Customers receive 72 patches on February’s Patch Tuesday.
After a light start to the year, February delivered 72 patches and 21 advisories to Microsoft customers. The CVEs addressed in this month’s Patch Tuesday release included 43 for Windows. Twelve other product groups or tools are also affected. Of the CVEs addressed, five are considered Critical in severity by Microsoft, these affect Windows, Office, Exchange, and Dynamics 365.
At patch time, two of the issues are known to be under exploit in the wild, and none has been publicly disclosed. ( However, one of the advisory items most certainly has, more on that in a minute. ) Eight of the addressed vulnerabilities in Windows, Office, and Exchange ( including a Critical- severity elevation- of- privilege issue with an attention- getting 9.8 CVSS base score ) are by the company’s estimation more likely to be exploited in the next 30 days. Six of the issues addressed are covered by Protections for Sophos, and we include information on those in a table below.
In addition to these patches the release included information on six Chromium/Edge- related CVEs, including an RCE that could lead to sandbox escapes, one MITRE- issued CVE concerning a DNS issue that could lead to denial of service, one Github- issued CVE addressing the recent CVE- 2024- 21626″ Leaky Vessel” issue affecting Mariner, disclosed in a lengthy public post by Snyk two weeks ago and patched by various other affected companies since then, and 13 Adobe advisories, all related to Acrobat Reader.
We do n’t include advisories in the CVE counts and graphics below, but we provide information on everything in an appendix at the end of the article. We are as usual including at the end of this post three other appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
- Total Microsoft CVEs: 72
- Total Adobe advisories covered in update: 13
- Total Edge / Chromium issues covered in update: 6
- Total Mariner advisories covered in update: 1
- Total MITRE advisories covered in update: 1
- Publicly disclosed: 0
- Exploited: 2
- Severity
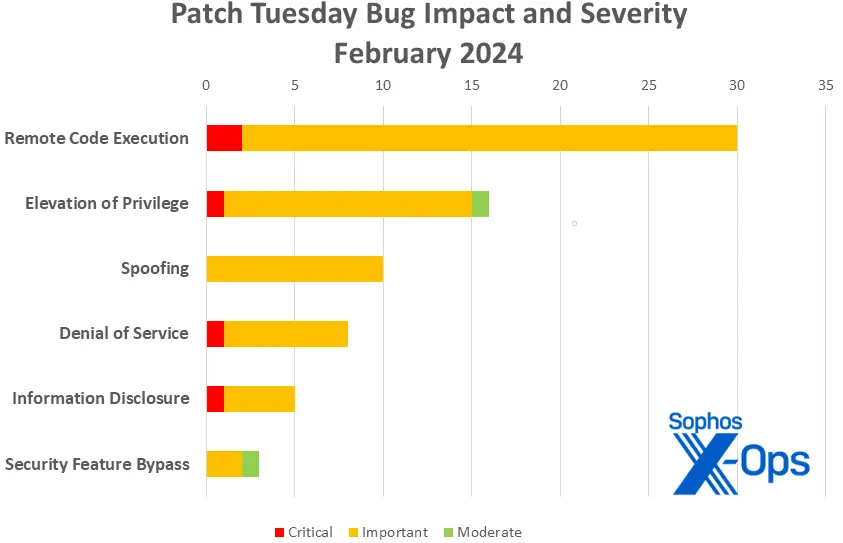
- Critical: 5
- Important: 65
- Moderate: 2
- Impact
- Execution of remote code: 30
- Privilege Elevation: 16
- 10 Spoofing
- Service Denial: 8
- Disclosure of Information: 5
- Bypass for security features: 3
Figure 1: Following January’s significant month for information disclosure bugs, a plethora of OLE-related fixes restored remote code execution for February.
