Your cart is currently empty!
Author: Omar
-

How do you exclude yourself from Instagram? Everything that a person must know
How does Instagram work? Sending money is free, or Instagram is your “preço.” For many people, this price represents a significant impact on their mental or physical well-being, leading to the accumulation of negative social effects. Among the many reasons that led us to give up on a platform, let’s look at these: Forte sensazione…
-

What is the service-based PaaS platform?
What does “platform as a service” mean? A third party ( a PaaS provider ) assists with a company’s application development by giving them the hardware and software necessary to do so under the cloud computing model known as “platform asa service.” Cloud solutions are frequently offered as a service to other businesses by PaaS…
-

How to avoid common password attacks and vulnerabilities
A password attack is what? Any attempt by an attacker to create or steal passwords in order to access private information and other user accounts is referred to as a password attack. Simple techniques like figuring out passwords based on frequently used phrases are just one approach, but sophisticated attacks can produce thousands of them.…
-
Is it really anonymous or can you be followed with a VPN?
What does a VPN do to completely anonymize me? No, there is n’t a VPN that is completely anonymous. Every internet user leaves behind a trail during their navigation that can be followed all the way to the end of their search, as well as through marketing or even surveillance. However, a VPN increases your…
-

A replay attack is what?
A replay attack is what? When an attacker intercepts two parties ‘ network communications to delay, redirect, or repeat them, they are said to have launched a replay attack. The cybercriminal then retransmits traffic while posing as one of the legitimate parties in order to mimic or control the initial action. What is the process…
-

Safer Internet
The importance of Safer Internet Day has not changed While the benefits of the Internet are numerous and widespread, we must all take precautions to protect ourselves and our valuable personal information while using it. The Internet has become a ubiquitous part of daily life. Without the proper safety precautions to make sure you’re safe…
-
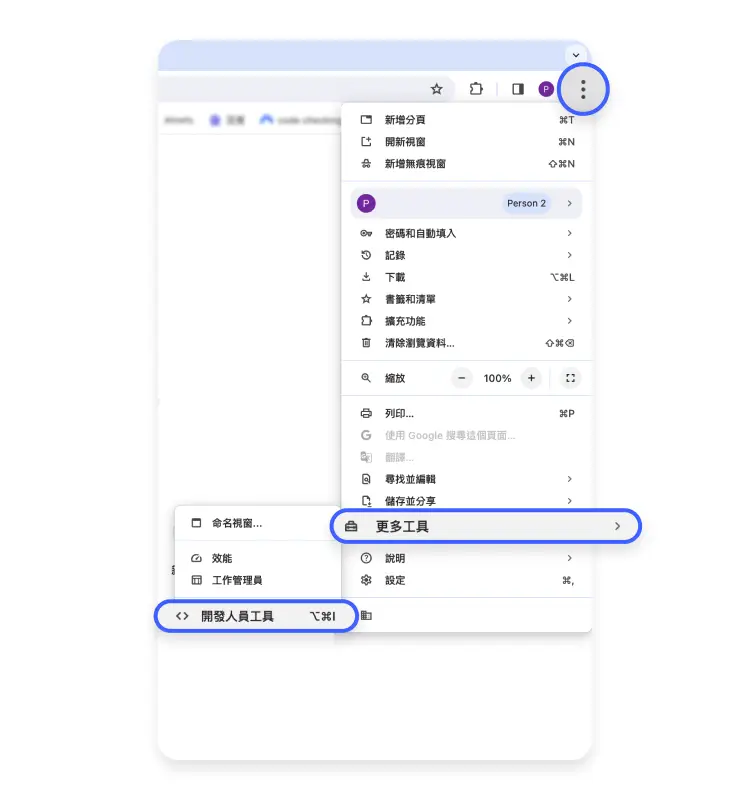
Google Chrome
Google Chrome Google Chrome is used. Google Chrome: 按下瀏覽器右上角的三點圖示。 前往「更多工具」>「開發人員工具」。 選擇「Sensors」(感測器)分頁。 如果沒有看到該頁籤,請按一下右上角的三點圖示,將鼠標懸停在「更多工具」,然後按一下「Sensors」。 按一下「Location」(位置)旁的下拉選單,選擇其中一個可用選項。 Manage ( ), >, Add location ( ). ,…. Google is the source. Google Chrome ” Chrome,””. .: 按下瀏覽器右上角的三點圖示。 前往「更多工具」>「開發人員工具」。 選擇「Sensors」頁籤。 按一下「Location」旁的下拉選單,然後選取「Other」(其他)。 輸入任意經度和緯度。 Google Chrome ,…. Google Chrome ( ): 在瀏覽器的右上角,按一下三點圖示,然後選取「設定」。 選取左側選單中的「隱私權和安全性」,然後點選「網站設定」。 然後於權限欄位下方選擇「位置」。 如在「預設行為」下方,選取「禁止網站查看你的位置資訊」。 值得注意的是,一旦您更改此設定,需要位置資訊的功能將無法運作。 Chrome Chrome NordVPN Chrome version of NordVPN.…
-

Contracts for February 5, 2024
ARMY A contract for M872A4 semi-trailers and related items valued at$ 155, 171, 315 fixed price with economic price adjustment was awarded to Talbert Manufacturing Inc. , * Rensselaer, Indiana. One bid was accepted after being solicited online. Each order will have a work location and funding choice, and it is anticipated that it will…
-

IEEE Conference on Synthetic Aperture Computational Imaging ( 2024 )
Automotive, mmWave, THz, Polarimetric, ISAR, 3D imaging, and high-dimensional feature processing using tensors are some of the radars. Sonar: Bathymetry, wideband regimes, micronavigation and position uncertainty Optics include deep learning techniques, ptychography, hohographs, coded aperture imaging, wiretinger flow, and phase retrieval imaging. 5G: Near-field beam focusing, channel sounding, over-the-air calibration, MIMO antenna testbeds, intelligent reflecting…
-

Welcome to Cloud Native Security: Blocking Attacks with an AI-Powered CNAPP!
It’s a thrilling day today. We declared that PingSafe has now been fully acquired by us. I wanted to use this chance to describe our journey forward because PingSafe is a key component of SentinelOne’s cloud security future. I’ll go into more detail about how and why cloud security is frequently the most difficult aspect…
