After October 2023, hackers with Iranian and Hezbollah support staged cyberattacks aimed at reducing public support for the Israel-Hamas war.
This includes malicious attacks on important Israeli organizations, hack-and-leak operations against Israeli and American entities, intelligence-stealing phishing campaigns, and information operations to sway public opinion against Israel.
In the six months prior to the attacks on October 7, Google reported that nearly 80 % of all government-sponsored phishing attacks against Israel were carried out by Iran.
The tech behemoth claimed that “hack-and-leak and information operations remain a key component in these and related threat actors ‘ efforts to telegraph intent and capability throughout the war, both to their adversaries and to other audiences that they seek to influence.”
The Israel-Hamas conflict is notable for the fact that, in contrast to the Russo-Ukranian War, the cyber operations appear to be carried out independently of the kinetic and battlefield actions.
According to the company, these cyber capabilities can be quickly and affordably used to fight regional rivals without engaging in direct military conflict.
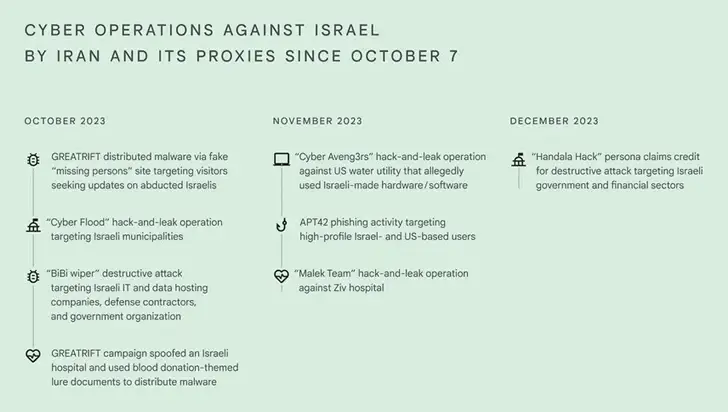
According to reports, GREATRIFT ( also known as UNC4453 or Plaid Rain ), one of the Iran-affiliated organizations, spread malware by using a fictitious “missing persons” website to target visitors looking for information on kidnapped Israelis. As a distribution vector, the threat actor also used lure documents with blood donation themes.
In order to launch destructive attacks against Israel and remove files from Windows and Linux systems, respectively, at least two hacktivist personas by the names of Karma and Handala Hack have used wiper malware strains like BiBi- Windows Wiper, ChillWIP, and COOLWIPE.
In a phishing campaign carried out in late October and November 2023, Charming Kitten, another Iranian nation-state hacking group ( also known as APT42 or CALANQUE), used POWERPUG to target media and non-governmental organizations ( NGOs ).
PowerLess, BellaCiao, POWERSTAR ( also known as GorjolEcho ), NokNok, and BASICSTAR are the most recent backdoors the enemy has added to its long list.
On the other hand, weeks prior to the attacks on October 7, Hamas-linked organizations tried to trick Israeli software engineers into downloading SysJoker malware by using coding assignment decoys. BlackATOM, a threat actor, is credited with starting the campaign.
According to Google,” the attackers [ …] pretended to be employees of legitimate businesses and used LinkedIn to invite targets to apply for freelance positions in software development.” Israel’s aerospace and defense sector, as well as its military, software engineers, were among the targets.
The tech behemoth noted that Hamas cyber actors used social engineering to deliver remote access trojans and backdoors like MAGNIFI to target users in Palestine and Israel, which has been connected to BLACKSTEM ( also known as Molerats ), and that their strategies were straightforward but effective.
The use of spyware on Android phones that can collect sensitive data and expose it to attacker-controlled infrastructure adds another dimension to these campaigns.
The Hamas-affiliated actor DESERTVARNISH, also known as Arid Viper, Desert Falcons, Renegade Jackal, and UNC718, is the creator of the malware strains MOAAZDROID and LOVELYDOOID. Cisco Talos had previously published information about the spyware in October 2023.
With the MYTHDROID ( also known as AhMyth ) Android remote access trojan and a specialized spyware called SOODOID for intelligence gathering, state-sponsored organizations from Iran, such as UNC1530, have also been seen targeting mobile devices in Israel.
According to Google, who has since removed the apps from the digital marketplace,” MYSTICDOME distributed SOLODROID using Firebase projects that 302- redirected users to the Play store, where they were prompted to install the spyware.”
A trojanized version of the legitimate Red Alert app, which is used in Israel to alert people of impending rocket attacks and exfiltrates contacts, messaging information, and location, was also highlighted by Google. SMS phishing messages that purported to be police were used to spread it.
Iran has also been impacted by the ongoing conflict, with an actor named Gonjeshke Darande ( predatory sparrow in Persian ) disrupting the country’s vital infrastructure in December 2023. The Israeli Military Intelligence Directorate is thought to be connected to the persona.
According to Microsoft, Iranian government-affiliated actors “launched a series of cyberattacks and influence operations ( IO ) intended to aid the Hamas cause and weaken Israel and its political allies and business partners.”
