Your cart is currently empty!
Author: Omar
-
Why use Rust to program safe systems?
In this series, we’ve looked at the need for preventative action to fix a group of vulnerabilities and discussed some Microsoft code examples of memory safety problems that could have been avoided. We’ll now take a look at why, in our opinion, Rust is the best C and C++ substitute currently on the market. First…
-

Safer programming language
A safer systems programming language is required We talked about the necessity of proactively addressing memory safety issues in our first post of this series. Memory safety concerns have been assigned to a CVE for almost the same percentage of vulnerabilities for more than ten years, despite the fact that tools and guidance are clearly…
-
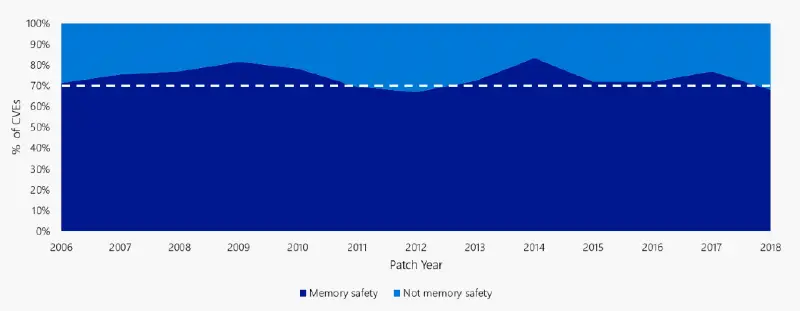
a proactive strategy for safer code
What if we were able to completely eliminate a class of vulnerabilities? The Microsoft Security Response Center ( MSRC ) has evaluated each Microsoft security vulnerability that has been reported since 2004. One startling fact stands out from all of that triage: according to Matt Miller’s 2019 BlueHat IL presentation, developers unintentionally add memory corruption…
-
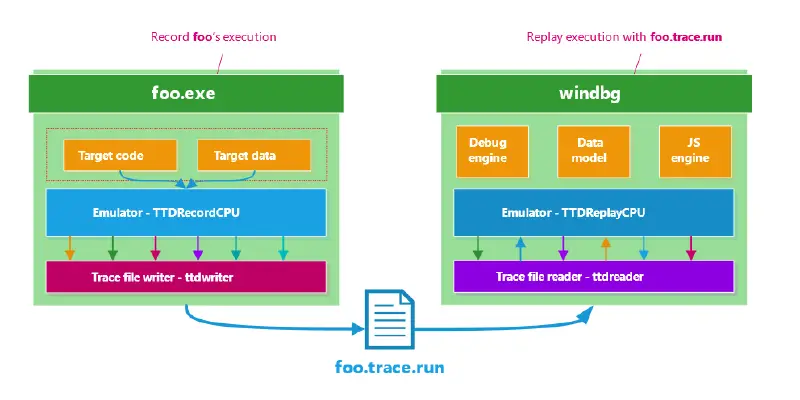
It’s a blast to debug time travel! ( from the past )
The Microsoft Security Response Center (MSRC) works to assess vulnerabilities that are externally reported to us as quickly as possible, but time can be lost if we have to confirm details of the repro steps or environment with the researcher to reproduce the vulnerability. Microsoft has made our “Time Travel Debugging” (TTD) tool publicly available…
-
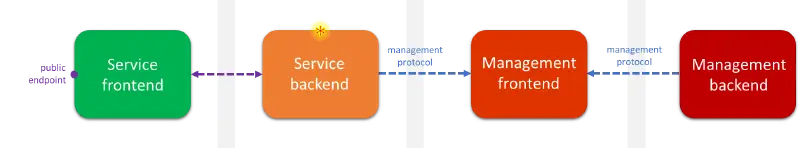
Part 2 of Semmle QL’s vulnerability hunting
Semmle QL and the Microsoft Security Response Center’s ( MSRC ) use of it to look into different types of vulnerabilities that have been reported to us were discussed in the first part of this series. This article covers a security audit of an Azure firmware component as an illustration of how we’ve been proactively…
-
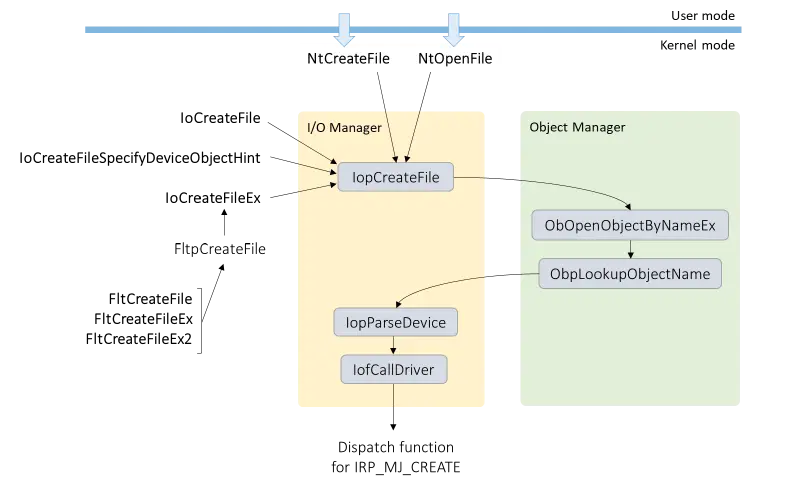
