Your cart is currently empty!
Author: Omar
Rust and Kubernetes
Rust and Kubernetes in the Safety Boat The popular open-source container management tool Kubernetes is used to run WebAssembly modules, and our team at DeisLabs recently released a new piece of software called Krustlet. Kubernetes, which is primarily written in the Go programming language, is widely used to run cloud software across numerous vendors and…
Using Windows ‘ Rust
Ryan Levick and Sebastian Fernandez, two Microsoft engineers, will give a keynote address at RustFest Barcelona on Saturday, November 9. They’ll discuss the reasons Microsoft is looking into implementing Rust, some of the difficulties we’ve encountered, and Microsoft’s plans for the future. Attend the keynote and speak with Ryan and Sebastian afterward if you want…
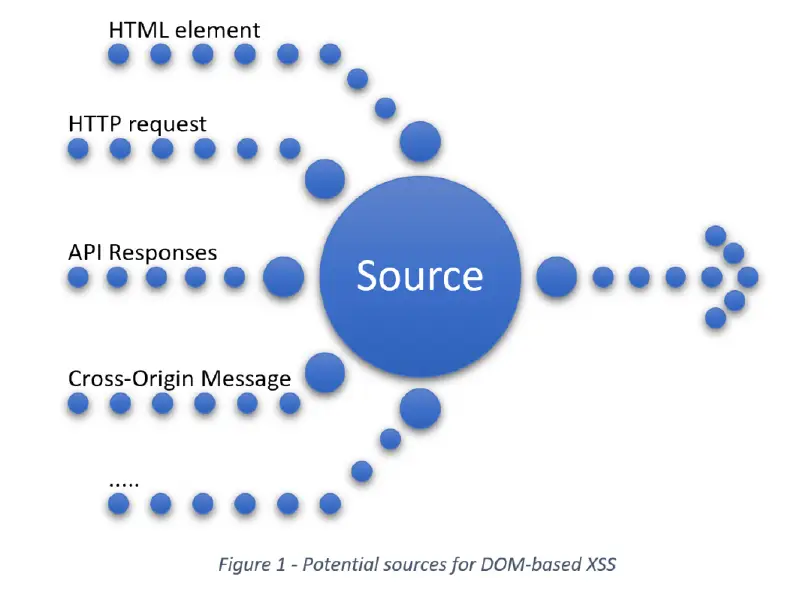
Semmle QL: DOM XSS vulnerability hunting
In two previous blog posts ( part 1 and part 2), we talked about using Semmle QL in C and C++ codebases to find vulnerabilities such as integer overflow, path traversal, and those leading to memory corruption. In this post, we will explore applying Semmle QL to web security by hunting for one of the…
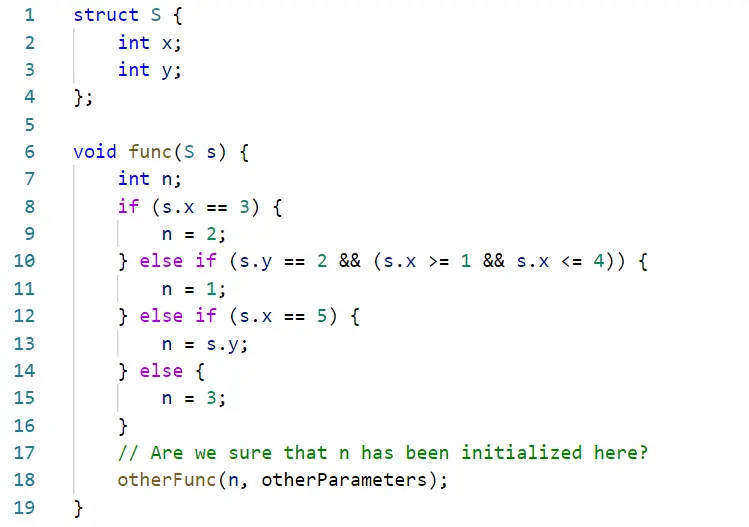
Having worked as an intern and# 039 with Rust
As described in this blog, I worked with the Safe Systems Programming Languages ( SSPL) team during my internship at the Microsoft Security Response Center ( MSRC ) to promote safer languages for systems programming where runtime overhead is crucial. In order to fix the memory safety bugs that had been plaguing Rust, I had…
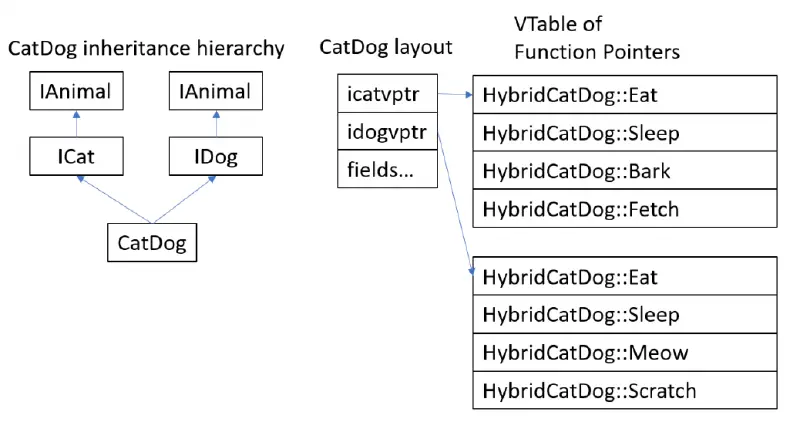
creating a Rust COM library
This past summer, I worked as a software engineering intern for Microsoft in Cheltenham’s MSRC UK team. As a preventative measure against memory-safety-related vulnerabilities, I worked for the Safe Systems Programming Language ( SSPL) group, which investigates safe programming languages. The project I’ve been working on while being mentored by the SSPL team is described…
Rust is being used to create the Azure IoT Edge Security Daemon.
