Silver SAML, a new attack strategy developed by researchers in cybersecurity, is capable of succeeding even when Golden SAML mitigations have been used.
In a report shared with The Hacker News, Semperis researchers Tomer Nahum and Eric Woodruff claimed that Silver SAML “enables the exploitation of SAML to launch attacks against applications configured to use it for authentication, such as Salesforce.”
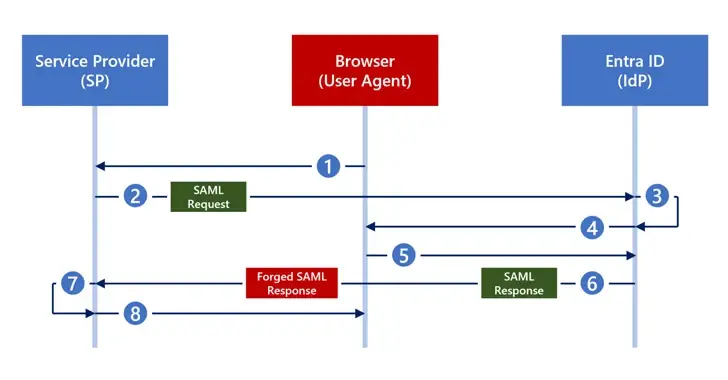
CyberArk first documented Golden SAML ( short for Security Assertion Markup Language ) in 2017. In a nutshell, the interoperable authentication standard is misused to impersonate almost any person in an organization, which is the attack vector.
Similar to the Golden Ticket attack, it enables attackers to gain any privileges, gain unauthorized access to any service in a federation, and maintain their composure in a covert manner.
Security researcher Shaked Reiner noted at the time that Golden SAML “introduces to a federation the benefits that golden ticket offers in a Kerberos environment” in addition to gaining any kind of access to stealthily maintaining persistency.
Rarely have there been real-world attacks that make use of this technique, with SolarWindsinfrastructure‘s first recorded use being to forge SAML tokens using hacked SAML token signing certificates.
In a March 2023 intrusion to access an unnamed target’s cloud resources without the need for any password, an Iranian threat actor codenamed Peach Sandstorm also used Golden SAML, according to Microsoft’s September 2023 disclosure.
The most recent approach, which does n’t require Active Directory Federation Services ( AD FS), works with an identity provider ( IdP ) similar to Microsoft Entra ID ( previously Azure Active Directory ). Organizations have been given a moderate-severe threat due to it.
According to the researchers,” Microsoft provides a self-signed certificate for SAML response signing” with Entra ID. Organizations can also make the choice to use an externally generated certificate, such as those from Okta. That choice poses a security risk, though.
” Any attacker who obtains the private key to any externally generated certificate can forge any SAML response they want and use the same private key that Entra ID holds to sign the response.” The attacker can then access the application as any user with this type of fake SAML response.
The company stated that the issue does not qualify for immediate servicing, but that it will take appropriate action to protect customers after its responsible disclosure to Microsoft on January 2, 2024.
Organizations are required to only use Entra ID self-signed certificates for SAML signing purposes despite the lack of any evidence that Silver SAML has been used in the wild. To create custom SAML responses, Semperis has also provided a proof-of-concept ( PoC ) dubbed SilverSAMLForger.
According to the researchers, “organizations can monitor Entra ID audit logs for changes to PreferredTokenSigningKeyThumbprint under ApplicationManagement.”
” You will need to add service principal credential events that relate to the service principal.” You will need to check whether the audit events are legitimate because the rotation of expired certificates is a common practice. Implementing change control procedures to document rotational events can help to reduce confusion during rotational events.