Your cart is currently empty!
Author: Omar

ScreenConnect bug under attack
As exploit code appears, a critical ScreenConnect bug is currently under attack. The two vulnerabilities ConnectWise disclosed earlier this week for ScreenConnect, its remote desktop and access software, have both technical information and proof-of-concept exploits available. Attackers began using the security flaws in attacks a day after the vendor made them public. The vendor identified…

LockBit ransomware gang $15 million bounty
For information on the LockBit ransomware gang, the US offers a$ 15 million bounty. Anyone who can provide information about LockBit ransomware gang members and their associates will now receive rewards of up to $15 million from the U. S. State Department. An additional $5 million is available for tips that could help identify or…

Hackers can access Android and Linux devices thanks to new Wi-Fi vulnerabilities.
NewsroomNetwork Security / Vulnerability as of February 21st, 2024 Open-source Wi-Fi software on Android, Linux, and ChromeOS devices has two authentication bypass flaws that could deceive users into joining malicious clones of legitimate networks or enable attackers to sign up for trusted networks without a password, according to cybersecurity researchers. Following a security assessment of…
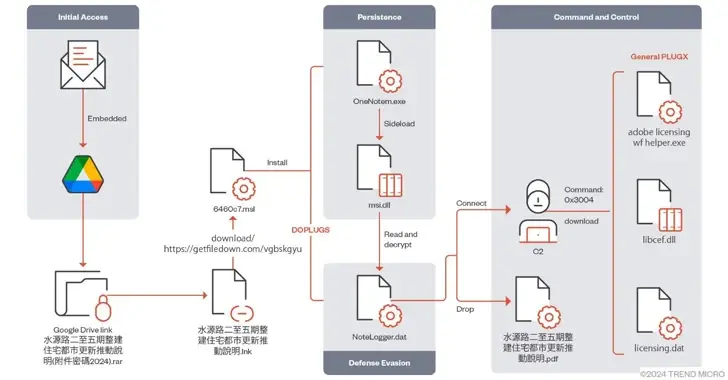
With the help of Advanced PlugX Variant DOPLUGS, Mustang Panda targets Asia.
21st of February 2024: Newsroom Malware/Cyber Espionage Using a variant of the PlugX ( also known as Korplug) backdoor called DOPLUGS, the China-linked threat actor Mustang Panda has attacked several Asian nations. According to Trend Micro researchers Sunny Lu and Pierre Lee, the customized version of PlugX malware differs from the general version, which includes…

AWS now offers SophosNDR.
All NDR and XDR/MDR customers can now use the Sophos RDR integration pack, which requires a log collector, in AWS AMI. For threat detection and response, Sophos NDR in AWS offers a number of benefits: what you receive Monitoring of cloud-native security: In AWS environments, native NDR sensors can now effectively provide visibility into network…
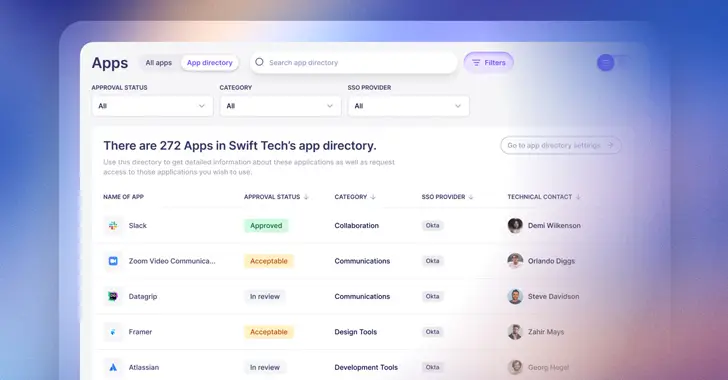
SaaS Identity Governance: 6 Simple Ways
Tasks related to identity governance must be carried out across a variety of different SaaS apps because they now account for the lion’s share of the technology used by employees in the majority of organizations. Centralized IT teams, who are ultimately in charge of managing and securing app access, face a significant challenge because they…

