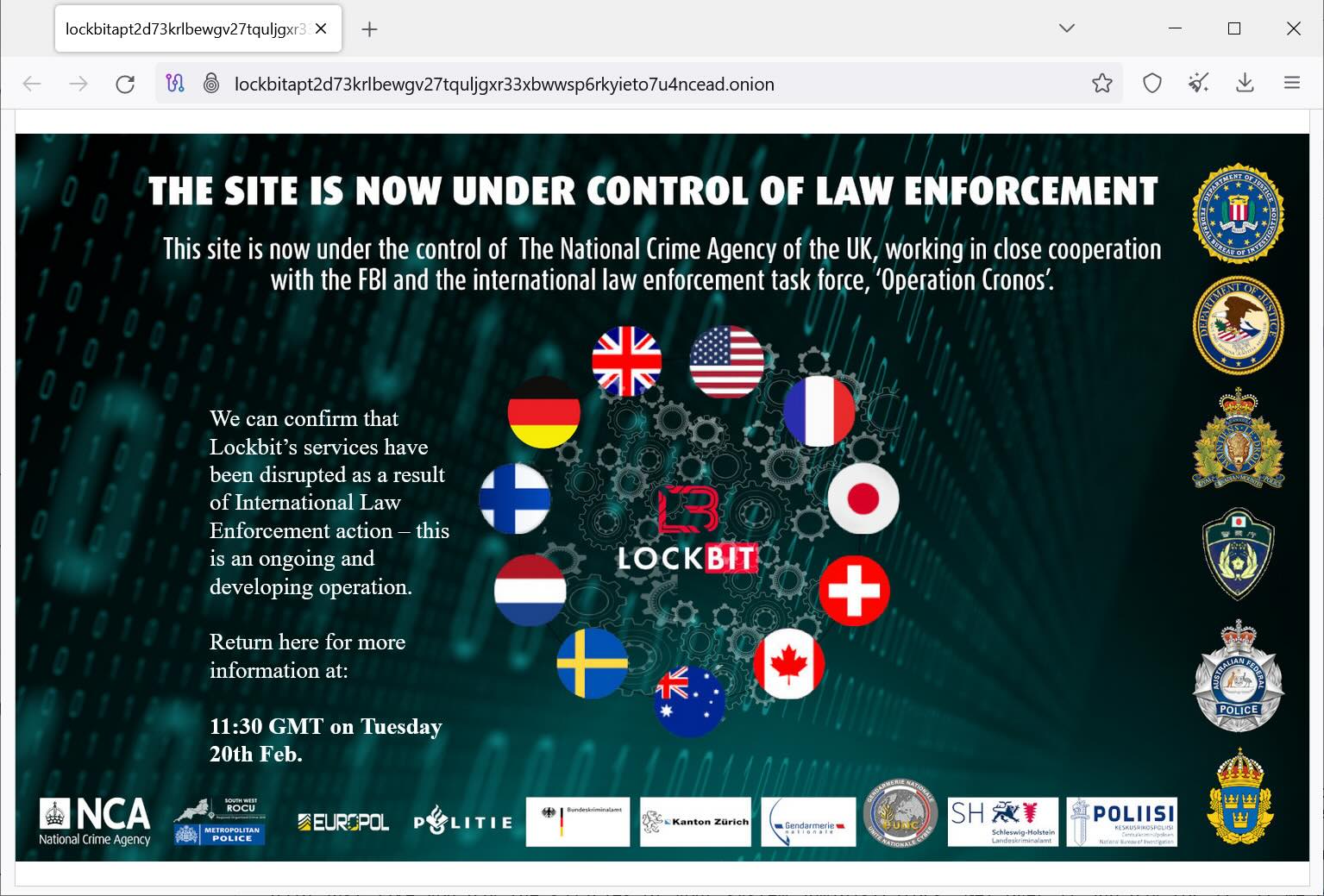
In a joint operation known as” Operation Cronos,” law enforcement organizations from 11 nations have disrupted the infamous LockBit ransomware operation.
The National Crime Agency of the United Kingdom now has control of LockBit, according to a banner on the website dedicated to data leaks.
” Law enforcement is now in charge of the website.” The National Crime Agency of the UK is now in charge of this website.” The banner reads,” Working closely with the FBI and the international law enforcement task force, Operation Cronos.”
This is an ongoing and growing operation, and we can confirm that Lockbit’s services have been disrupted as a result of international law enforcement action.
Some of the other dark web sites used by the gang ( including those used to host data and send private messages to them ) are still operational even though Lockbit’s leak site is no longer accessible and displays the seizure banner embedded below or an” Unable to connect “error saying the connection was refused.
Additionally, BleepingComputer has confirmed that although LockBit’s ransom negotiation sites are offline, the NCA has not yet sent a seizure message.
The NCA can vouch for the fact that international law enforcement action has disrupted LockBit services. According to a spokesperson for the NCA, this operation is still ongoing and growing.
Tomorrow at 12:30 CET, a joint press release is anticipated from the law enforcement organizations behind Operation Chronos.
A threat actor known as LockBitSupp, who uses the Tox messaging service to communicate, is in charge of the Lockbit operation. A message stating that the FBI used a PHP exploit to access the servers of the ransomware operation can now be seen in his account status on the service.
The translated status message from LockBitSupp reads,” BBC f****d up servers via PHP, backup servers without PHP ca n’t be touched.”
Since its launch in September 2019, the LockBit ransomware as a service ( RaaS ) operation has focused on numerous well-known organizations all over the world.
The City of Oakland, the American automaker Continental, and the Italian Internal Revenue Service are among LockBit’s victims.
After Infosys McCamish Systems ( IMS ), one of Bank of America’s service providers, was hacked in an attack claimed by the LockBit ransomware gang, the company most recently issued a warning to customers that their personal information had been compromised.
Following up to 1,700 attacks since 2020, the LockBit gang has extorted at least$ 91 million from U.S. organizations, according to a joint advisory released in June by US cybersecurity authorities and partners around the world.
Law enforcement has recently taken control of the Tor payment and data leak sites for Hive and ALPHV ( BlackCat ) ransomware.
Update : LockBit disruption was confirmed by an added NCA statement on February 19, 17 :20EST.