One of the biggest threats to organizations today is ransomware. Given that threat actors are constantly improving their methods and approaches, beating it is no simple task. Recent changes, for instance, include improvements to ransomware-as-the-service ( RaaS ) models, the adoption of new programming languages, advancements in targeting and deployment, and an increase in attacks being launched after business hours and on weekends to obstruct detection and incident response efforts.
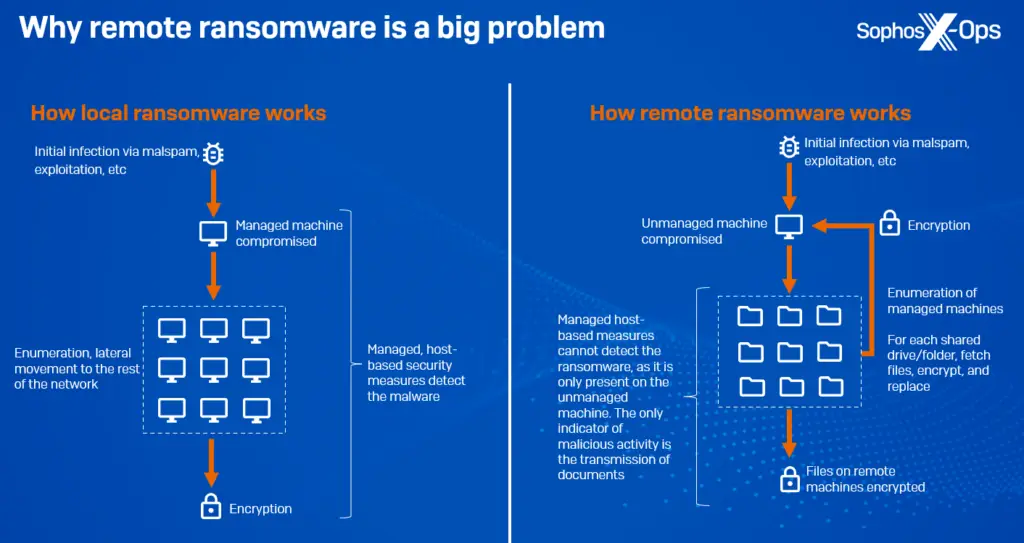
An increase in remote ransomware, which uses an organization’s domain architecture to encrypt data on managed domain-joined machines, is one of the more significant developments. The only sign of compromise is the transmission of documents to and from other machines because all malicious activity, including ingress, payload execution, and encryption, takes place on an unmanaged machine, bypassing modern security stacks. According to our telemetry, intentional remote encryption attacks have increased by 62 % year over year since 2022. Additionally, according to Microsoft’s 2023 Digital Defense Report, remote encryption is used in about 60 % of human-operated ransomware attacks, and 80 % of all compromises come from unmanaged devices, showing a lack of active asset management. Remote encryption is a technique that has been around for some time; as recently as 2013, CryptoLocker was focusing on network shares. Ransomware families known to support it include Akira, ALPHV/BlackCat, BlackMatter, LockBit, and Royal.
A condensed explanation of the operation of remote ransomware is shown in Figure 1.
Unsurprisingly, the rise and ongoing development of ransomware has sparked a flurry of research aimed at finding and preventing it, with academics, security researchers, and vendors all offering different solutions. As a type of malware, ransomware presents particular practical and intellectual difficulties, and the variety of available solutions reflects this. Many of these solutions aim to address one or more of the distinctive behavioral characteristics of ransomware, such as listing filesystems, accessing and encrypting files, and producing runsom notes. Others are more general, using standard anti-malware methods against ransomware.
We’ll give a quick overview of some of these methods and their benefits and drawbacks in this, the second issue of our brand-new technical thought leadership series ( the first, on memory scanning, is available here ), before looking in-depth at our own contribution to the field, CryptoGuard.