Healthcare Cybersecurity: Identifying the Threat Landscape and Preparing Recovery Solutions
While many Americans were celebrating Thanksgiving Day 2023, hospitals all over the country were doing the exact opposite. Systems were n’t working properly. There was a detour for ambulances. The care was hampered. When a ransomware attack hit hospitals in three states, the real-world consequences became apparent—not just computer networks were shut down, but actual…
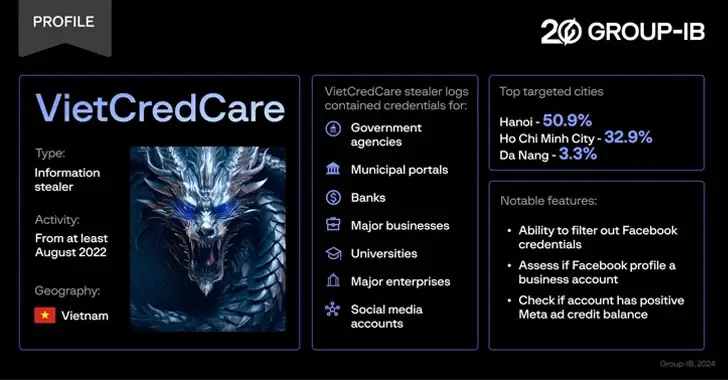
VietCredCare', a thief who targets Facebook advertisers in Vietnam, is new and number 39.
21st of February 2024: Malware/Cyber Threat in the Newsroom At least since August 2022, VietCredCare, a previously unidentified information stealer, has been targeting Facebook advertisers in Vietnam. According to a recent report published by Singapore-based Group-IB and distributed to The Hacker News, the malware is “notable for its ability to automatically filter out Facebook session…
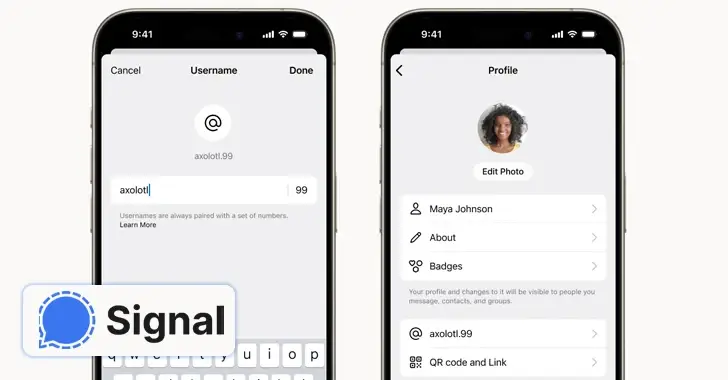
Users can keep their phone numbers private thanks to the signal that introduces usernames.
NewsroomSecure Communication / Anonymity on February 21st, 2024 Signal, an end-to-end encrypted ( E2EE ) messaging app, announced that it is testing out a new feature that enables users to create distinctive usernames ( not to be confused with profile names ) and hide their phone numbers from prying eyes. Your phone number wo n’t…
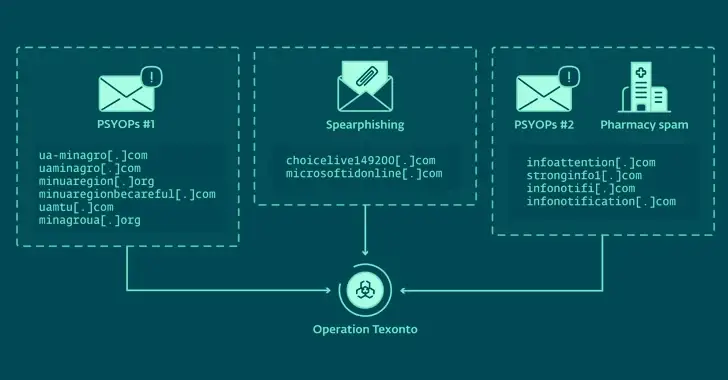
With false information and credential-healing attacks, Russian hackers target Ukraine.
NewsroomPhishing Attack / Information Warfare, February 21, 2024 A new influence operation that uses spam emails to spread war-related misinformation has been discovered by cybersecurity researchers and is aimed at Ukraine. The Slovak cybersecurity company ESET, which also identified a spear-phishing campaign in October 2023 and another European Union agency in November 20, with the…