The Azure IoT Edge open source, cross-platform software project from Microsoft’s Azure IT team aims to address the issue of managing compute distribution from the cloud to the edge of your on-premise network. The selection of Rust as the product’s implementation programming language for the Security Daemon component is explained in some detail in this…
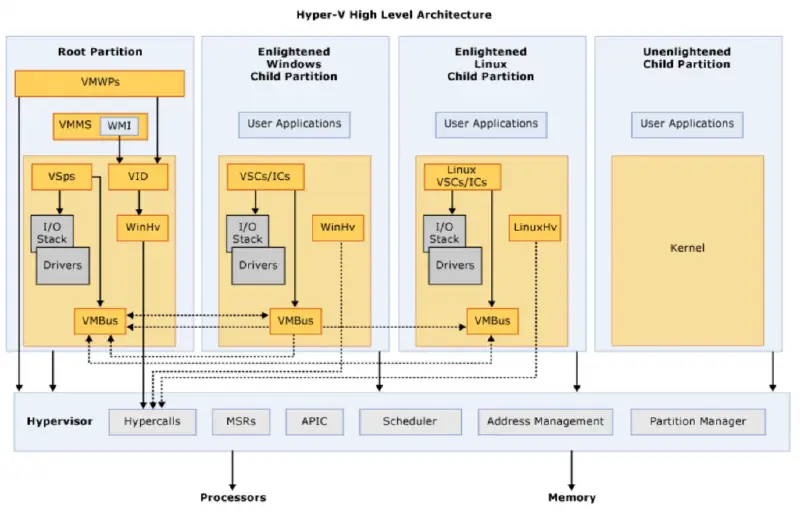
The VM Worker Process is Attacked
We spent a lot of time in the previous year improving everyone’s access to Hyper-V research. First Steps in Hyper-V Research, our first blog post, examines the intriguing attack surfaces of the virtualization stack components and describes the tools and setup for debugging the hypervisor. The focus of our friends at the Virtualization Security Team…
obtaining an investigative VHD
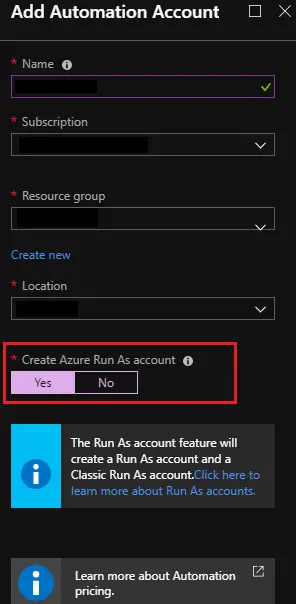
In a previous post, we discussed some of the differences between on-premises/physical forensics, cyber investigations, and cloud-based investigations and how they can be difficult. You can quickly deploy this pre-prepared machine to be used in an investigation thanks to the method described in that blog post for creating and maintaining a VM image that can…
Investigative incident response
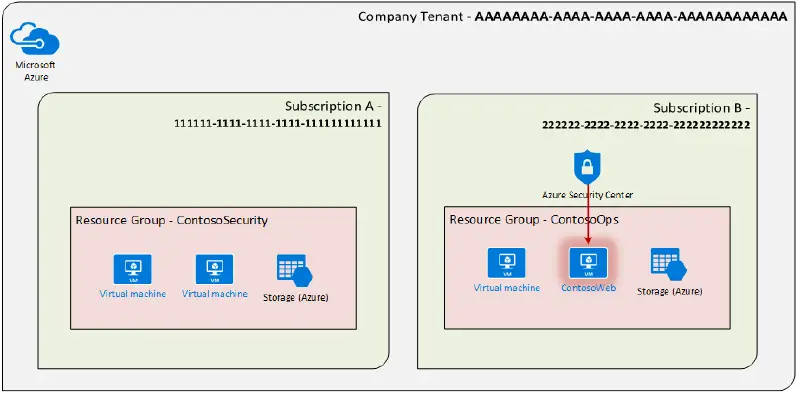
Investigative and incident response scalable infrastructure Traditional computer forensics and cyber investigations are just as applicable in the cloud as they are in physical locations, but access to and execution of these investigations varies. This article will outline some of the difficulties associated with implementing on-premises forensics techniques in the cloud and demonstrate an Azure-based…
Corporate Internet of Things ( IoT ): an entry point
According to a number of sources, 50 billion IoT devices will be used globally by 2020. Many Internet of Things ( IoT ) devices simply connect to the internet with little management or oversight, despite the fact that many of them are built with a network connection in mind. Security teams must still be able…
