Hackers have begun to exploit TeamCity On-Premises ‘ critical-strength authentication bypass vulnerability ( CVE- 2024- 27198 ), which JetBrains addressed in a Monday update.
Numerous new users are being created on unpatched TeamCity instances that have been exposed on the public web.
Supply-chain attack risk
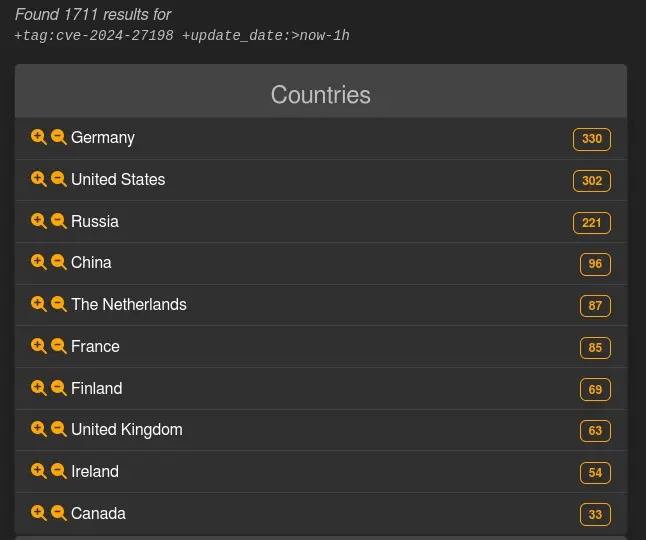
More than 1, 700 TeamCity servers have not yet received the fix, according to LeakIX, a search engine for exposed device flaws and vulnerabilities.
source: LeakIX
Germany, Russia, and the United States are the most vulnerable hosts LeakIX has identified, followed closely by China, the Netherlands, and France.
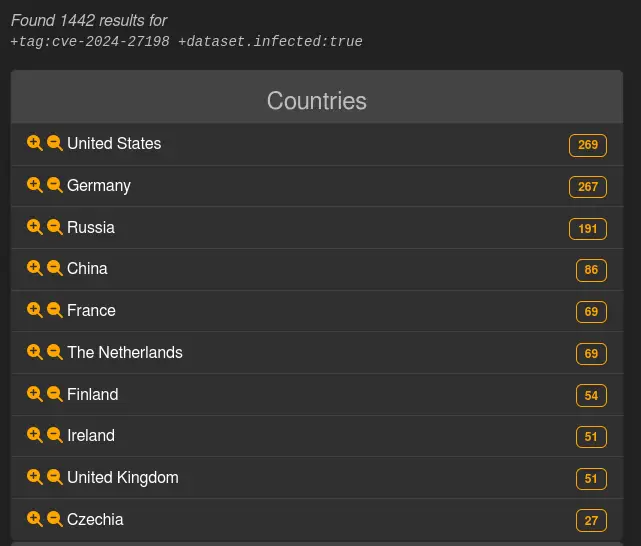
According to the platform, hackers have already hacked into more than 1, 440 instances of these.
LeakIX reported to BleepingComputer that “between 3 and 300 hundreds of users are created on compromised instances, typically with 8 alphanum characters.”
source: LeakIX
On March 5, a sizable increase in attempts to exploit CVE- 2024- 27198 was also reported by Grey Noise, a company that analyzes internet scanning traffic.
The majority of attempts, according to GreyNoise statistics, are made by American-based DigitalOcean hosting infrastructure systems.
The TeamCity servers, according to LeakIX’s Gregory Boddin, are software development and deployment tools, according to BleepingComputer.
Because they may contain sensitive information like credentials for the environments where code is deployed, published, or stored ( such as stores and markets, repositories, company infrastructure ), this implies that compromising them could lead to supply-chain attacks.
Rapid7, a cybersecurity company, shared the same concern in a blog post looking at the vulnerability and how it can be used to launch attacks.
urgent update on TeamCity
CVE- 2024- 27198 is affected by all releases of TeamCity up until 2023.11.4 and has a critical severity score of 9.8 out of ten.
A remote, unauthenticated attacker could take control of a vulnerable server with administrative privileges because it is present in the server’s web component.
The vulnerability, which was discovered by Stephen Fewer, a principal security researcher at Rapid7, was identified by JetBrains in the middle of February and fixed on March 4.
An attacker could exploit the vulnerability by using it to execute remote code, according to Rapid7’s detailed technical documentation that includes detailed explanations of what causes the issue.
With a fix for CVE- 2024- 27198, JetBrains announced the release of TeamCity 2023.11.4 on Monday, encouraging all users to update their instances to the most recent version.
Administrators of on-premise TeamCity instances should immediately take action to install the newest release given the already extensive exploitation that has been observed.











