Your cart is currently empty!
Author: Omar
U. S. Offers$ 15 Million in Bounty to Find LockBit RansomwareLeaders
Up to$ 15 million in cash rewards have been announced by the U. S. State Department for information that could help identify important members of the LockBit ransomware group and result in their arrest. According to the State Department, LockBit actors have carried out more than 2, 000 attacks on victims worldwide and in the…
Lockbit is locked out, and funeral Facebook scams are discussed in the Smashing Security podcast# 360.
Heaven is above! Scammers are taking advantage of online funerals, and cybercops are stylishly dismantling Lockbit, the” Walmart of Ransomware. “ The most recent episode of Graham Cluley and Carole Theriault’s” Smashing Security” podcast covers all of this and more. Warning: There may be nuts, adult themes, and coarse language in this podcast. Hosts: @gcluley…

Joomla fixes XSS vulnerabilities that could make RCE attacks possible on websites.
The Joomla content management system has five vulnerabilities that could be used to program arbitrary code on websites that are vulnerable. Versions , 5.0.3 and 4.4.3 of the CMS have fixes, and the vendor has fixed the security problems that affect various Joomla versions. When a user’s MFA methods have been changed, CVE-2024-21722 does not properly…

After a May breach, Microsoft expands its free logging capabilities.
Six months after revealing that Chinese hackers stole U. S. government emails covertly during an Exchange Online breach between May and June 2023, Microsoft has increased free logging capabilities for all Purview Audit standard customers, including federal agencies in the United States. Since the incident was made public, the company has collaborated with CISA, OMB,…

Two vulnerabilities are raised by ConnectWise.
A security advisory for ConnectWise’s remote monitoring and management ( RMM) software was published on February 19, 2024. Two vulnerabilities that affect older ScreenConnect versions were identified by the advisory and fixed in version 23. 9. 8 and later. These vulnerabilities are classified as” Critical—Vulnerabilities that could allow the ability to execute remote code or…

Hackers run a massive banking Trojan campaign, abusing Google Cloud Run.
Hackers using the Google Cloud Run service to distribute enormous amounts of banking Trojans like Astaroth, Mekotio, and Ousaban are being warned by security researchers. Users can deploy frontend and backend services, websites, and applications using Google Cloud Run without having to worry about infrastructure management or scaling. Beginning in September 2023, Brazilian actors began…

