Your cart is currently empty!
Author: Omar
-
announcing the MICO ( Microsoft Machine Learning Membership Inference Competition )
A new competition focusing on machine learning ( ML) systems ‘ security and privacy has just been announced, and we are thrilled to announce it. Many goods and services already heavily rely on machine learning, and this trend is likely to continue. Understanding the security and privacy protections offered by cutting-edge ML algorithms is therefore…
-
What CHERI variety is the smallest?
Microsoft Research Cambridge, Microsoft Security Response Center, and Azure Silicon Engineering &, Solutions collaborated on the Portmeirion project. We have been looking into how to scale the major concepts from CHERI down to the smallest cores using the most affordable microcontrollers over the past year. The desktop and server-class processors that have been the Morello…
-
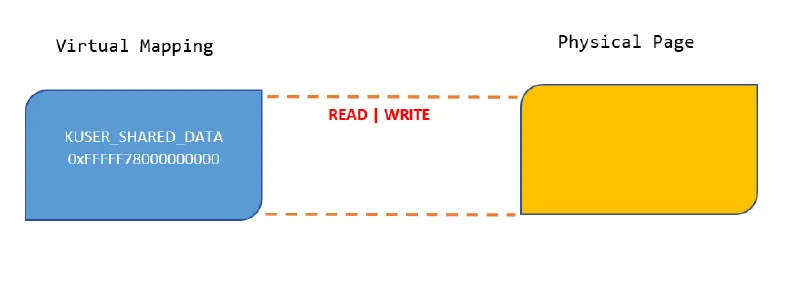
Windows KUSER_SHARED_DATA Structure Randomization
Kernel Address Space Layout Randomization (KASLR ) has been improved significantly by Windows 10, which raises the price of exploitation, especially for remote code execution exploits. There are numerous kernel virtual address space (VAS ) locations, such as system PTEs, pools, and kernel stacks. are chosen randomly. The KUSER_SHARED_DATA structure, a page of memory that…
-
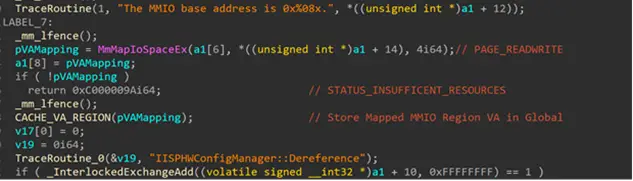
Investigating a New Kernel Exploit Primitive Class
Attack surfaces change as a result of the dynamic and frequently changing security landscape. Numerous cases involving various products, bug types, and exploit primitives are received by MSRC. An arbitrary kernel pointer read is one of the most intriguing primitives we observe. These frequently occur when kernel mode code fails to verify that pointers read…
-

Exploring the Morello Prototype
A Leap Towards Advanced Memory Safety Arm is at the forefront of innovation, shipping a limited number of demonstration boards featuring the first silicon for the Morello prototype architecture. This initiative is a collaborative effort involving industry giants like Arm, Microsoft, and the University of Cambridge, aiming to revolutionize hardware security through the Morello project.…