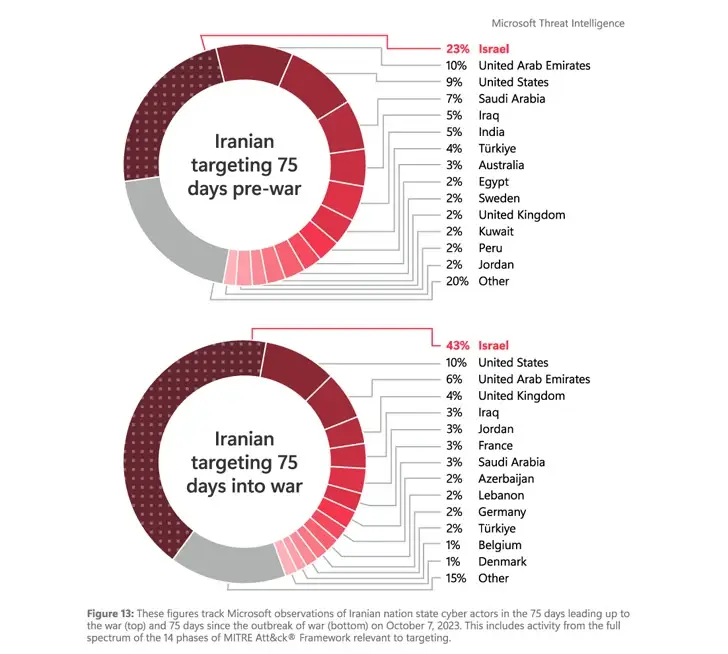
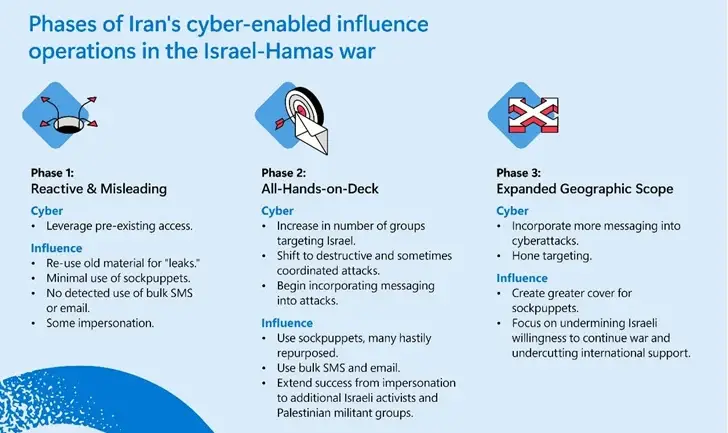
Redmond concurred with Google’s assessment that the attacks became “increasingly targeted and destructive and IO campaigns grew increasingly sophisticated and inauthentic” after the war started, describing their early-stage cyber and influence operations as reactive and exploitative.
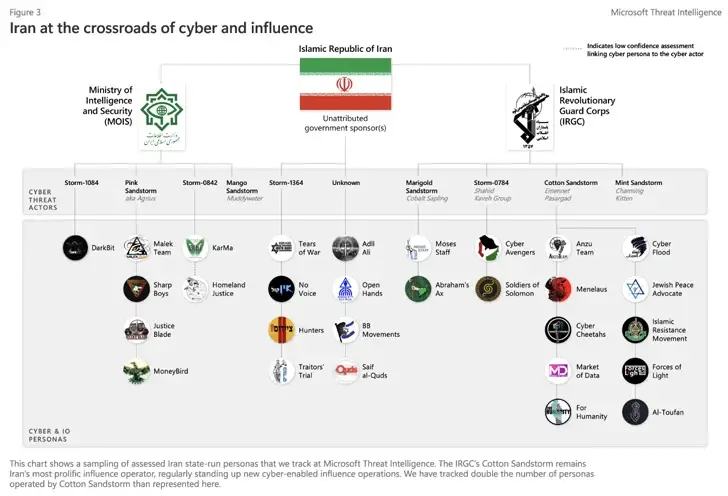
Microsoft reported that it saw cooperation among Iran-affiliated groups like Pink Sandstorm ( also known as Agrius ) and Hezbollah cyber units in addition to ramping up and broadening their attack focus beyond Israel to include nations that Iran perceives as aiding Israel, such as Albania, Bahrain, and the U.S.
According to Clint Watts, general manager at the Microsoft Threat Analysis Center ( MTAC ), collaboration lowers the barrier to entry by enabling each group to contribute existing capabilities and eliminates a single group’s need to create an extensive range of tooling or tradecraft.
The U.S. recently launched a cyberattack against MV Behshad, an Iranian military ship that was gathering information on cargo ships in the Red Sea and the Gulf of Aden, according to NBC News last week.
In order to “foment instability in target countries,” various contracting firms in Iran manage and operate hacking personas and front groups, according to a report from Recorded Future published last month.
In the early stages of the war, Iranian groups hurried to carry out—or merely fabricate—operations, but more recently, they have slowed down, giving them more time to gain desired access or create more complex influence operations, according to Microsoft.