iPhones worth more than $3 million were stolen from Apple
$3 million worth iPhone were stolen from Apple After being apprehended and found guilty of submitting more than 5,000 fake iPhones to Apple with the intention of having them replaced with real ones, two Chinese nationals now face 20 years in prison. Customers can return broken iPhones to Apple or authorized resellers for a replacement…
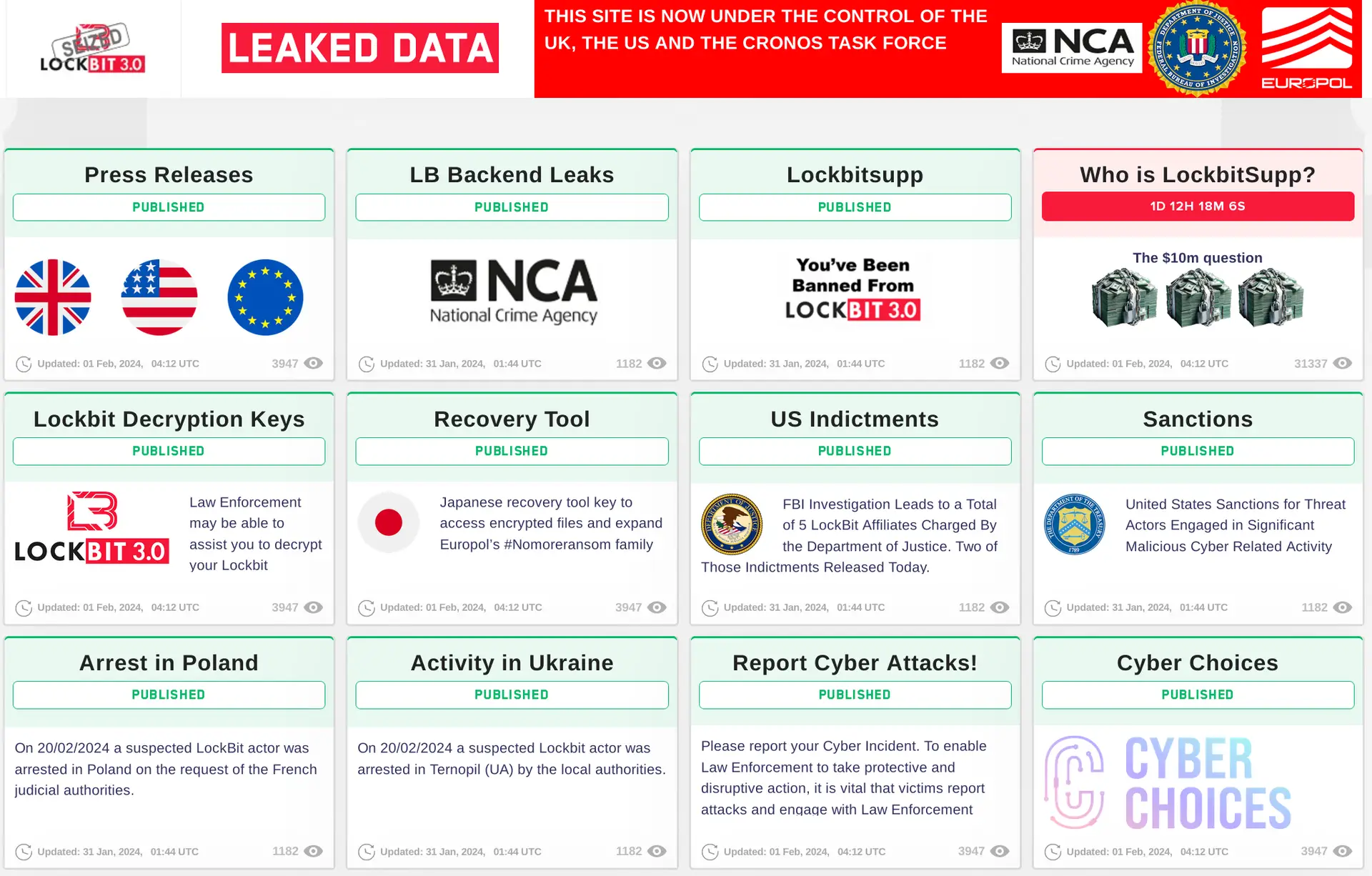
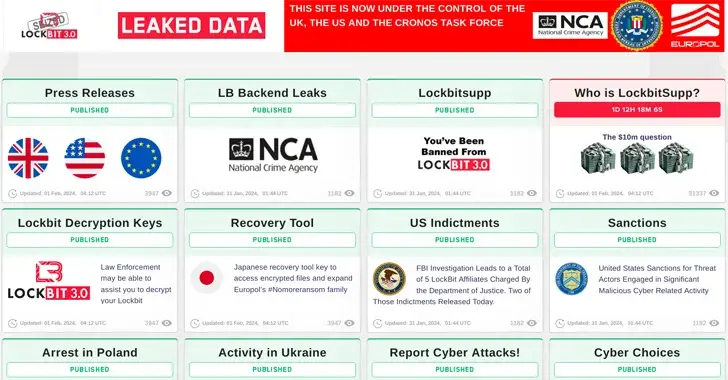
Lessons learned from winning the cybercrime war on LockBit
The National Crime Agency (NCA ) of the United Kingdom took control of LockBit’s main website late on February 19, 2024, making it the most active ransomware organization in recent memory. The NCA has taken control of the physical servers that run the main site and has detained two men—one in Poland and the other…

New SSH-Snake malware snatches the keys to the network and spreads it.
An open-source network mapping tool called  , SSH-Snake is being used by a threat actor to move laterally along the victim infrastructure while searching for hidden private keys. The Sysdig Threat Research Team ( TRT ) made the discovery of SSH-Snake, describing it as a” self-modifying worm” that distinguishes itself from more conventionally crafted attacks…

US government provides water utilities with cyberattack defense advice.
U. S. water utilities should take a number of defense measures, according to CISA, the FBI, and the Environmental Protection Agency ( EPA ), to better protect their systems from cyberattacks. The top eight steps U.S. Water and Wastewater Systems ( WWS ) sector organizations can take to lower cyberattack risks and strengthen their defenses…
