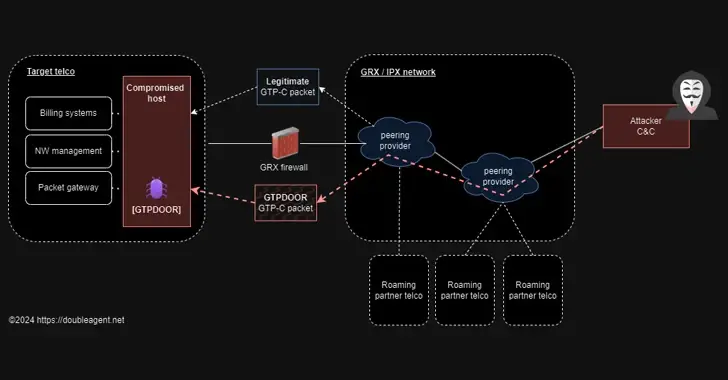
GTPDOOR, a new Linux malware that is intended to be used in telecom networks close to GPRS roaming exchanges ( GRX ), has been discovered by threat hunters.
The <a href="https://doubleagent.net/telecommunications/backdoor/gtp/2024/02/27/GTPDOOR-COVERT-TELCO-BACKDOOR” rel=”noopener” target=”_blank”>malware’s use of the GPRS Tunnelling Protocol ( GPP ) for command-and-control ( C2 ) communications is novel.
Subscribers can access their GPRS services when their home mobile network is unavailable through GPRS roaming. A GRX that uses GTP to transport roaming traffic between the visited and the home Public Land Mobile Network ( PLMN) facilitates this.
The backdoor is likely connected to a known threat actor identified as LightBasin ( also known as UNC1945 ), according to security researcher haxrob, who found two GTPDOORartifacts from China and Italy that were previously made public by CrowdStrike in October 2021 in connection with a string of attacks aimed at stealing subscriber data and call metadata.
The researcher claimed that the first thing GTPDOOR does is is process- name stomp itself when it is run, changing its process name to” syslog ]” in disguise as syslog invoked from the kernel. The implant will be able to receive UDP messages hitting the network interfaces by suppressing child signals before opening a raw socket.
Put another way, GTPDOOR enables a threat actor to contact a compromised host by sending GTP-C Echo Request messages with a malicious payload.
This magical GTP-C Echo Request message serves as a means of delivering a command to an infected machine back to the remote host.
The researcher remarked that GTPDOOR” can be covertly probed from an external network to elicit a response by sending a TCP packet to any port number.” A crafted empty TCP packet with information about whether the host’s host port was open or responding is returned if the implant is active.
This implant appears to be built on compromised hosts that directly interact with the GRX network; these hosts communicate with other telecommunications operator networks using the GRX.