One thing to keep in mind before we get started is that a ransomware attack has several stages, the majority of which will happen before the solutions we talk about in this article take effect. A well-defended business will have multiple layers of defense that should fend off attacks at different points, so specific anti-ransomware solutions are frequently not necessary. However, if all else fails and a determined foe enters the encryption stage, technology is required to stop irreparable harm. Encryption is not reversible, but other stages of an attack, such as initial infection, persistence, lateral movement, and so on, are.
methods of anti-ransomware
static remedies
Static techniques for ransomware detection are not significantly different from those used to detect any other type of malware, i .e., those that can be carried out passively, without requiring the execution of the malware. In this vein, solutions include signature-matching, string comparison, file operations, analyzing behavioral traits, deep learning methods, and PE headers.
Determined attackers can evade static methods by changing the code until signature detections are broken, even though they have the advantage of being relatively quick and inexpensive. Additionally, they are less effective against remote ransomware, new variants, packers, obfuscators, and in-memory threats.
solutions that are dynamic
solutions that are dynamic, on the other hand, tend to be more computationally expensive, but offer greater coverage. Dynamic anti-ransomware solutions in this vein include the following:
interactions in the filesystem
Some security measures will keep an eye out for changes to file extensions, high-frequency read/write and renaming operations, or new files with extensions connected to ransomware variants. The open-source project Raccine, for instance, is based on the idea that many ransomware variants delete shadow copies using vssadmin. On the other hand, some solutions leverage other interactions. Racine functions by intercepting vssadmin requests and terminating the process in charge.
Given that ransomware targets files, it makes sense that many strategies should concentrate on filesystem interactions. Although it is possible to dynamically adjust the degree of monitoring, some filesystem-based techniques may also not be effective when it comes to remote ransomware. Many of them, however, are dependent on analysis within a sandboxed environment and are predicated on anomalous patterns that threat actors may try to avoid generating.
Folder protection
While Windows Defender’s Controlled Folder Access ( CAF ) solutions restrict access to folders to particular applications, they are primarily designed with individual users in mind. By limiting unauthorized access to designated folders and allowing only trusted applications to edit files inside of them, CAF aids in the prevention of ransomware. Due to the ongoing requirement for meticulous folder and application management, this method may not be as useful for business networks. Additionally, it ignores the possibility of attacks gaining access to trusted apps, a common strategy used in ransomware attacks.
API requests
Some security solutions will assess API requests invoked by a process, either by flagging suspicious and seldom-seen calls or by determining potentially malicious call sequences.
Most ransomware employs API requests, although some variants use evasive measures to disguise these (particularly for API requests which are known to be suspicious, such as CreateRemoteThread or VirtualAllocEx, commonly used in process injection; or API requests related to encryption). Monitoring API requests at the kernel level certainly seems to be a worthwhile approach, but such monitoring is resource-intensive, can generate false positives, and is challenging to implement at scale. Additionally, when it comes to remote ransomware, the process itself may not be on the host being attacked, which can frustrate this approach.
Honeyfiles
Inconspicuous files that are placed in a directory and that legitimate users are asked not to touch are known as “honefiles,” “decoy files,” ‘ bait files, or” canary files” in many security products as an anti-ransomware solution. If those files are accessed or modified by any process, a separate monitoring system, either at the user level or the kernel level, is triggered, at which point an alert is produced.
Honeyfiles can serve as a quick alert that an attack may be underway because they are small, lightweight, and low-effort. They do have some restrictions, though. Defenders must make sure that any alert is received and responded to as soon as possible because, on purpose, an attack will already be underway when a honeyfile is activated. Additionally, they must be strategically positioned within filesystems—deep enough to prevent unintentional tampering by regular, legitimate users and processes, but not so far that crucial documents must first be encrypted.
Fingerprinting
A less popular method is to “fingerprint” specific malicious patterns, such as in CPU usage, network traffic, or CPU signals.
In terms of network traffic, it’s important to note that threat actors customize and compile the ransomware binary for each victim in contemporary human-led attacks, which is a tactical move meant to make detection difficult and the decryption process more difficult. Due to the fact that the encryption process is self-contained within the malware and uses a victim-specific embedded public key, this custom-built ransomware typically uses an embedded victim’s note and is deployed “fire and forget,” eliminating the need for direct communication with the threat actor.