Products
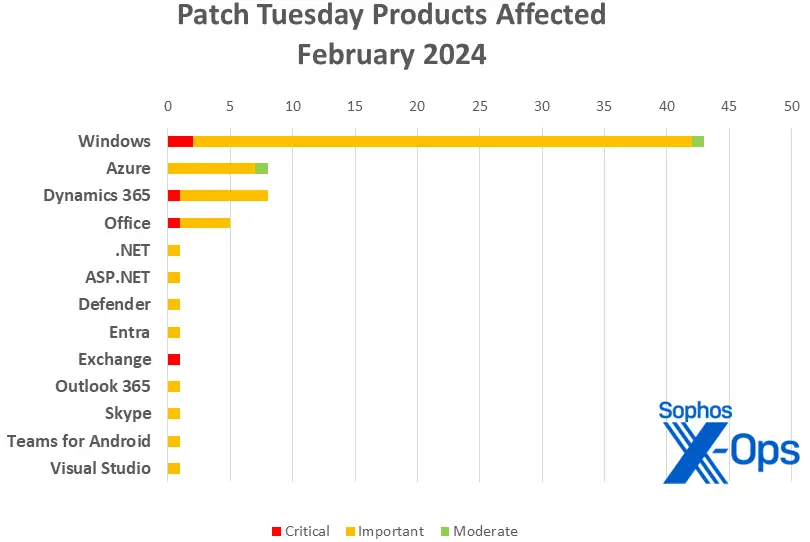
- 43 Windows
- Azure 8.
- 8 Dynamics 365
- Office 5.
- NET: 1.
- ASPNET: 1. (shared with Visual Studio)
- 1 Defender
- Azure AD: 1 entra
- 1 exchange
- Outlook 1 365
- Skype: 1
- Android teams: 1
- ( Shared with ASP) Visual Studio: 1. ( NET )
Figure 2: Due in part to numerous fixes for Windows Defender Application Control ( WDAC ), this month has been very Windows-heavy.
Notable updates from February
A few specific things, in addition to the ones already covered, are important to note.
CVE: 2024: 21350, 21342, 21358, 2025: 21369, CAVE: 2248, 20-24: 21471, 22361, 2026: 20, 24, 21378, 2127, 21, and 21375 are all examples of Cves that are included in this list.
For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider
fifteen CVEs with a common name, severity ( Important ), impact (RCE), high CVSS base score ( 8.8 ), and finder non-identification ( Microsoft credits all 15 to” Anonymous” ) One more ( but related ) person is with them. Vulnerability of Microsoft WDAC ODBC Driver Remote Code Execution is the only difference between the number and name of the patch, which is CVE-2024-21353.
CVE-2024-21404
Increased Privilege Vulnerability in the Microsoft Entra Jira Single-Sign-OnPlugin
This extra-spicy EoP only receives an significant severity rating from Microsoft, but the Azure AD Jira SSO plugin is the target of its base CVSS, which is a critical level9.8. Importantly, the attacker can update the Entra ID SAML metadata and information for the plugin, changing the application’s authentication as they see fit, without even having to authenticate in order to cause trouble. All it takes is a script to access the targeted Jira server. The fix is a 1.1.2 update that can be downloaded from the Atlassian Marketplace or the Microsoft Download Center.
CVE-2024-21410
Privilege Vulnerability Increased on Microsoft Exchange Server
A NTLM relay ( pass-the-hash ) vulnerability is the other CVE this month with a 9.8CVSS. It might enable an attacker to authenticate as the user by relaying their leaked Net-NTLMv2 hash against a weak Exchange Server. It has an impact on several versions, including Exchange Server 2016 ( cumulative update 23 ), 2019, cumulative update 13, and 2019. Microsoft’s Exchange Team Blog has more information, but keep in mind that it thinks this one will be used more frequently in the coming 30 days.
CVE-2024-21378
Vulnerability of Microsoft Outlook Remote Code Execution
This significant-severity RCE uses Preview Pane as an attack vector, and according to Microsoft, exploitation is more likely to occur within the next 30 days. The competition has begun.
