For fifty years, Chinese hackers have been operating unnoticed in critical infrastructure in the United States
Volt Typhoon, a hacking group funded by the Chinese government, has been incorporated into some of the nation’s most important infrastructure networks for at least five years, according to the U. S. government on Wednesday.
The U.S. and Guam water and wastewater systems, energy, transportation, and communications sectors are among the threat actor’s targets.
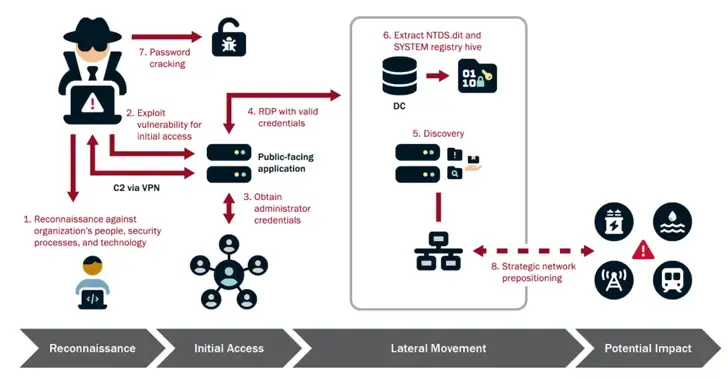
According to the U.S. government, Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT assets to disrupt functions. This is in contrast to traditional cyber espionage or intelligence gathering operations.
In the event of a significant crisis or conflict with the United States, the goal is to position themselves on IT networks by remaining persistent and gradually understanding the target environment for disruptive or destructive cyberattacks against U.S. critical infrastructure.
Other countries that are a part of the Five Eyes ( FVEY ) intelligence alliance, which includes Australia, Canada, New Zealand, and the United Kingdom, supported the joint advisory that was published by the Cybersecurity and Infrastructure Security Agency ( CISA ), National Security Administration ( NSA ), and Federal Bureau of Investigation ( FBI ).
Bronze Silhouette, Insidious Taurus, UNC3236, Vanguard Panda, and Voltzite are other names for the covert China-based cyber espionage organization that is thought to have been active since June 2021.
It was first discovered in May 2023 when FVEY and Microsoft revealed that the hacking team had been able to penetrate U.S. and Guam’s critical infrastructure organizations for protracted periods of time without being discovered, primarily by using living-off-the-land ( LotL ) techniques.
Even by organizations with more sophisticated security postures, it can be challenging to distinguish between malicious activity and legitimate system and network behavior thanks to this type of tradecraft, known as “living off the land,” according to the U. K. National Cyber Security Centre (NCSC ).
Using multi-hop proxies like KV-botnet to route malicious traffic through a network of compromised routers and firewalls in the U.S. to conceal its true origins is another distinctive strategy used by Volt Typhoon.
In a report that was released in June 2023, the cybersecurity company CrowdStrike criticized its reliance on an extensive collection of open-source tools to combat only one group of victims in order to accomplish its strategic objectives.
The agencies noted that” Volt Typhoon actors conduct extensive pre-exploitation reconnaissance to learn about the target organization and its environment, tailor their tactics, techniques, and procedures ( TTPs ) to the victim’s environment.
The group also makes use of reliable financial records and robust operational security, which, when combined, enable long-term undiscovered persistence.
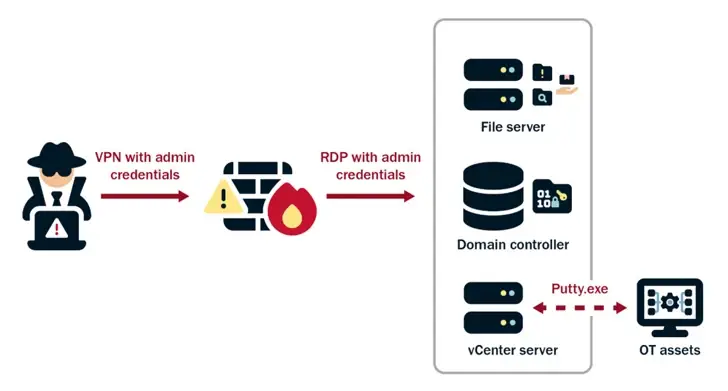
Additionally, it has been reported that the nation-state has used privilege escalation flaws to try and gain administrator credentials within the network. They then use the elevated access to facilitate lateral movement, reconnaissance, and full domain compromise.
Retaining access to the compromised environments while “methodically” re-targeting them over time to confirm and expand their unauthorized accesses is the campaign’s ultimate objective. The agencies claim that their meticulous approach is demonstrated by the numerous times they have accessed domain credentials to guarantee access to up-to-date and legitimate accounts.
The actors employ LOTL techniques in addition to using stolen account credentials to prevent malware artifacts from being left on systems that might trigger alerts, according to CISA, FBI, and NSA.
They are able to maintain long-term, undiscovered persistence thanks to their strong emphasis on operational security and stealth. Targeted log deletion to hide their activities in the compromised environment also improves Volt Typhoon’s operational security.
The Citizen Lab recently unveiled a network of at least 123 websites posing as regional news organizations in 30 European, Asian, and Latin American nations that are promoting pro-China content as part of an extensive influence campaign involving Beijing public relations firm Shenzhen Haimaiyunxiang Media Co., Ltd.
The Toronto-based digital watchdog, known as PAPERWALL, claimed that despite having different operators and distinct TTPs, the influence operation is similar to HaiEnergy.
The ephemeral nature of PAPERWALL’s most aggressive components, which ensure that articles criticizing Beijing are routinely removed from these websites after they are published, is a key characteristic of the network of websites, according to the Citizen Lab.
It is a typical bias and double standard to claim that the pro-China contents and reports are “disinformation” and to call the anti-Chinese ones” true information,” the spokesperson for China’s embassy in Washington told Reuters.