Researchers studying cybersecurity have discovered an “implementation vulnerability” that allows for the reconstruction of encryption keys and the decryption of Rhysida ransomware-protected data.
Researchers from Kookmin University and the Korea Internet and Security Agency (KISA ) released their findings last week.
We were able to regenerate the malware’s encryption key thanks to a thorough analysis of Rhysida Ransomware, according to the researchers.
The ransomware strain, which first appeared in May 2023, has now been successfully decrypted for the first time thanks to this development. KISA is distributing a recovery tool.
After Magniber v2, Ragnar Locker, Avaddon, and Hive, the study is also the most recent to use implementation flaws in ransomware to decrypt data.
Rhysida, a ransomware group with similarities to Vice Society, uses double extortion to pressure victims into paying up by threatening to reveal their stolen data.
Threat actors were criticized for planning opportunistic attacks on the government sectors, manufacturing, information technology, and education in an advisory released by the U.S. government in November 2023.
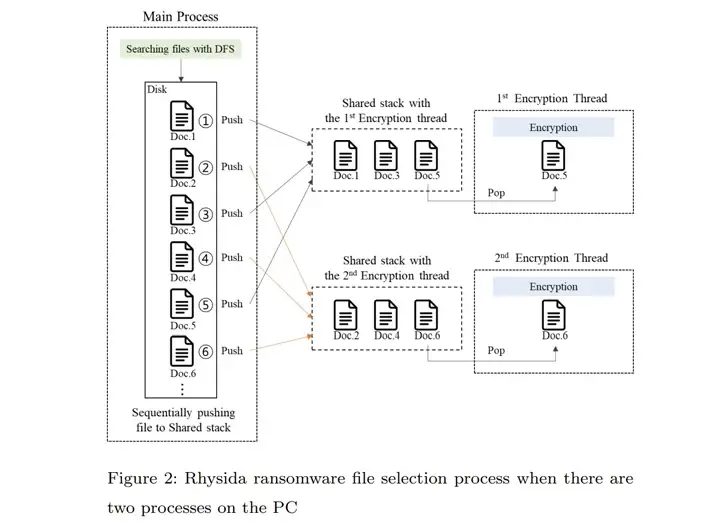
The ransomware uses LibTomCrypt for encryption and parallel processing to speed up the process, according to a thorough analysis of its internal workings. In order to avoid being discovered by security solutions, intermittent encryption ( also known as partial encryption ) has also been discovered.
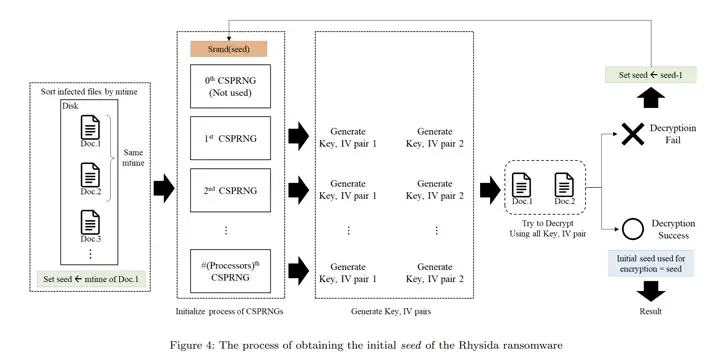
According to the researchers,” Rhysida ransomware generates the encryption key using a cryptographically secure pseudo-random number generator ( CSPRNG ). To produce random numbers, this generator employs a cryptographically secure algorithm.
The CSPRNG is specifically based on the LibTomCrypt library‘s ChaCha20 algorithm, which also generates random numbers that are correlated to the frequency of Rhysida ransomware.
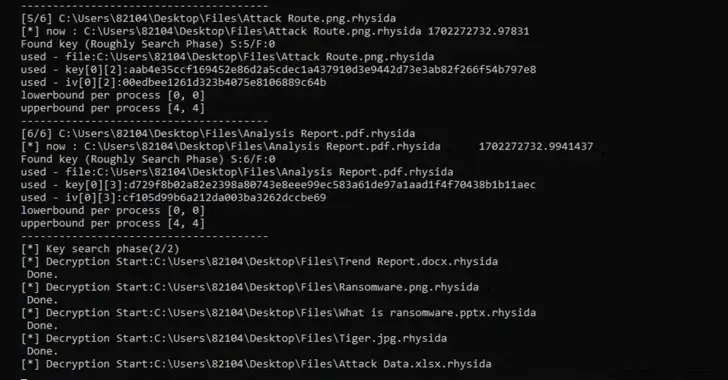
Despite the random number’s predictability, the main Rhysida ransomware process compiles a list of encrypted files, which is then referenced by various threads that are made to encrypt the files simultaneously and sequentially.
The researchers observed that the Rhysida ransomware’s encryption thread produces 80 bytes of random numbers when encrypting a single file. The encryption key and initialization vector for these are the first 48 bytes.
The researchers claimed that they were able to recover the data without having to pay a ransom by using these observations as their point of reference. They also identified the “randomized” order in which the files were encrypted.
The researchers came to the conclusion that even though the scope of these studies is constrained, it is crucial to recognize that some ransomwares can be decrypted successfully.
Update
Security researcher Fabian Wosar claimed that “at least three other parties, who chose to circulate it in private rather than seeking publication and alerting Rhysida about their problem,” discovered the flaws after the story was published.
According to Wosar,” Avast discovered the vulnerability in October of last year, the French CERT wrote and released a private paper about it in June. We have since decrypted hundreds of systems, but I’m not aware of the Avast or CERT data.
A word of caution: The paper only covers the Rhysida ransomware in WindowsPE. The ESXi and PowerShell payloads are exempt from this rule.