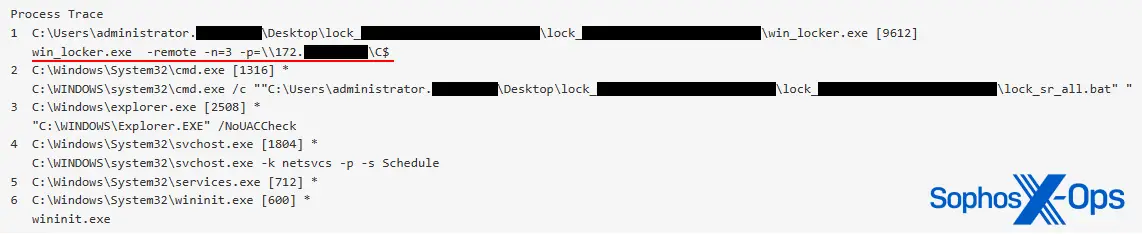
TDT ( Threat Detection Technology ), an emerging Intel technology, enables hardware-level ransomware detection. A review by SE Labs shows that it is remarkably effective against a wide range of encryption techniques. This only applies to particular Intel CPUs, excluding ARM and AMD architectures. This restriction results from TDT’s reliance on a machine learning model that is trained on CPU performance signals from particular encryption profiles of ransomware families. The Intel-trained model cannot support remote encryption and is reliant on vendor support. This technology’s drawback is that some ransomware programs, like LockBit and Akira, are purposefully designed to only encrypt a portion of each file. As a result, the attack’s impact is accelerated, affecting more files more quickly. Additionally, it implies that Intel TDT detects files after a sizable number of them have already been compromised.
Figure 2 shows Akira ransomware, which specifically targets remote data and only encrypts 3 % of each file.
Automated containment based on telemetry
For incident response and alert analysis, the majority of contemporary endpoint protection solutions transmit data to the cloud. However, it can take anywhere from a few minutes to several hours for alert telemetry to automatically piece together the specifics of an active human-led ransomware attack. The configuration of the telemetry reporting frequency, the presence of additional alert signals, and the cloud’s ability to combine and correlate particular events from various protected machines all affect this latency.
In order to isolate a particular user account that the attacker is suspected of compromising, managed devices may be subject to an automated response after being detected. It is important to note that the distribution of this policy also takes time (up to hours ), despite the fact that it aims to stop an impending or ongoing ( remote ) ransomware encryption attack coming from the identified account. Furthermore, the circumstances do not always favor an efficient cloud-driven dynamic containment strategy when the attacker starts encryption without triggering prior alerts on managed machines ( as noted above, 80 % of attacks involve unmanaged machines ) or chooses to start the encryption process from an alternate user account. However, it can be beneficial in some situations.
Rollback
Dynamic anti-ransomware solutions typically require some degree of encryption or data manipulation to have occurred before detecting the attack. As a result, some files will probably become encrypted, necessitating the use of the backup and restore functions to retrieve the affected files.
Some endpoint protection products use Volume Shadow Copies, a Windows feature that periodically generates data snapshots, to restore unencrypted file versions. Even when they are in use, these” shadow copies” record file or volume states. The effectiveness of rollback depends on identifying and addressing the ransomware incident before the subsequent scheduled snapshot, which usually happens every four hours. Attackers frequently delete shadow copies, they do not protect files on network mapped drives, and this method has its drawbacks. Additionally, as was already mentioned, the majority of attacks occur after business hours, making recovery efforts more difficult.
Summary
Generally speaking, many of these methods concentrate on identifying behavioral characteristics that are a sign of ransomware activity in order to look for “badness.” Although this appears to be a wise choice, it does have one major flaw in that threat actors have an incentive to hide or obfuscate those characteristics in order to avoid detection. CryptoGuard, on the other hand, approaches things differently.