CVE-2024-21374
Android Information Disclosure Microsoft Teams
Google Play has a patch for this significant-severity information disclosure problem.
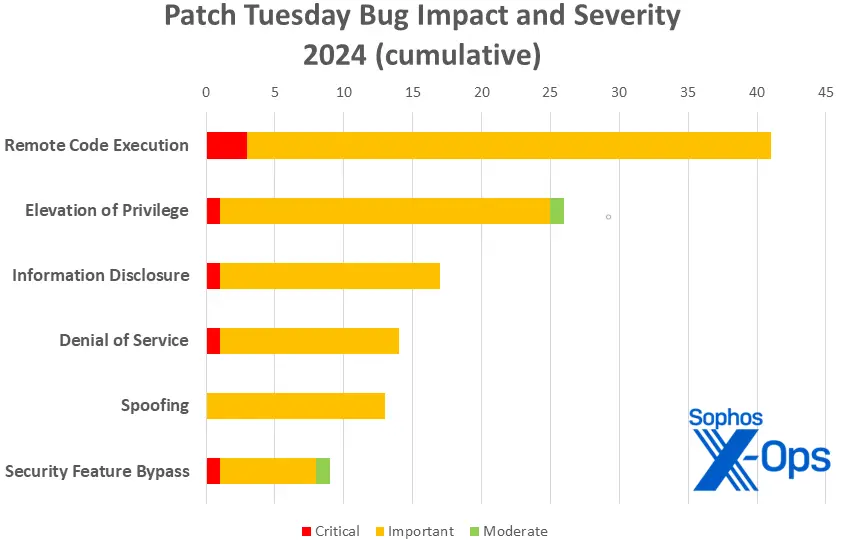
With only 120 patches so far, Figure 3: 2024’s totals are significantly behind those of previous years. ( 173 patches were released in the first two months of 2023, followed by 154, 139, 2021, and 150 in 2020. )
Protections for Sophos
| CVE | X/Endpoint IPS Sophos Intercept | Firewall Sophos XGS |
| CVE-2024-21338 | Exp/2421338-A | Exp/2421338-A |
| CVE-2024-21345 | Exp/2421345-A | Exp/2421345-A |
| CVE-2024-21346 | Exp/2421346-A | Exp/2421346-A |
| CVE-2024-21357 | Exp/2421357-A | Exp/2421357-A |
| CVE-2024-21371 | Exp/2421371-A | Exp/2421371-A |
| CVE-2024-21379 | N/A | sid:2309292 |
You can manually download Microsoft updates from the Windows Update Catalog website each month if you do n’t want to wait for your computer to automatically remove them. The winver should be run. Download the Cumulative Update package for the architecture and build number of your particular system after using the exe tool to find out which version of Windows 10 or 11 you are using.
Impact and severity of vulnerability are discussed in Appendix A.
Here is a list of February patches, arranged in terms of severity and impact. CVE further organizes each list.
