In response to widespread and active exploitation by numerous threat actors, CISA issued this year’s first emergency directive directing Federal Civilian Executive Branch (FCEB ) agencies to immediately mitigate two Ivanti Connect Secure and Ivani Policy Secure zero-day flaws.
Given that numerous attacks have been launched against vulnerable Ivanti devices since December, including the CVE- 2023-46805 authentication bypass and command injection vulnerabilities, and that the vendor has not yet released security patches, this development is to be expected.
The cybersecurity agency stated on Friday that “CISA has determined that these conditions pose an unacceptable risk to Federal Civilian Executive Branch (FCEB ) agencies and require emergency action.”
This conclusion is based on the widespread use of vulnerabilities by various threat actors, the prevalence of the affected products within the federal enterprise, how likely it is that agency information systems will be compromised, what would happen if it were to happen, and how complicated the suggested mitigations would be.
Actions are required for ED 24-01
Federal agencies must now quickly carry out Ivanti’s publicly disclosed mitigation measures to thwart attack attempts, as directed by emergency directive ED 24-01.
Additionally, the agencies must utilize Ivanti’s External Integrity Checker Tool and:
- Immediately report indications of compromise to CISA through central@cisa.dhs.gov
- Remove tainted goods from agency networks. Start an incident analysis, create forensic hard drive images to protect data from the compromised devices, and look for signs of further compromise.
- Apply Ivanti’s mitigations to a compromised product, restore it to factory default settings, and remove the attack vector.
They must first follow Ivanti’s recovery instructions in order to fully restore impacted appliances and put them back into service:
- Any certificates that have been stored should be revoked and reissued.
- Change the admin enable password.
- API keys that are stored should be reset.
- Reset the password for any local user defined on the gateway, including service accounts for configurations of auth servers.
- Apply updates to the affected products as soon as they are made available and no later than 48 hours after Ivanti releases them that address the two vulnerabilities mentioned in this Directive.
- Report to CISA, using the provided template, a full inventory of all Ivanti Policy Secure and Connect Secure products used on agency networks, along with information on actions taken and outcomes, one week after this Directive was issued.
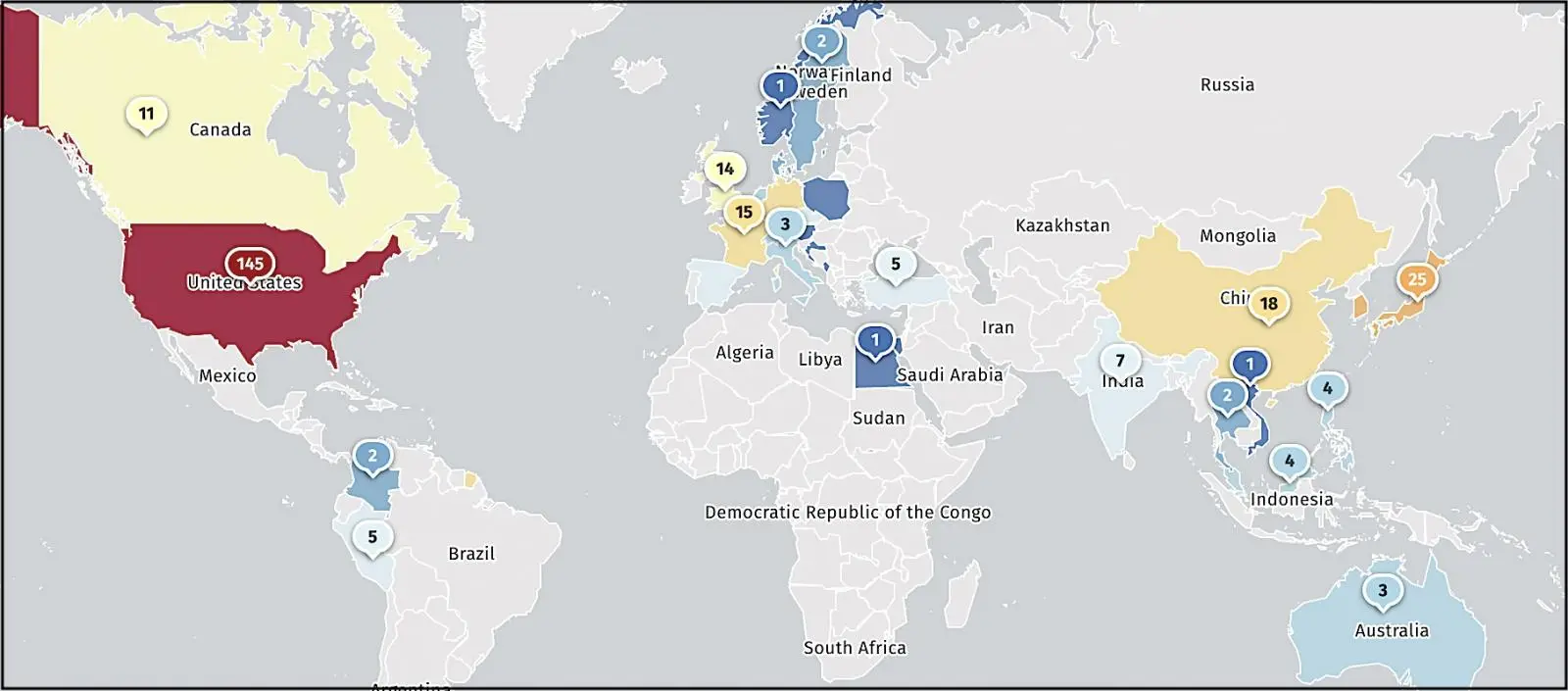
More than 16, 200 ICS VPN appliances are currently exposed online by the threat monitoring service Shadowserver, with over 4,700 of them in the US ( Shodan also observes nearly 17, 000 Internet-exposed Ivanti CIS devices ).
More than 420 compromised Ivanti Connect Secure VPN instances, including those discovered on January 18, are also being tracked by Shadowserver.
actively used to drop malware and crypto miners
According to threat intelligence provider Volexity, one of the attackers—a suspected Chinese state-backed threat actor identified as UTA0178 and UNC5221—has already used a GIFTEDVISITOR webshell variant to backdoor more than 2,100 Ivanti appliances.
Five unique malware strains were discovered by Mandiant on systems of compromised customers with the intention of stealing credentials, deploying webshells, and spreading malicious payloads.
The threat actor has been stealing information from compromised networks, including account and session data.
Government and military departments worldwide, national telecom companies, defense contractors, technology firms, banking, finance, and accounting organizations, international consulting groups, as well as aerospace, aviation and engineering firms have all been identified as potential victims.
From small businesses to some of the biggest companies in the world, including numerous Fortune 500 companies from various industry sectors, they range greatly in size.
Volexity and GreyNoise have also reported seeing attackers deploying XMRig cryptocurrency miners and Rust-based malware payloads that are still pending analysis.
Related Cybersecurity Threat and Awareness Blogs:
Ivanti Zero-Day Exploits: CISA Issues Emergency Directive to Federal Agencies
Week 2 of The Good, the Bad, and the Ugly in Cybersecurity