CryptoGuard
Previously known as HitmanPro, CryptoGuard. When determined threat actors have evaded all other protections and are ready to start encryption, Alert, which has been a part of Intercept X since 2016, was first created in 2013. It is intended to be the final layer of defense against both local and remote ransomware. Blocking WannaCry, LockBit, and REvil ransomware are a few of its notable accomplishments. While we closely monitor changes in the ransomware industry, CryptoGuard has n’t changed all that much over the years, mainly because it has not needed to.
an unbalanced strategy
CryptoGuard does not at all search for attackers, executable ransomware, or malicious behavioral patterns, in contrast to the majority of the methods mentioned above. Of course, other security solutions, such as Sophos products, carry out these actions; they are an essential component of a layered defense that ideally prevents attackers from reaching the encryption stage. However, CryptoGuard itself uses an approach that is more symmetrical, for when those layers have been circumvented.
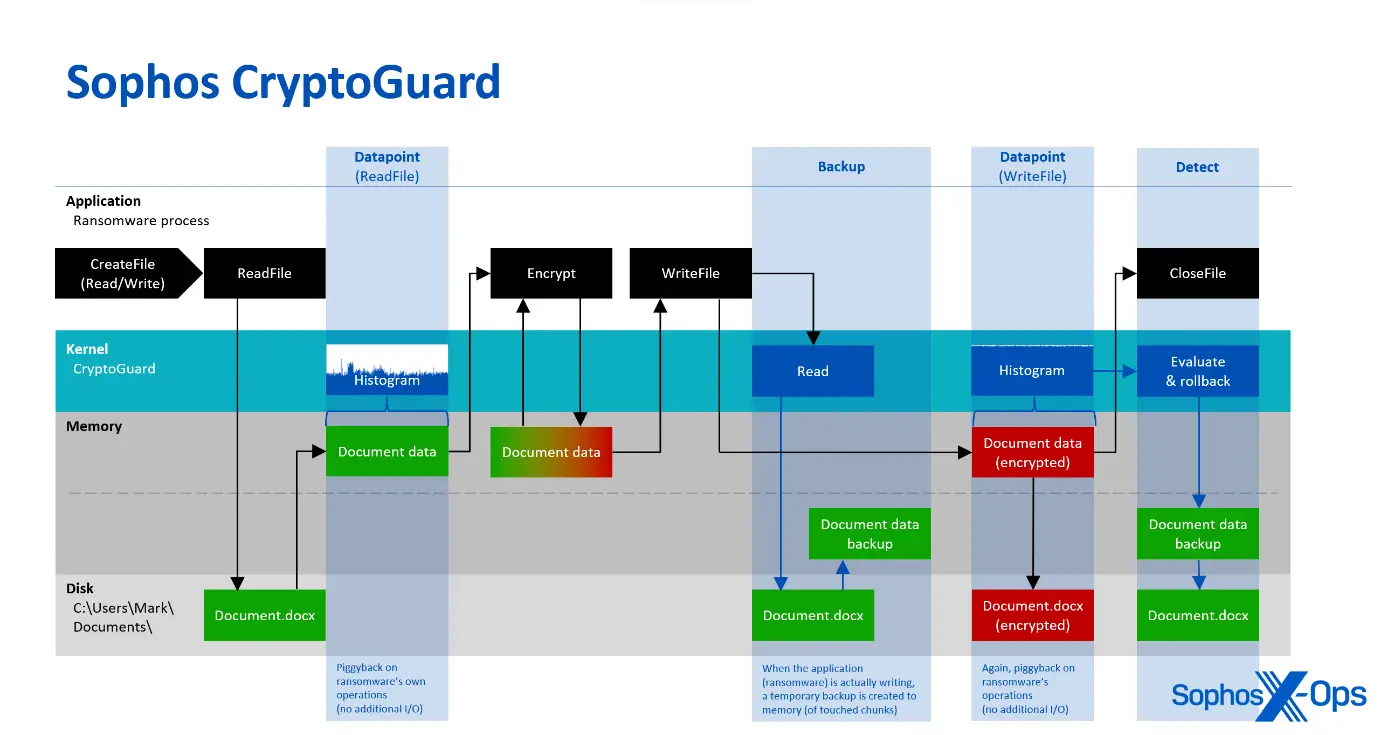
CryptoGuard concentrates on the contents of files by using a mathematical algorithm to analyze their patterns rather than searching for “badness.” The minifilter driver of CryptoGuard, which runs within the Windows operating system kernel, continuously generates histograms of the read and written data whenever a process opens the file for reading and writing. These histograms help us comprehend the overall pattern and traits of the data. They are assessed for entropy and statistically examined to see if the read and written data is compressed, encrypted, or unencrypted. The built-in evaluators use mathematical models to categorize the data. The analysis is very effective because it does not result in additional disk input or output ( I/O ) since it uses the same memory buffers that the operating system provides for the requesting process.