Execution of remote code ( 30 CVEs )
| seriousness | |
| CVE-2024-21357 | Vulnerability of Windows Pragmatic General Multicast ( PGM ) Remote Code Execution |
| CVE-2024-21413 | Vulnerability of Microsoft Office Remote Code Execution |
| significant severity | |
| CVE-2024-20667 | Vulnerability of Azure DevOps Server Remote Code Execution |
| CVE-2024-20673 | Vulnerability of Microsoft Office Remote Code Execution |
| CVE-2024-21339 | Vulnerability of Windows USB Generic Parent Driver Remote Code Execution |
| CVE-2024-21341 | Vulnerability of Windows Kernel Remote Code Execution |
| CVE-2024-21347 | Vulnerability of Microsoft ODBC Driver Remote Code Execution |
| CVE-2024-21349 | Vulnerability of Microsoft ActiveX Data Objects Remote Code Execution |
| CVE-2024-21350 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21352 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21353 | Vulnerability of Microsoft WDAC ODBC Driver Remote Code Execution |
| CVE-2024-21358 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21359 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21360 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21361 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21363 | Vulnerability of Microsoft Message Queuing ( MSMQ) Remote Code Execution |
| CVE-2024-21365 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21366 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21367 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21368 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21369 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21370 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21372 | Vulnerability of Windows OLE Remote Code Execution |
| CVE-2024-21375 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21376 | Vulnerability of Microsoft Azure Kubernetes Service Confidential Container Remote Code Execution |
| CVE-2024-21378 | Vulnerability of Microsoft Outlook Remote Code Execution |
| CVE-2024-21379 | Vulnerability of Microsoft Word Remote Code Execution |
| CVE-2024-21384 | Vulnerability of Microsoft Office OneNote Remote Code Execution |
| CVE-2024-21391 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21420 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
Privilege Elevation ( 16 CVEs )
| seriousness | |
| CVE-2024-21410 | Privilege Vulnerability Increased on Microsoft Exchange Server |
| significant severity | |
| CVE-2024-21304 | Base Elevation of Privilege Vulnerability by Trusted Compute |
| CVE-2024-21315 | Elevating Privilege Vulnerability with Microsoft Defender for Endpoint Protection |
| CVE-2024-21329 | Increased Privilege Vulnerability for Azure Connected Machine Agents |
| CVE-2024-21338 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21345 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21346 | Privilege Vulnerability Elevation in Win32k |
| CVE-2024-21354 | Increased Privilege Vulnerability as a result of Microsoft Message Queuing ( MSMQ) |
| CVE-2024-21355 | Increased Privilege Vulnerability as a result of Microsoft Message Queuing ( MSMQ) |
| CVE-2024-21371 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21397 | Privilege Vulnerability Improvement in Microsoft Azure File Sync |
| CVE-2024-21401 | Increased Privilege Vulnerability in the Microsoft Entra Jira Single-Sign-OnPlugin |
| CVE-2024-21402 | Privilege Vulnerability Improvement in Microsoft Outlook |
| CVE-2024-21403 | Confidential Container Elevation of Privilege Vulnerability for Microsoft Azure Kubernetes Services |
| CVE-2024-21405 | Increased Privilege Vulnerability as a result of Microsoft Message Queuing ( MSMQ) |
| mildly severe | |
| CVE-2024-21364 | Privilege vulnerability improvement for Microsoft Azure site recovery |
Spoofing ( 10 CVEs )
| significant severity | |
| CVE-2024-20679 | Spoofing vulnerability in Azure Stack Hub |
| CVE-2024-21327 | Cross-site scripting vulnerability with Microsoft Dynamics 365 CustomerEngagement |
| CVE-2024-21328 | Sales Spoofing Vulnerability in Dynamics 365 |
| CVE-2024-21381 | B2C Spoofing Vulnerability in Microsoft Azure Active Directory |
| CVE-2024-21389 | Cross-site scripting vulnerability with Microsoft Dynamics 365 (on-premises ) |
| CVE-2024-21393 | Cross-site scripting vulnerability with Microsoft Dynamics 365 (on-premises ) |
