Your cart is currently empty!
Author: Omar
-
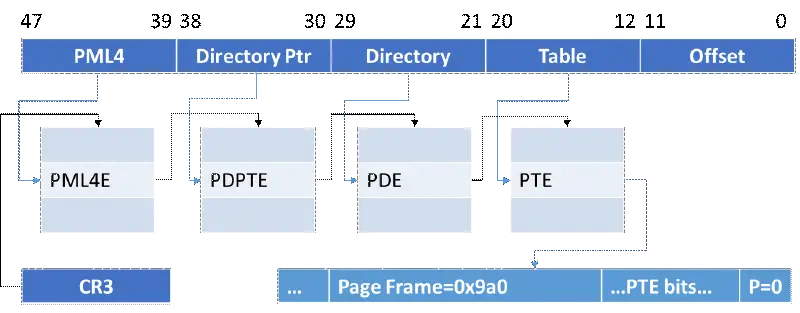
L1 Terminal Fault ( L1TF ) analysis and mitigation
A new class of hardware vulnerabilities known as Spectre and Meltdown, which involve speculative execution side channels, received advisory and security updates from Microsoft in January 2018. In this blog post, we’ll give a technical analysis of the new L1 Terminal Fault ( L1TF ) speculative execution side channel vulnerability, which has been given the…
-
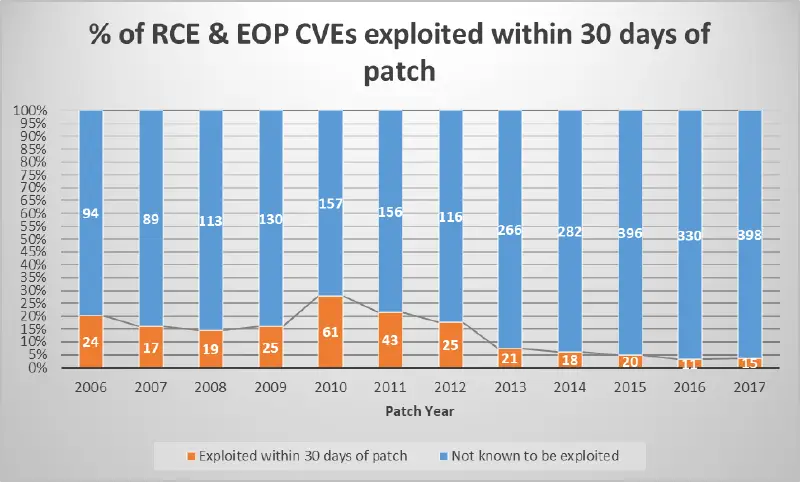
Microsoft’s Mitigation Bypass Bounty Changes Announced
Control Flow Guard ( CFG ) will no longer be included in the list of in-scope mitigations, according to a change to the Mitigation Bypass Bounty that was announced today. We’ll give more background and explain why we’re making this change in this blog post. Background for Mitigation Bypass Bounty By learning about bypasses, Microsoft…
-
Microsoft Security Service Commitments for Windows Draft
September 10, 2018 update You can find the Servicing Criteria for Windows at the link below, which has become an official document. Microsoft appreciates the comments on the draft copy from the research community. Windows Security Servicing Criteria from Microsoft
-
Speculative store bypass analysis and mitigation (CVE-2018-3639 )
Microsoft released an advisory and security update for Spectre and Meltdown, two new hardware vulnerabilities, in January 2018. In this blog post, we’ll give a technical analysis of the CVE-2018-3639 subclass of speculative execution side channel vulnerabilities known as SPECULATE Store Bypass ( SSB ). Ken Johnson of the Microsoft Security Response Center ( MSRC…
-
There are publically available Hyper-V Debugging Symbols.
We place a high priority on the security of Microsoft’s cloud services. Microsoft Hyper-V, which we use to separate tenants in the cloud, is one of the technologies that is essential to cloud security. Microsoft has invested significantly in the security of Hyper-V and the potent security features it enables, such as Virtualization-Based Security (VBS…
-
evaluating the vulnerability of DLL planting
Every now and then, DLL planting ( also known as binary planting, hijacking, or preloading ) resurfaces, and Microsoft’s response to the report is not always known. The parameters taken into account when triaging DLL planting issues will be attempted to be clarified in this blog post. It is common knowledge that Windows uses a…
-
KVA Shadow: Reducing Windows Meltdown
On January 3rd, 2018, Microsoft released an advisory and security updates that relate to a new class of discovered hardware vulnerabilities, termed speculative execution side channels, that affect the design methodology and implementation decisions behind many modern microprocessors. This post dives into the technical details of Kernel Virtual Address (KVA) Shadow which is the Windows…
-
Reducing hardware vulnerabilities
Hardware vulnerabilities On January 3rd, 2018, Microsoft released an advisory and security updates related to a newly discovered class of hardware vulnerabilities involving speculative execution side channels (known as Spectre and Meltdown) that affect AMD, ARM, and Intel CPUs to varying degrees. If you haven’t had a chance to learn about these issues, we recommend…
-
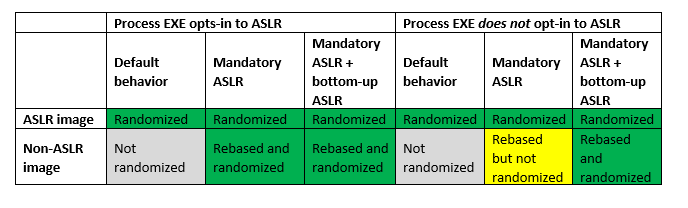
defining the required ASLR’s behavior
When Windows Defender Exploit Guard ( WDEG ) and EMET were used to enable system-wide mandatory Address Space Layout Randomization ( ASLR ) on Windows 8 and above, the CERT/CC published an advisory last week outlining some unexpected behavior they saw. In this blog post, we’ll go over the configuration problem that CERT/CC ran into…
-
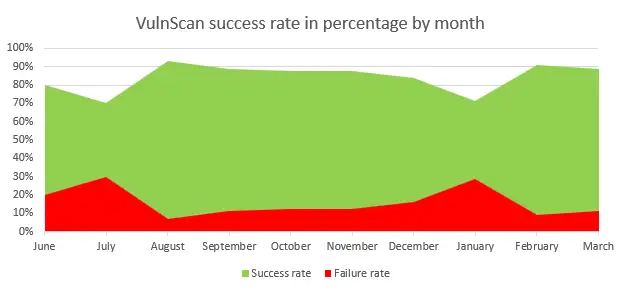
VulnScan – Automated Triage and Root Cause Analysis of Memory Corruption Issues
Our engineering team’s task is to evaluate the severity, impact, and underlying causes of these issues after receiving reports about potential vulnerabilities in our products from the Microsoft Security Response Center ( MSRC ). In reality, memory corruption problems account for a sizable portion of these reports. An MSRC security engineer typically needs to examine…
