Your cart is currently empty!
Author: Omar

Release notes for NordVPN for MacOS
( Direct download ) Threat Protection has made browling easier and more enjoyable. No more obtrusive blocks on your favorite websites thanks to our improved web monitoring mechanism. Knowing that our watchful guardian keeps you safe, surf in freedom! ( App Store + Direct Download ) To improve the functionality of the NordVPN app for…

Installing Ivanti Vulnerability and using DSLog and# 039, Backdoor on 670+ ITInfrastructures
13 February 2024 Newsroom Vulnerability/CyberThreat Threat actors are using a backdoor code called DSLog to target vulnerable devices by using the recently discovered security flaw that affects ZTA gateways, Ivanti Connect Secure, and Policy Secure. That is consistent with Orange Cyberdefense’s findings, which claimed to have seen CVE-2024-21893 exploited just hours after the proof-the-concept (…

Alert: Roundcube and# 039, CISA Warns of Active &, and Email Attacks: Patch Now
13 February 2024: Email Security / Newsroom Vulnerability Based on evidence of active exploitation, the United States Cybersecurity and Infrastructure Security Agency ( CISA ) added a medium-severity security flaw affecting Roundcube email software to its Known Exploited Vulnerabilities (KEV ) catalog on Monday. The problem, which is identified as CVE-2023-43770 ( CVSS score: 6.1…

Ransomware attacks on IT service providers severely affected 20+ hospitals in Romania.
According to reports, a ransomware attack on more than 20 Bucharest hospitals resulted from cybercriminals targeting an IT service provider. As a result, medical professionals are now required to use pen and paper rather than computers. The Backmydata ransomware, a subset of Phobos, was used by the attackers to encrypted hospital data, according to the…

Contracts due February 12, 2024
ARMY Alberici Constructors Inc. , St. Louis, Missouri ( W9127S- 24- D- 0001 ), J. F. Brennan Co. Inc. , La Crosse, Wisconsin ( W9127S- 24- D- 0002 ), Johnson Bros. Corp. , A Southland Holdings Inc. Co. , Grapevine, Texas ( W9127S- 24- D- 0003 ), Massman Construction Co. , Overland Park, Kansas (…

Safe, Secure, and Reliable AI
ExecBrief from PinnacleOne: Safe, Secure, and Reliable AI The PinnacleOne Executive Brief has been re-launched. The P1 ExecBrief offers actionable insights on significant developments spanning geopolitics, cybersecurity, strategic technology, and related policy dynamics. It is designed for corporate executives and senior leadership in roles in risk, strategy, or security. SentinelOne’s response to the Executive Order…
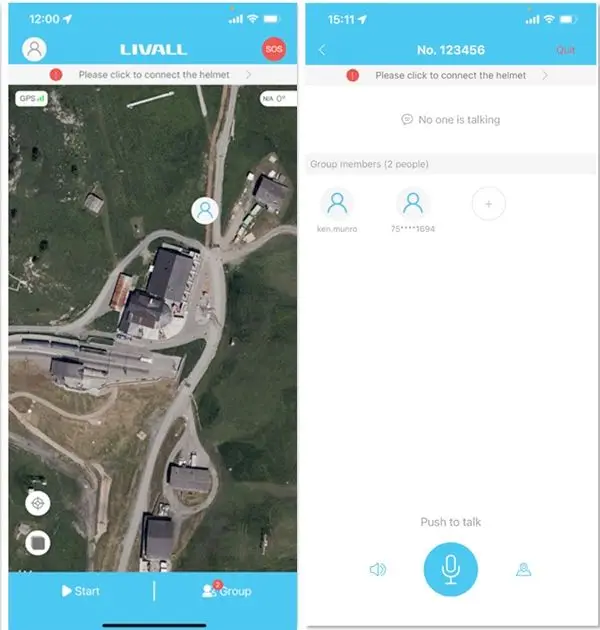
Location tracking and privacy risks are exposed by the” Smart” helmet flaw.
It sounds like a good idea to get fans who enjoy biking and skiing to wear smart helmets. Protect your head and maintain contact with your group if you’re on slopes or trails. Because of this, Livall, a well-known ski and bike helmet manufacturer, is likely to have created” smart” lines of products with “walkie-talkies”…
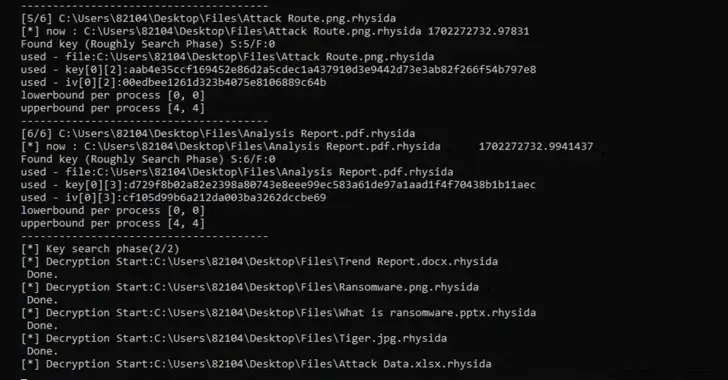
Free decryption tool released after Rhysida ransomware was cracked
Data recovery and vulnerability in the newsroom on February 12, 2024 Researchers studying cybersecurity have discovered an “implementation vulnerability” that allows for the reconstruction of encryption keys and the decryption of Rhysida ransomware-protected data. Researchers from Kookmin University and the Korea Internet and Security Agency (KISA ) released their findings last week. We were able…

4 Ways Hackers Get Around MFAs Bypassing Social Engineering
Hackers Bypassing MFA One suggestion that stands out above the rest in terms of access security is multi-factor authentication ( MFA ). Since hackers can easily crack passwords on their own, MFA offers a crucial layer of defense against breaches. It’s crucial to keep in mind that MFA is not impenetrable. It is frequently possible…

Package Repository Security Release Framework by CISA and OpenSSF
The Hacker NewsInfrastructure Security / Software Supply Chain as of February 12, 2024 A new framework to secure package repositories will be published by the U.S. Cybersecurity and Infrastructure Security Agency ( CISA ) in collaboration with the Open Source Security Foundation ( OSF ) Securing Software Repositories Working Group. The framework, known as the…