Local privilege escalation through Windows I/O Manager: a different collaboration
To improve the security of our customers and the entire online community, the Microsoft Security Response Center ( MSRC ) looks into all reports of security flaws affecting Microsoft products and services. We value the excellent vulnerability research that the security community regularly reports to us and view working with these researchers as an honor.…
-
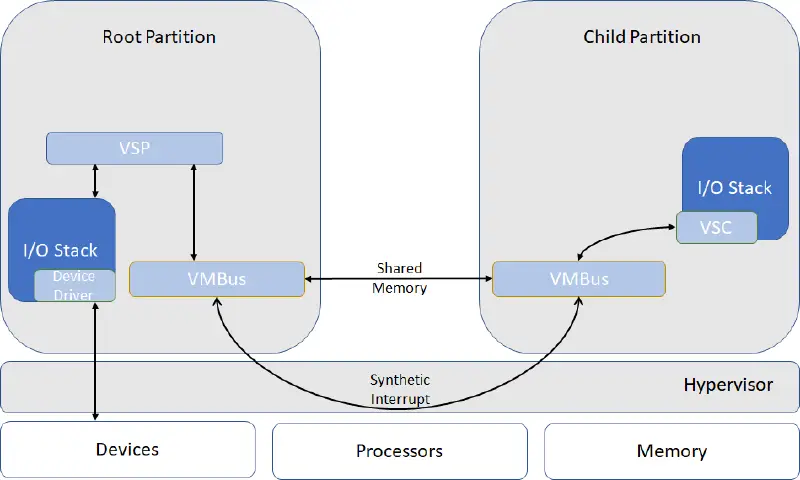
Hyper-V fuzzing para-virtualized devices
Introduction Hyper-V is the backbone of Azure, running on its Hosts to provide efficient and fair sharing of resources, but also isolation. That’s why we, in the vulnerability research team for Windows, have been working in the background for years now helping secure Hyper-V. And why Microsoft invites security researchers across the globe to submit…
-
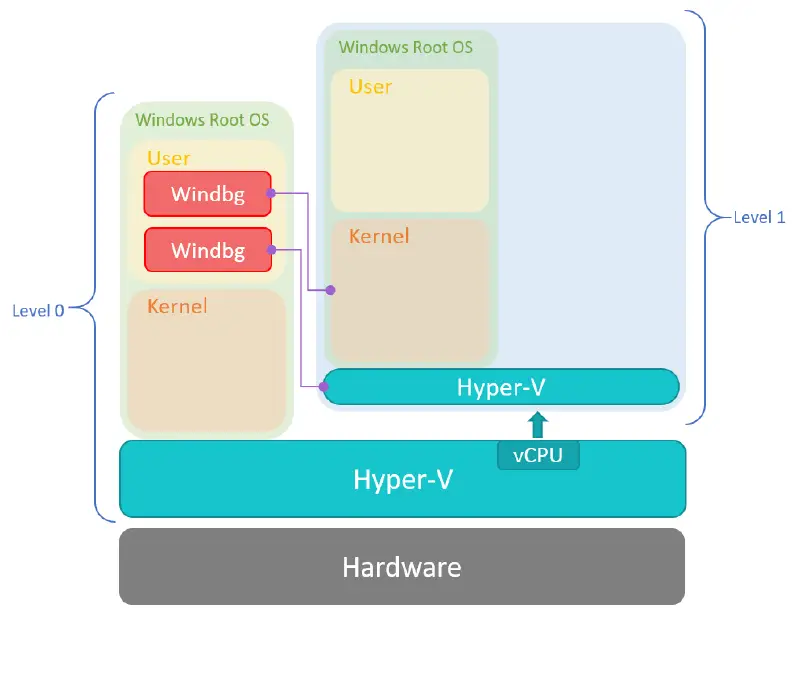
Initial Steps in Hyper-V Research
Microsoft has put a lot of effort in Hyper-V security. Hyper-V, and the whole virtualization stack, runs at the core of many of our products: cloud computing, Windows Defender Application Guard, and technology built on top of Virtualization Based Security (VBS). Because Hyper-V is critical to so much of what we do, we want to…
-
Windows Security Servicing Criteria
Being more open and honest with security researchers and our customers about the standards we use to decide when to address a reported vulnerability through e-security updates is one of our objectives at the Microsoft Security Response Center ( MSRC ). As the threat landscape changes over time, we think that increasing transparency on this…
-
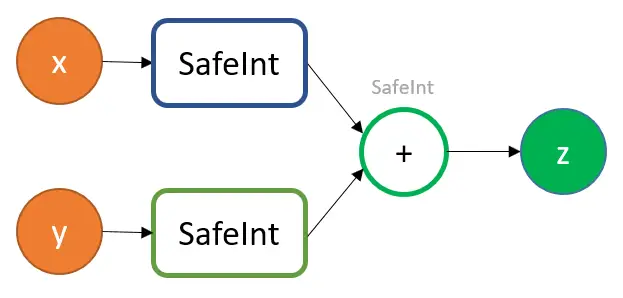
Part 1 of Semmle QL’s vulnerability hunting
We’ve previously discussed how MSRC automates root cause analysis of discovered and reported vulnerabilities on this blog. Our next step is variant analysis, which involves identifying and looking into any vulnerability variants. In order to prevent these variants from being exploited in the wild, it is crucial that we locate all of them at once…