| CVE-2024-21394 | Vulnerability Spoofing Dynamics 365 Field Service |
| CVE-2024-21395 | Cross-site scripting vulnerability with Microsoft Dynamics 365 (on-premises ) |
| CVE-2024-21396 | Sales Spoofing Vulnerability in Dynamics 365 |
| CVE-2024-21406 | Vulnerability Spoofing by Windows Print Spooler |
Service Denial ( 8 CVEs )
| seriousness | |
| CVE-2024-20684 | Denial of Service Vulnerability in Windows Hyper-V |
| significant severity | |
| CVE-2024-21342 | Vulnerability of Windows DNS Client Denial of Service |
| CVE-2024-21343 | Service vulnerability is denied by Windows Network Address Translation ( NAT ) |
| CVE-2024-21344 | Service vulnerability is denied by Windows Network Address Translation ( NAT ) |
| CVE-2024-21348 | Internet Connection Sharing ( ICS) Service Vulnerability Denial |
| CVE-2024-21356 | Service vulnerability is denied by Windows Lightweight Directory Access Protocol ( LDAP ). |
| CVE-2024-21386 | Service vulnerability is denied by .NET |
| CVE-2024-21404 | Service vulnerability is denied by .NET |
Information disclosure ( 5 CVEs )
| seriousness | |
| CVE-2024-21380 | Vulnerability of Microsoft Dynamics Business Central/NAV Information Disclosure |
| significant severity | |
| CVE-2024-20695 | Vulnerability of Business Information Disclosure via Skype |
| CVE-2024-21340 | Information Disclosure Vulnerability in the Windows Kernel |
| CVE-2024-21374 | Android Information Disclosure Microsoft Teams Vulnerability |
| CVE-2024-21377 | Vulnerability of Windows DNS Information Disclosure |
Bypass for security features ( 3 CVEs )
| significant severity | |
| CVE-2024-21362 | Bypass Vulnerability for Windows Kernel Security Features |
| CVE-2024-21412 | Security feature bypass vulnerability for Internet Shortcut Files |
| Severity that is moderate | |
| CVE-2024-21351 | Bypass Vulnerability for Windows SmartScreen Security Features |
Exploitability in Appendix B
This is a list of the February CVEs that Microsoft believes are either already actively exploited in the wild or are more likely to be so within the first 30 days of release. CVE further organizes each list.
| Exploitation found | |
| CVE-2024-21351 | Bypass Vulnerability for Windows SmartScreen Security Features |
| CVE-2024-21412 | Security feature bypass vulnerability for Internet Shortcut Files |
| Within the next 30 days, exploration is more likely. | |
| CVE-2024-21338 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21345 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21346 | Privilege Vulnerability Elevation in Win32k |
| CVE-2024-21357 | Vulnerability of Windows Pragmatic General Multicast ( PGM ) Remote Code Execution |
| CVE-2024-21371 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21378 | Vulnerability of Microsoft Outlook Remote Code Execution |
| CVE-2024-21379 | Vulnerability of Microsoft Word Remote Code Execution |
| CVE-2024-21410 | Privilege Vulnerability Increased on Microsoft Exchange Server |
Products Affected by  , Appendix C
Here is a list of February’s patches, broken down by severity and product family. CVE further organizes each list. Each product family receives a separate listing of the patches that are shared among them.
( 43 CVEs ) Windows
| seriousness | |
| CVE-2024-20684 | Denial of Service Vulnerability in Windows Hyper-V |
| CVE-2024-21357 | Vulnerability of Windows Pragmatic General Multicast ( PGM ) Remote Code Execution |
| significant severity | |
| CVE-2024-21304 | Base Elevation of Privilege Vulnerability by Trusted Compute |
| CVE-2024-21338 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21339 | Vulnerability of Windows USB Generic Parent Driver Remote Code Execution |
| CVE-2024-21340 | Information Disclosure Vulnerability in the Windows Kernel |
| CVE-2024-21341 | Vulnerability of Windows Kernel Remote Code Execution |
| CVE-2024-21342 | Vulnerability of Windows DNS Client Denial of Service |
| CVE-2024-21343 | Service vulnerability is denied by Windows Network Address Translation ( NAT ) |
| CVE-2024-21344 | Service vulnerability is denied by Windows Network Address Translation ( NAT ) |
| CVE-2024-21345 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21346 | Privilege Vulnerability Elevation in Win32k |
| CVE-2024-21347 | Vulnerability of Microsoft ODBC Driver Remote Code Execution |