Figure 3: A summary of CryptoGuard’s business operations
Even in cases where an unprotected remote machine on the network is attacking shared documents on a Sophos- protected file server, for instance, this capability offers symmetric protection. Most human-led ransomware attacks aim to encrypt shared data on remote machines, as was already mentioned. In these situations, the ransomware is not carried out on the secure remote machine (either because the attacker did n’t deploy it there or because endpoint protection prevented it from doing so ). As a result, the machine that stores the targeted data cannot observe the ransomware binary itself or the attacker-controlled process ( that performs the encryption ).
Therefore, technologies like antivirus, machine learning, indicators of breach, etc., cannot be used to detect malicious code on the attacked machine. –all centered on identifying enemies and their malicious code—are completely sidelined and not in play ( even if it is a well-known, years-old sample that is responsible for the encryption ) CryptoGuard, on the other hand, can automatically take action by blocking the IP address of the remote machine and undoing the changes it made when it replaces documents in the shared folder with encrypted versions. In order to roll back changes if mass encryption is discovered, it creates temporary backups of any modified files. It can also detect the deployment of ransom notes within the folders where the ransomeware has encrypted files, and it can do this. As a result, even though it was n’t intended to do so, it occasionally identifies instances of data exfiltration.
Zero-trust
In order to perform encryption, adversaries will occasionally abuse an already-existing process or package a normally benign process that loads an evil DLL ( also known as dLL side-loading ). The encryption activity is carried out under the name of the benign process, which is currently running attacker-code and encrypting documents.
The Kaseya VSA incident, in which the REvil threat actor embedded a malicious DLL to be side-loaded in an out-of-date but vulnerable Windows Defender executable, is an actual example of this. Defender was the threat actor’s choice on purpose because Microsoft-signed code is typically trusted by protections. A DLL may also be “approved” sooner because it cannot be examined as thoroughly as an executable in a sandbox environment.
On that particular occasion, Sophos found both the REvil payload itself and a code certificate that was specifically associated with it. The REvil dropper was able to be installed on machines thanks to Kayesa’s protection exclusions, but CryptoGuard discovered the ransomware because it is unconstrained by them and prevents file encryption on drives that are protected.
a stroll
Conclusion
When it comes to dealing with ransomware, there is no magic solution. Numerous layers, from vulnerability remediation and configuration reviews to user education and security solutions, should be a part of an effective defense. The robustness and effectiveness of the last layer, however, should be taken into account when all other measures have failed and threat actors are in a position to carry out their ransomware, regardless of which layers organizations employ and how many. At that point, the solutions we’ve discussed here start to make sense.
These solutions cover a wide range of behavioral characteristics and activities. Many have distinct strengths and weaknesses and differ greatly in terms of their scalability, versatility, and cost-benefit ratios. The majority of solutions concentrate on “detecting badness” in some way, whether through API call analysis, honeyfiles, or some other form of fingerprinting. A layered and diverse defense stack is a good strategy, and that is n’t always the case. However, as we’ve demonstrated, Intercept X’s CryptoGuard strategy is slightly different and more asymmetrical, concentrating on file contents rather than the actions of ransomware or its users.
Ransomware is constantly changing, and as a result, more and more solutions and methods are probably going to be developed. We’ll keep track of changes in both ransomware and the solutions intended to detect and prevent it, as we have been doing for the past ten years.