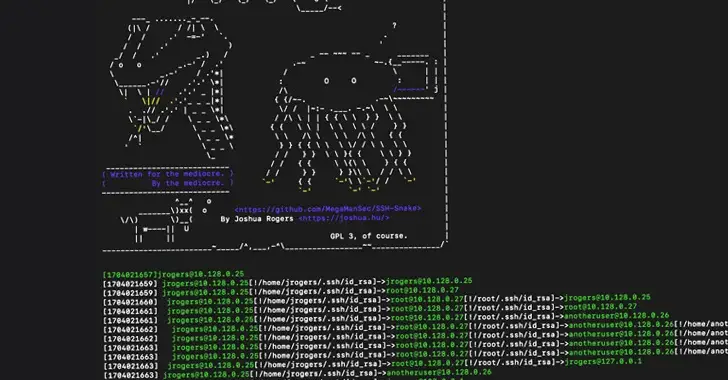
Threat actors have used the recently open-sourced network mapping tool SSH- Snake to carry out malicious activities.
According to Sysdig researcher Miguel Hernández,” SSH-Snake is a self-modifying worm that starts spreading itself throughout the network by exploiting SSH credentials found on an compromised system.”
” To determine its next move, the worm automatically searches through well-known credential locations and shell history files.”
Early in January 2024, SSH-Snake was first made available on Git Hub. Its creator referred to it as a “powerful tool” for automating network traversal with the help of private keys found on systems.
In doing so, it maps out a network’s dependencies in great detail, assisting in figuring out how vulnerable it is to attacks using SSH and private keys that begin with one host. Additionally, it supports the resolution of IPv4 address-multiple domains.
According to the project’s description, it is completely fileless, self-replicating, and propagating. SSH-Snake is actually a worm in many ways because it replicates and disperses as widely as it can between systems.
According to Sysdig, the shell script offers more stealth and flexibility than other typical SSH worms in addition to facilitating lateral movement.
Following the discovery of a command-and-control ( C2 ) server hosting the data, the cloud security company claimed to have seen threat actors using SSH-Snake in real-world attacks to harvest credentials, target IP addresses, and bash command history.
Hernández stated that” SSH-Snake tries to take advantage of the use of SSH keys in order to spread.” Threat actors will be able to penetrate a network further once they establish themselves because it is smarter and more dependable.
When contacted for comment, Joshua Rogers, the creator of SSH-Snake, advised businesses to use the tool to “discover the attack paths that exist- and fix them,” as it gives legitimate system owners a way to spot infrastructure flaws before attackers do.
According to Rogers, “it seems to be widely believed that cyberterrorism simply strikes systems out of the blue, necessitating a reactive approach to security.” ” Systems should be designed and maintained with comprehensive security measures, in my opinion.”
Focus should be placed on those in charge of the infrastructure if a cyber terrorist can access thousands of servers and run SSH-Snake on it with the intention of revitalizing it so that the compromise of one host wo n’t spread to thousands more.
Rogers also drew attention to the “negligent operations” carried out by businesses that create and use insecure infrastructure that are easily breached by a shell script.
The fallout from such a script being executed would be minimized, as well as if SSH-Snake’s actions were manually carried out by an attacker, Rogers continued.
Security teams of businesses concerned about this kind of script taking over their entire infrastructure should perform a complete re-architecture of their systems by trained security specialists, not those who initially created the architecture, rather than reading privacy policies and performing data entry.
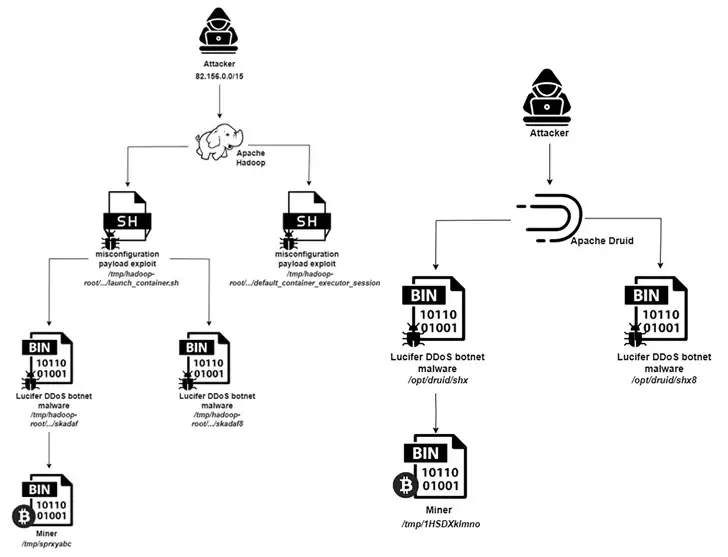
The information was revealed as Aqua unveiled the Lucifer botnet campaign, which uses flaws and misconfigurations in Apache Hadoop and Apache Druid to gather them into a network for mining cryptocurrencies and staging distributed denial-of-service ( DDoS ) attacks.
Palo Alto Networks Unit 42 first reported the hybrid cryptojacking malware in June 2020, highlighting its capacity to compromise Windows endpoints by taking advantage of well-known security flaws.
The cloud security company reported that over the past month, up to 3, 000 different attacks on the Apache big data stack have been found. This includes those who choose to deploy rootkits and miners on Apache Flink instances that are vulnerable.
According to security researcher Nitzan Yaakov, the attacker uses pre-existing configurations and vulnerabilities in those services to carry out the attack.
” Many users and contributors use Apache open-source solutions frequently.” Attackers might see this widespread use as a chance to attack them with limitless resources.