Your cart is currently empty!
Author: Omar

Insights into the State of Cyber Threats
Cybersecurity treats We understand that the threat of cyberattacks is becoming increasingly prevalent in today’s digital age, and as such, it is important to stay informed and take necessary measures to protect ourselves and our businesses. The current landscape of cyber threats is complex, with attackers utilizing sophisticated techniques to exploit vulnerabilities and gain access…
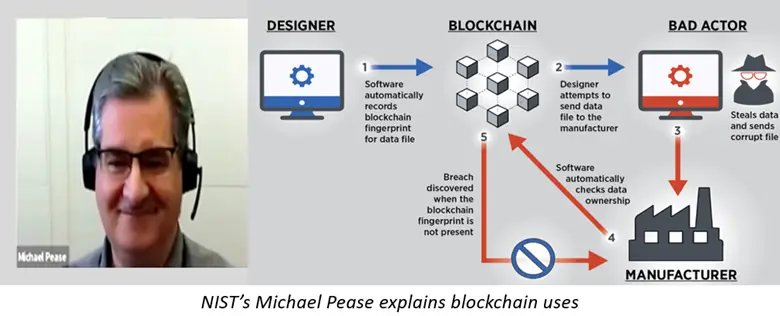
NIST researcher discusses blockchain applications, ideas, and potential future research on the panel.
The Blockchain Use Case Summit was held by the American Council for Technology-Industry Advisory Council in January 2023. In its panel, NIST researcher Michael Pease discussed” Operationalizing, Blockchain: Manufacturing, Supply Chains, Stablecoins and Security. “ Blockchain and Related Technologies to Support Manufacturing Supply Chain Traceability: Needs and Industry Perspectives, NIST Internal Report 8419, was reviewed…
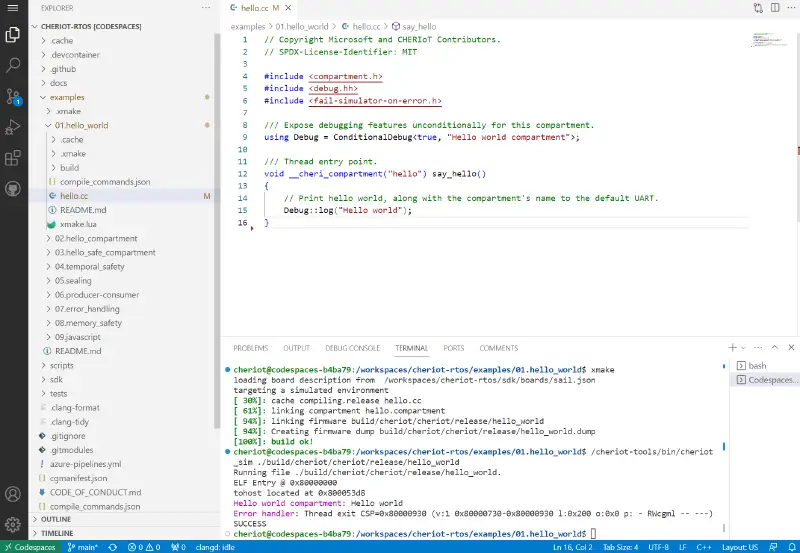
CHERIoT Security Research’s initial steps
In our quest for memory safety, Microsoft spends a lot of time researching and looking into potential solutions. The task of safeguarding legacy code is crucial because the vast majority of existing codebases are written in dangerous programming languages. Compared to purely software solutions, hardware solutions are more appealing because they offer very strong security…

Defending Against Ransomware
Insights into the State of Cyber Threats Researchers connect Conti, Royal cybercrime gangs, and 3AM ransomware Defender Exploit Guard Moving Beyond EMET II Home of CyberSecurity and Compliance Akira Ransomware Exploiting Cisco ASA/FTD Vulnerability, CISAWarning

Office 365 BitLocker and Distributed Key
Office 365 BitLocker and Distributed Key Manager for Encryption Encryption is a critical aspect of data protection for any organization, and Microsoft Office 365 offers several built-in encryption options. However, one of the most robust and flexible options available is the combination of BitLocker and Distributed Key Manager (DKM). This guide will provide a detailed…
Achieving FIPS 140-2 Validation
Learn why IDShield offers the best security and value. The Ultimate Guide to FIPS 140-2 Validation: Security, Windows, and Best Practices FIPS 140-2, a standard established by the National Institute of Standards and Technology (NIST), provides a stringent set of requirements for ensuring robust cryptographic capabilities within IT systems. This blog explores the fundamentals of…

Data backup strategies for virtualization and cloud environments
Implementing effective data backup strategies is crucial for businesses that use virtualization and cloud technologies to prevent data loss and downtime in case of a disaster. In virtualized environments, multiple virtual machines (VMs) run on a single physical host, which could add complexity to backup data. In addition, cloud environments are typically distributed across multiple…

Ransomware Threats
Ransomware -Understanding Threats and Protecting Organization Ransomware is a rapidly growing cyber threat, costing businesses millions of dollars annually. This malicious software encrypts the files on a victim’s computer or an entire organization network and demands payment for the decryption key. Sadly, paying a ransom does not guarantee that the victim will regain access to…
What is CDI?
What is Covered Defense Information (CDI)? Covered Defense Information (CDI) is a broad category that encompasses a wide range of information related to national defense. It can include (for example), classified and unclassified data and information controlled for other reasons, such as export control regulations. Some examples of CDI include: CDI protection is governed by…
What is CUI?
What is Controlled Unclassified Information (CUI)? Controlled Unclassified Information (CUI) refers to sensitive or confidential information that is not classified by the government but still requires protection due to its nature. This type of information is typically not as sensitive as controlled information, but it still needs protection to ensure it is not released to…