| CVE-2024-21348 | Internet Connection Sharing ( ICS) Service Vulnerability Denial |
| CVE-2024-21349 | Vulnerability of Microsoft ActiveX Data Objects Remote Code Execution |
| CVE-2024-21350 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21352 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21353 | Vulnerability of Microsoft WDAC ODBC Driver Remote Code Execution |
| CVE-2024-21354 | Increased Privilege Vulnerability as a result of Microsoft Message Queuing ( MSMQ) |
| CVE-2024-21355 | Increased Privilege Vulnerability as a result of Microsoft Message Queuing ( MSMQ) |
| CVE-2024-21356 | Service vulnerability is denied by Windows Lightweight Directory Access Protocol ( LDAP ). |
| CVE-2024-21358 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21359 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21360 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21361 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21362 | Bypass Vulnerability for Windows Kernel Security Features |
| CVE-2024-21363 | Vulnerability of Microsoft Message Queuing ( MSMQ) Remote Code Execution |
| CVE-2024-21365 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21366 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21367 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21368 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21369 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21370 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21371 | Privilege Vulnerability Improvement in the Windows Kernel |
| CVE-2024-21372 | Vulnerability of Windows OLE Remote Code Execution |
| CVE-2024-21375 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21377 | Vulnerability of Windows DNS Information Disclosure |
| CVE-2024-21391 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21405 | Increased Privilege Vulnerability as a result of Microsoft Message Queuing ( MSMQ) |
| CVE-2024-21406 | Vulnerability Spoofing by Windows Print Spooler |
| CVE-2024-21412 | Security feature bypass vulnerability for Internet Shortcut Files |
| CVE-2024-21420 | For SQL Server Remote Code Execution Vulnerability, Microsoft WDAC OLE DB provider |
| CVE-2024-21351 | Bypass Vulnerability for Windows SmartScreen Security Features |
( 8 CVEs ) Azure
| significant severity | |
| CVE-2024-20667 | Vulnerability of Azure DevOps Server Remote Code Execution |
| CVE-2024-20679 | Spoofing vulnerability in Azure Stack Hub |
| CVE-2024-21329 | Increased Privilege Vulnerability for Azure Connected Machine Agents |
| CVE-2024-21376 | Vulnerability of Microsoft Azure Kubernetes Service Confidential Container Remote Code Execution |
| CVE-2024-21381 | B2C Spoofing Vulnerability in Microsoft Azure Active Directory |
| CVE-2024-21397 | Privilege Vulnerability Improvement in Microsoft Azure File Sync |
| CVE-2024-21403 | Confidential Container Elevation of Privilege Vulnerability for Microsoft Azure Kubernetes Services |
| mildly severe | |
| CVE-2024-21364 | Privilege vulnerability improvement for Microsoft Azure site recovery |
8 CVEs of Dynamics 365
| seriousness | |
| CVE-2024-21380 | Vulnerability of Microsoft Dynamics Business Central/NAV Information Disclosure |
| significant severity | |
| CVE-2024-21327 | Cross-site scripting vulnerability with Microsoft Dynamics 365 CustomerEngagement |
| CVE-2024-21328 | Sales Spoofing Vulnerability in Dynamics 365 |
| CVE-2024-21389 | Cross-site scripting vulnerability with Microsoft Dynamics 365 (on-premises ) |
| CVE-2024-21393 | Cross-site scripting vulnerability with Microsoft Dynamics 365 (on-premises ) |
| CVE-2024-21394 | Vulnerability Spoofing Dynamics 365 Field Service |
| CVE-2024-21395 | Cross-site scripting vulnerability with Microsoft Dynamics 365 (on-premises ) |
| CVE-2024-21396 | Sales Spoofing Vulnerability in Dynamics 365 |
Office 5CVEs
| seriousness | |
| CVE-2024-21413 | Vulnerability of Microsoft Office Remote Code Execution |
| significant severity | |
| CVE-2024-20673 | Vulnerability of Microsoft Office Remote Code Execution |
| CVE-2024-21378 | Vulnerability of Microsoft Outlook Remote Code Execution |
| CVE-2024-21379 | Vulnerability of Microsoft Word Remote Code Execution |
| CVE-2024-21384 | Vulnerability of Microsoft Office OneNote Remote Code Execution |
Shared with Visual Studio is.NET ( 1 CVE ).
