Your cart is currently empty!
Author: Omar

Spotify is held accountable by Apple for a$ 1. 95 billion fine over ", abusive", App store regulations.
The European Commission has fined Apple €1. 8 billion, or approximately$ 1. 95 million, for allegedly abusing its market dominance in music streaming app distribution to prevent developers from promoting cheaper services outside the app. ” The European Commission has fined Apple over €1.8 billion for abusing its dominant position on the market for the…

According to claims that they stole$ 22 million in ransom, BlackCat ransomware shuts down servers.
The ALPHV/BlackCat ransomware gang has shut down its servers amid claims that they scammed the affiliate responsible for the attack on Optum, the operator of the Change Healthcare platform, of $22 million. While BlackCat’s data leak blog has been down since Friday, BleepingComputer had confirmed that negotiation sites were still active over the weekend. Today, BleepingComputer…

Russia’s Ministry of Defense servers were allegedly hacked, according to Ukraine.
According to the Ukrainian Ministry of Defense’s Main Intelligence Directorate ( GUR), it allegedly stole sensitive documents from the Russian Ministry of Defense’s ( Minoborony ) servers. The attack is described as a” special operation” carried out by GUR’s cyber-skills, according to a press release released today on an official Ukrainian government domain. The GUR…

To steal engineering data, North Korea hacks two South Korean chip companies.
The National Intelligence Service ( NIS ) in South Korea warns that North Korean hackers target domestic semiconductor manufacturers in cyber espionage attacks. NIS says these attacks increased in the second half of 2023 until recently, targeting internet- exposed servers vulnerable to known flaws for initial access to corporate networks. Once the network was breached,…

How Money Laundering Operations in India are being abused by cybercriminals.
Cybercriminals are using a network of hired money mules in India using an Android-based application to orchestrate a massive money laundering scheme. The malicious application, called XHelper, is a “key tool for onboarding and managing these money mules,” CloudSEK researchers Sparsh Kulshrestha, Abhishek Mathew, and Santripti Bhujel said in a report. Details about the scam…

Credit cards from American Express are the subject of a data breach by a third party.
3/4/24: Article updated with further clarification from American Express that it was a merchant processor who was hacked, not one of their service providers. American Express is warning customers that credit cards were exposed in a third- party data breach after a merchant processor was hacked. This incident was not caused by a data breach…

Credit cards from American Express are the subject of a vendor data breach.
 , American Express is warning customers that credit cards were exposed in a third- party data breach after one of its service providers was hacked. In a data breach notification filed with the state of Massachusetts, American Express said that the breach occurred at one of its service providers used by their travel services division,…

From 500 to 5000 employees, ensuring the use of third-party apps in mid-market businesses.
Mar 04, 2024The Hacker NewsSaaS Security / Vulnerability Assessment A company’s lifecycle stage, size, and state have a significant impact on its security needs, policies, and priorities. This is particularly true for modern mid-market companies that are either experiencing or have experienced rapid growth. As requirements and tasks continue to accumulate and malicious actors remain…
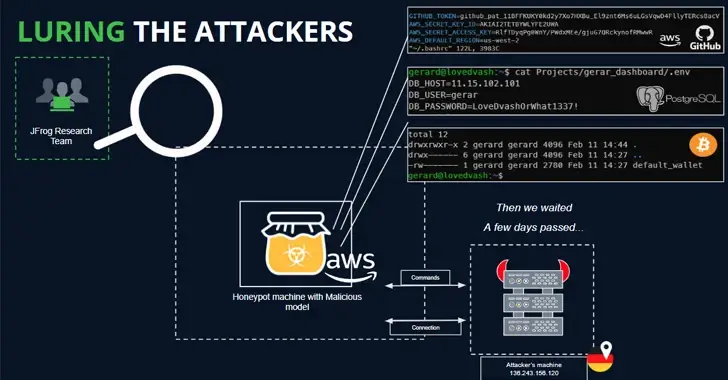
On the Hugging Face platform, there are more than 100 malicious AI/ML models.
Mar 04, 2024NewsroomAI Security / Vulnerability As many as 100 malicious artificial intelligence (AI)/machine learning (ML) models have been discovered in the Hugging Face platform. These include instances where loading a pickle file leads to code execution, software supply chain security firm JFrog said. “The model’s payload grants the attacker a shell on the compromised…

SSL Explained: A Guide to Protecting Your Website and User Data
SSL Certificates Explained: A Guide to Protecting Your Website Data & Understanding Cybersecurity In today’s digital landscape, cybersecurity is paramount, and protecting your website’s data and visitors’ information is more critical than ever. SSL (Secure Sockets Layer) and its successor, TLS (Transport Layer Security), are essential components of your cybersecurity toolkit. Let’s dive into SSL/TLS…
