Two malicious packages were found using the DLL side-loading technique to run malicious code and avoid detection by security software on the Python Package Index ( PyPI ) repository, according to cybersecurity researchers.
Before they were removed, the packages with the namesNP6HelperHttptest and NF6HeaterHTtper had each been downloaded 537 or 166 times, respectively.
According to a report published by ReversingLabs researcher Petar Kirhmajer and made available to The Hacker News,” the most recent discovery is an example of DLL sideloading carried out by an open-source package that suggests the scope of software supply chain threats is expanding.”
The term “NP6” is notable because it refers to ChapsVision’s authorized marketing automation solution. The fake packages, in particular, are typosquats of the PyPI-published helper toolsNP6HelperHttp and NV6 HelperConfig from one of ChapsVision’s employees.
To put it another way, the objective is to deceive programmers looking for NP6HelperHttp and NPCConfig into downloading their malicious counterparts.
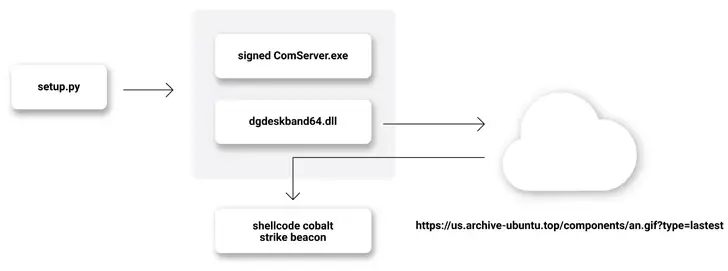
A setup is contained between the two libraries. Python script that can download two files and is actually executable from Kingsoft Corporation ( ComServer ), based in Beijing. exe ) and the malicious DLL to be side-loaded (dgdeskband64 ), respectively. dll ‘ ).
As previously seen in the case of an npm package called aabquerys, which also used the same technique to execute code capable of deploying remote access trojan, the goal of side-loading the DLL is to avoid detection of malicious code.
For its part, the DLL connects to a domain that is under attacker’s control (us ). Ubuntu Archive [. ] top” ) to retrieve a GIF file that, in reality, contains shellcode for the red teaming post-exploitation toolkit Cobalt Strike Beacon.
Evidence points to a larger campaign involving the distribution of comparable executables that are open to DLL side-loading as part of the packages.
Security researcher Karlo Zanki stated that “development organizations need to be aware of the threats related to supply chain security and open-source package repositories.”
Threat actors will abuse open-source package repositories to impersonate businesses and their software products and tools even if they are n’t using them.