Authorities claimed that LockBitSupp, the person( s ) responsible for the ransomware service’s persona on cybercrime forums like Exploit and XSS, “has engaged with law enforcement. “
The change occurred after the popular ransomware-as-service ( RaaS ) operation was shut down as part of a coordinated global operation known as Cronos. The criminals ‘ use of more than 14, 000 rogue accounts on third-party services like Mega, Protonmail, and Tutanota has been shut down.
” We are aware of his identity. We are aware of his residence. We are aware of his value. According to a message posted on the now-seized ( and offline ) dark web data leak site, LockbitSupp has cooperated with law enforcement.
Long-time LockBit users have interpreted the action as an effort to raise suspicion and sow the seeds of mistrust among affiliates, ultimately undermining trust in the cybercrime ecosystem.
There is evidence to suggest that at least three different people, including the gang’s leader, have operated the” LockBit” and” Supp” accounts, according to research published by Analyst1 in August 2023.
However, LockBit stated that they did n’t think law enforcement knew his/her/their identities in a conversation with malware research group VX- Underground. Additionally, they increased the reward to$ 20 million for anyone who could message them using their real names. It’s important to note that late last month, the reward was raised from$ 1 million USD to$ 10 million.
Since its inception in September 2019, LockBit, also known as Gold Mystic and Water Selkie, has undergone several iterations. The cybercrime syndicate has also been secretly working on a new version of the game called Lockbit-NG-Dev before having its infrastructure demolished.
According to Trend Micro,” LockBit-NG-Dev is now written in.NET and compiled using CoreRT.” This enables the code to be more platform-agnostic when deployed alongside the.NET environment. It eliminated the user’s printers ‘ ability to print ransom notes and self-propagating capabilities.
A validity period, which only continues to function if the current date falls within a certain date range, is one of the notable additions. This suggests that the developers have made an effort to stop malware reuse and thwart automated analysis.
The leak of the ransomware builder by a disgruntled developer in September 2022, as well as concerns that one of its administrators might have been replaced by government agents, are said to have spurred work on the next generation variant.
The LockBit-managed accounts ‘ ban from Exploit and XSS toward the end of January 2024 for failing to pay the initial access broker who gave them access did n’t help either.
Trend Micro claimed that the actor” came across as someone who was” too big to fail” and even displayed contempt for the arbitrator who would decide how the claim would turn out. This speech” showed that LockBitSupp is probably negotiating access fees or the percentage of ransom payouts with affiliates on the basis of their reputation.”
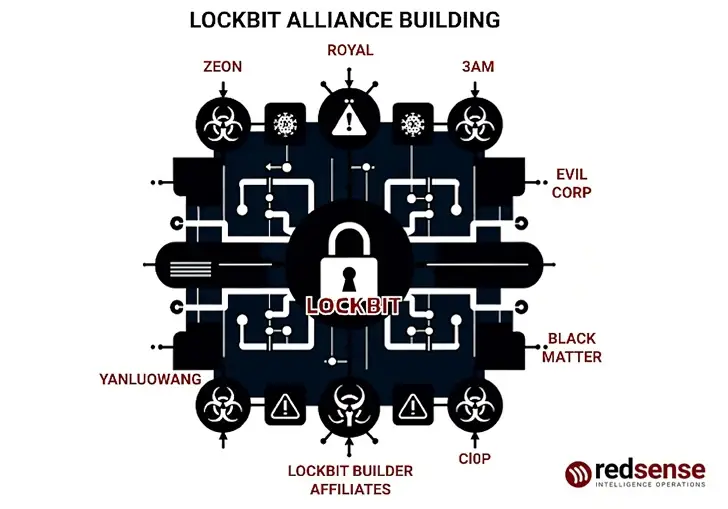
Over 28 affiliates were found by PRODAFT in its own analysis of the LockBit operation, some of whom are connected to other Russian e-crime organizations like Evil Corp, FIN7, and Wizard Spider ( also known as TrickBot ).
These connections are further supported by the gang’s appearance as a “nesting doll” with three distinct layers, which gave the impression that the organization was compromising dozens of affiliates while covertly forging personal alliances with other ransomware organizations to steal highly skilled pen testers.
Yelisey Bohuslavskiy and Marley Smith, researchers from RedSense, claim that the smokescreen materialized as a Ghost Group model, with LockBitSupp acting” a mere distraction for actual operations.”
According to them,” A Ghost Group is a group with very high capabilities that transfers those capabilities to another brand by allowing them to outsource operations.” Zeon, who has been delegating their tasks to LockBit and Akira, is the most obvious example of this.
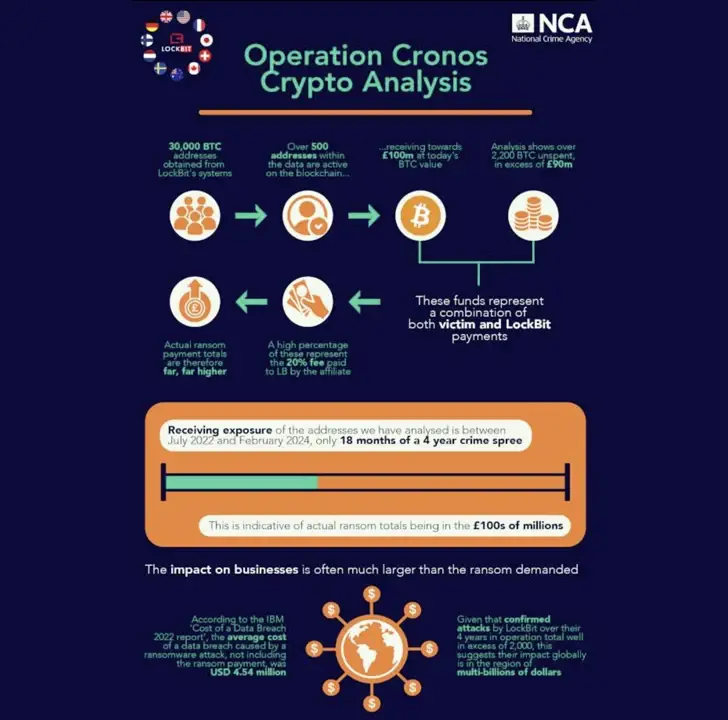
The organization is thought to have amassed more than$ 120 million in illicit profits over the course of its multi-year operation, becoming history’s most active ransomware actor.
The U. K. National Crime Agency (NCA ) stated that “given that confirmed attacks by LockBit over their four years of operation total well over 2, 000, this suggests that their impact globally is in the range of multi-billion dollars.”
It goes without saying that Operation Cronos has probably permanently damaged the criminal organization’s ability to continue using ransomware, at least under its current name.
RedSense stated that it is highly unlikely that the infrastructure will be rebuilt and that LockBit’s leadership lacks the necessary technical skills. As evidenced by the primitivism of their infrastructure, the people to whom they delegated their structural development have long since left LockBit.
After a takedown, initial access brokers, who were the main driving force behind LockBit’s business, will no longer trust their access to groups because they want to convert it into cash.