61 Brazilian banks are targeted by a new Coyote Trojan using an nim-powered attack
A new banking scam called Coyote is targeting 61 banking institutions, all of which are based in Brazil.
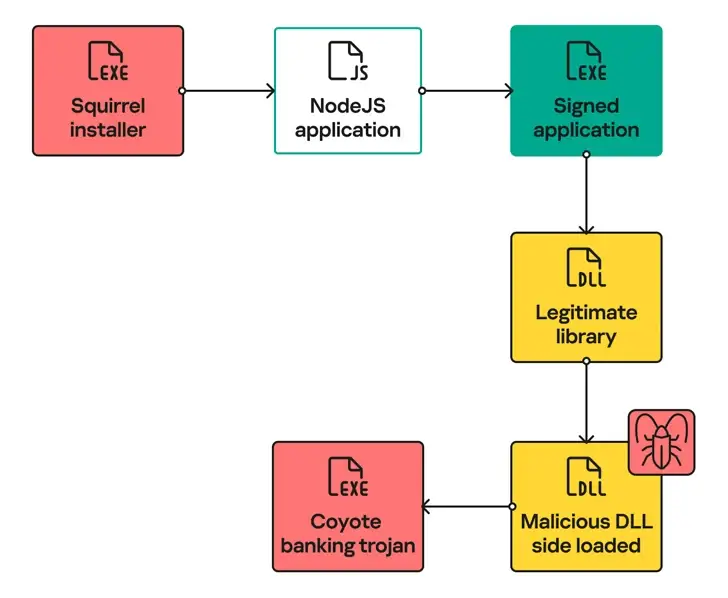
” This malware makes use of Node .js and the Squirrel installer for distribution.” According to a report released on Thursday by Russian cybersecurity company Kaspersky, js and the relatively new multi-platform programming language Nim will complete its infection.
The use of the open-source Squirrel framework for installing and updating Windows apps distinguishes Coyote from other banking trojans of its kind. The switch from Delphi to a rare programming language like Nim, which is common among banking malware groups targeting Latin America, is another notable departure.
the “libcef” malicious dynamic-link library. dll” is side-loaded using a legitimate executable with the name “obs-browser-page.” exe, which the Node also contains. project in js. It’s important to remember that the libcef was original. The Chromium Embedded Framework ( CEF ) includes dll.
Once activated, Coyote “monitors all open applications on the victim’s system and waits for the specific banking application or website to be accessed” before contacting a server under actor control to retrieve next-stage directives.
A variety of commands can be used to run the machine, including taking screenshots, recording keystrokes and ending processes, showing fake overlays or moving the mouse cursor in one place or even turning it off. Additionally, a phony” Working on updates” option can be used to completely block the machine. message while secretly carrying out evil deeds.
According to Kaspersky, adding Nim as a loader makes the trojan’s design more complicated. This evolution demonstrates how threat actors are modifying and utilizing the most recent languages and tools in their malicious campaigns while also highlighting the threat landscape’s growing sophistication.
Additionally, it comes after the development of a brand-new MrTonyScam-related Python-based information stealer that is distributed via Microsoft Excel and Word documents that have been booby-trapped.
According to a report released this week by Fortinet FortiGuard Labs, the stealer” collects browsers ‘ cookies and login data [ …] from receptacles like Chrome and Edge as well as locally-focused browser like the C-Cc browser.”
Five-year prison sentence for the developer of a Trojan horse
Npm Trojan Bypasses UAC, Installs AnyDesk with &quot, Oscompatible, and Package
O AliExpress, are you a confidant? I’m here to help you with your security
A Patriotic Scientist Who Changed the Periodic Table and Then Went to War, Henry Moseley