In a new campaign launched in November 2023, the Android banking Trojan Anatsa has broadened its focus to include Slovakia, Slovenia, and Czechia.
Despite Google Play’s improved detection and protection mechanisms, some campaign droppers were able to take advantage of the accessibility service, according to a report from ThreatFabric that was distributed to The Hacker News.
” Every dropper in this campaign has shown that Android 13’s restricted accessibility service settings can be bypassed.” Five droppers are involved in the campaign overall, and there have been more than 100,000 installations.
Anatsa, also referred to as TeaBot and Toddler, is a well-known Google Play Store application that is distributed under the guise of ostensibly innocent apps. By getting around Google’s security measures that try to give sensitive permissions, these apps, known as droppers, make it easier to install malware.
The Dutch mobile security company unveiled an Anatsa campaign in June 2023 that used dropper apps that had been downloaded more than 30 000 times on the Play Store to target banking customers in the United States, United Kingdom, Germany, Austria, and Switzerland at least since March 2022.
Anatsa is equipped with the ability to fully control infected devices and carry out victim-specific actions. Additionally, it has the ability to steal credentials and start shady deals.
The most recent iteration, which was seen in November 2023, is similar in that one of the droppers,” Phone Cleaner- File Explorer,” ( package name” com ), pretended to be a phone cleaner app. volabs. and used versioning as a technique to introduce its malicious behavior ( androidcleaner ).
The app can still be downloaded from other shady third-party sources even though it is no longer accessible from the official Android storefront.
The app is thought to have received about 12, 000 downloads between November 13 and November 27, when it was unpublished, according to data from the app intelligence platform AppBrain.
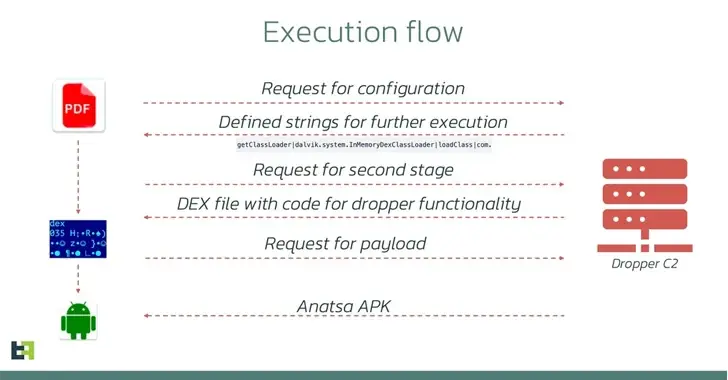
According to ThreatFabric researchers, the app initially appeared to be safe, contained no malicious code, and engaged in no harmful activities with its accessibility service.
Malicious code was added to the update a week after it was released, though. The AccessibilityService functionality was changed by this update, allowing it to carry out malicious actions like clicking buttons automatically when it receives a configuration from the [command-and-control ] server.
Although other droppers used in the campaign have been found to be manufacturer agnostic, the dropper’s abuse of the accessibility service is tailored to Samsung devices, suggesting that it was initially intended to only target Samsung handsets.
By mimicking the method used by markets to install new applications without having their access to accessibility service functionalities disabled, as previously seen in the case of dropper services like SecuriDropper, the droppers can also get around Android 13’s restricted settings.
ThreatFabric claimed that these actors frequently change their focus and prefer focused attacks on particular regions to a global spread. They are able to focus on a small number of financial organizations thanks to their targeted approach, which quickly results in an increase in fraud cases.
In order to replace destination wallet addresses with actor-controlled ones and carry out illicit asset transfers, Fortinet FortiGuard Labs has described another campaign that distributes the SpyNote remote access trojan.
This malware abuses the accessibility API, according to security researcher Axelle Apvrille, like a lot of Android malware today. The Accessibility API is used in this SpyNote sample to target well-known cryptocurrency wallets.