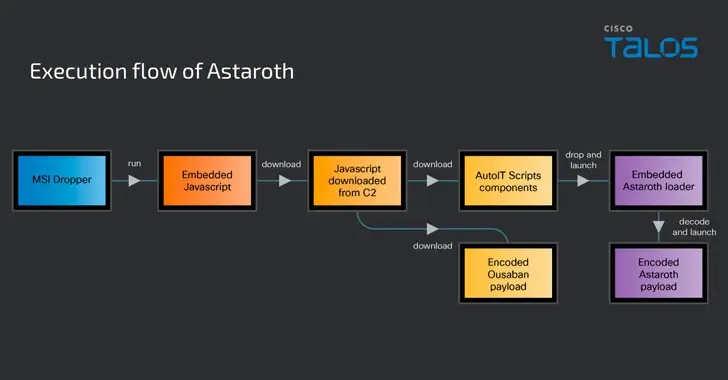
Banking Trojans Target Latin America and Europe Through Google Cloud Run
Cybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka Guildma), Mekotio, and Ousaban (aka Javali) to targets across Latin America (LATAM) and Europe. “The infection chains associated with these malware families feature the use of malicious…
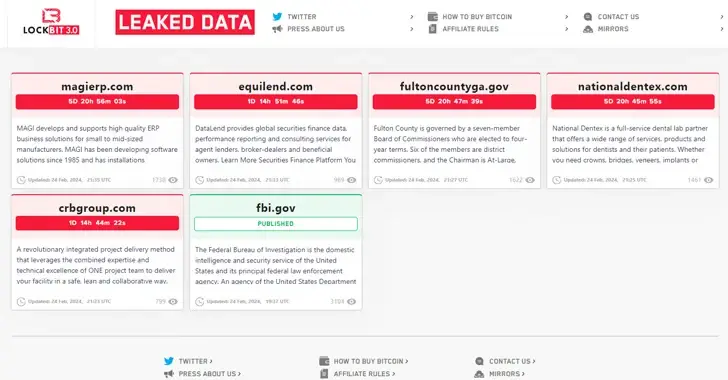
After being shut down by law enforcement, the LockBit ransomware group resurfaces.
Days after an international law enforcement exercise took control of its servers, the threat actors responsible for the LockBit ransomware operation have resurfaced on the dark web using new infrastructure. In order to achieve this, the infamous group relocated its data leak portal to a new TOR network address and has so far listed 12…

After a police disruption, LockBit ransomware returns and restores servers.
Less than a week after law enforcement hackers compromised their servers, the LockBit gang is resuming its ransomware operation on new infrastructure and has threatened to concentrate more of its attacks on the government. The gang published a lengthy message about their negligence in allowing the breach and the plans for the operation going forward…

A new technique to find stolen cookies has been patented by PayPal.
A novel technique that can detect when” super-cookie” is stolen has been submitted for patent by PayPal . This technique could enhance cookie-based authentication and reduce account takeover attacks. PayPal wants to take precautions against hackers stealing cookies containing authentication tokens and using two-factor authentication ( 2FA ) to access victim accounts without requiring valid credentials.…

RCMP is looking into a cyberattack because its website is down.
The national police force of Canada, the Royal Canadian Mounted Police (RCMP), has disclosed that its networks were recently the target of a cyberattack. In order to ascertain the extent of the security breach, the federal andnbsp body has begun its criminal investigation into the matter. No threat to Canadians ‘ safety and security, according…

Authorities assert that LockBit Admin ", LockbitSupp&quo, has cooperated with law enforcement.
Authorities claimed that LockBitSupp, the person( s ) responsible for the ransomware service’s persona on cybercrime forums like Exploit and XSS, “has engaged with law enforcement. “ The change occurred after the popular ransomware-as-service ( RaaS ) operation was shut down as part of a coordinated global operation known as Cronos. The criminals ‘ use…