-
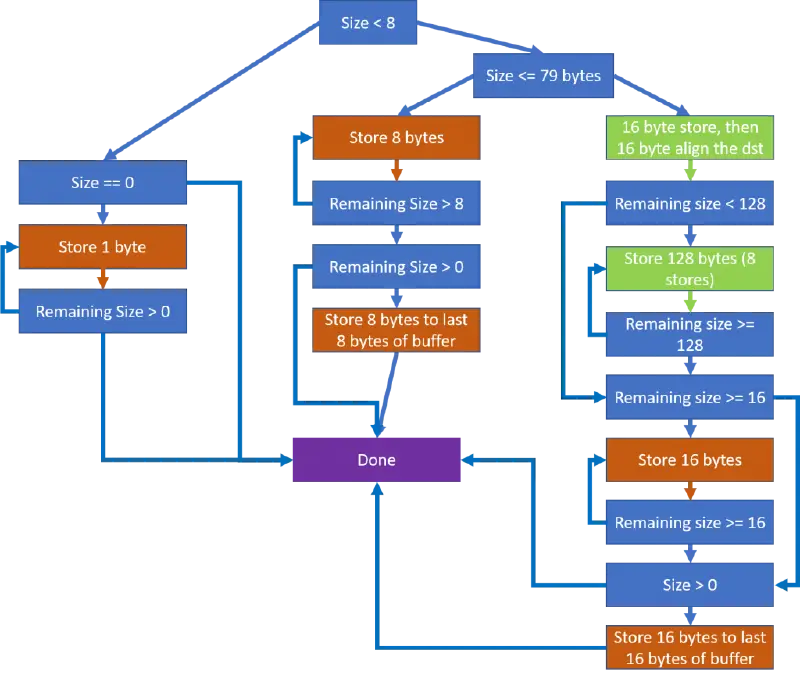
Building FasterAMD 64
Memset Routines for Building FasterAMD 64 Over the past several years, Microsoft has rolled out several changes that result in more memory being zeroed. These mitigations include: The InitAll mitigation which zeros most stack variables Switching most Microsoft kernel code over to the ExAllocatePool2/ExAllocatePool3 API’s which zero memory by default. Where possible the compiler will…
-
CHERI ISA Security Analysis
Is it possible to reach a point where memory safety concerns are definitively reduced? We looked at CHERI ( Capability Hardware Enhanced RISC Instructions ), which offers memory protection features against numerous exploited vulnerabilities, or an architectural solution that breaks exploits, in our effort to reduce memory corruption vulnerabilities. We have considered additional mitigations to…
-
Rust and Clang/LLVM Control Flow Guard
We’re happy to announce that the Clang C/C++ compiler and Rust now support Windows Control Flow Guard ( CFG ) as part of our ongoing efforts to program safer systems. Control Flow Guard: What Is It? A platform security technology called CFG is intended to uphold the integrity of the control flow. Since Windows 8.1,…
-

Uninitialized Kernel Pool Memory on Windows: A Solution
This blog post describes Microsoft’s efforts to remove Windows ‘ uninitialized kernel pool memory vulnerabilities as well as our motivations. Please refer to our previous blog post for more information on the benefits of uninitialized memory and the solutions that have been used in the past to address this problem. In a nutshell, less than…
-
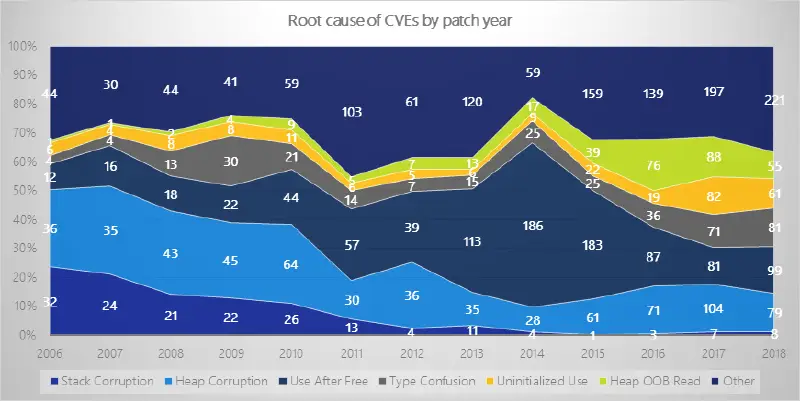
Uninitialized Stack Memory
Uninitialized Stack Memory on Windows This blog post outlines the work that Microsoft is doing to eliminate uninitialized stack memory vulnerabilities from Windows and why we’re on this path. This blog post will be broken down into a few parts that folks can jump to: Uninitialized Memory Background Potential Solutions to Uninitialized Memory Vulnerabilities InitAll…