| significant severity | |
| CVE-2024-21404 | Service vulnerability is denied by .NET |
ASP. CVE ( 1 NET )
| significant severity | |
| CVE-2024-21386 | Service vulnerability is denied by .NET |
Defender ( CVE )
| significant severity | |
| CVE-2024-21315 | Elevating Privilege Vulnerability with Microsoft Defender for Endpoint Protection |
( CVE )Entra
| significant severity | |
| CVE-2024-21401 | Increased Privilege Vulnerability in the Microsoft Entra Jira Single-Sign-OnPlugin |
( 1 CVE ) Exchange
| seriousness | |
| CVE-2024-21410 | Privilege Vulnerability Increased on Microsoft Exchange Server |
CVE version of Outlook 365
| significant severity | |
| CVE-2024-21402 | Privilege Vulnerability Improvement in Microsoft Outlook |
CVE Skype
| significant severity | |
| CVE-2024-20695 | Vulnerability of Business Information Disclosure via Skype |
Android Teams ( 1 CVE )
| significant severity | |
| CVE-2024-21374 | Android Information Disclosure Microsoft Teams Vulnerability |
Shared with ASP is Visual Studio ( 1 CVE ). ( NET )
| significant severity | |
| CVE-2024-21386 | Service vulnerability is denied by .NET |
Advisories and Other Products, Appendix D
Sorted by product, this is a list of advisories and details on additional pertinent CVEs from the February Microsoft release.
Relevant to Chromium/Edge ( 6 CVEs )
| CVE-2024-1059 | Use Chromium: CVE-2024-1059 after free on WebRTC. |
| CVE-2024-1060 | Chromium: CVE-2024-1060 Use it immediately in Canvas. |
| CVE-2024-1077 | Use Chromium: CVE-2024-1077 in Network after free. |
| CVE-2024-1283 | Chromium: CVE-2024–1283 Skia heap buffer overflow |
| CVE-2024-1284 | Chromium: CVE-2024-1284 Use it in Mojo after free. |
| CVE-2024-21399 | Remote code execution vulnerability with Microsoft Edge ( Chromium-based ) |
Relevant to Windows ( one CVE, non-Microsoft release )
| CVE-2023-50387 | MITRE: It is possible to abuse CVE-2023-50387 DNS RRSIGs and DNSKEYs validation to remotely use DNS server resources. |
Relevant to Adobe ( 13 CVEs )
| CVE-2024-20726 | Acrobat Reader security updates are available. |
| CVE-2024-20727 | Acrobat Reader security updates are available. |
| CVE-2024-20728 | Acrobat Reader security updates are available. |
| CVE-2024-20729 | Acrobat Reader security updates are available. |
| CVE-2024-20730 | Acrobat Reader security updates are available. |
| CVE-2024-20731 | Acrobat Reader security updates are available. |
| CVE-2024-20733 | Acrobat Reader security updates are available. |
| CVE-2024-20734 | Acrobat Reader security updates are available. |
| CVE-2024-20735 | Acrobat Reader security updates are available. |
| CVE-2024-20736 | Acrobat Reader security updates are available. |
| CVE-2024-20747 | Acrobat Reader security updates are available. |
| CVE-2024-20748 | Acrobat Reader security updates are available. |
| CVE-2024-20749 | Acrobat Reader security updates are available. |
VulnScan – Automated Triage and Root Cause Analysis of Memory Corruption Issues
Microsoft distributes patches for 73 flaws, including two days of Windows Zero
Reducing hardware vulnerabilities
The first Patch Tuesday of 2024 takes small steps(Opens in a new browser tab)