Hackers using the Google Cloud Run service to distribute enormous amounts of banking Trojans like Astaroth, Mekotio, and Ousaban are being warned by security researchers.
Users can deploy frontend and backend services, websites, and applications using Google Cloud Run without having to worry about infrastructure management or scaling.
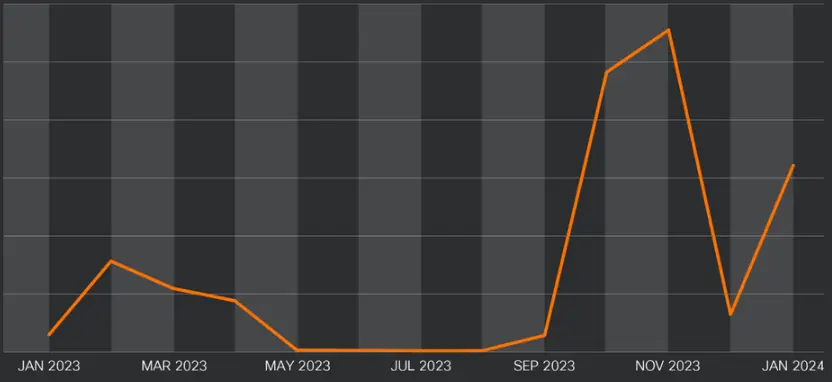
Beginning in September 2023, Brazilian actors began using  , MSI installer files to deploy malware payloads, which led to a significant increase in malware distribution using Google’s service, according to Cisco Talos researchers.
According to the researchers ‘  report, Google Cloud Run has recently attracted cybercriminals due to its affordability and capacity to get around traditional security restrictions and blocks.
chain of attacks
Phishing emails sent to potential victims are the first step in the attacks. These emails are designed to pass for legitimate invoices, financial statements, or tax and local government messages.
According to the researchers, the majority of the campaign’s emails are written in Spanish because they are directed at Latin American nations, though Italian is occasionally used.
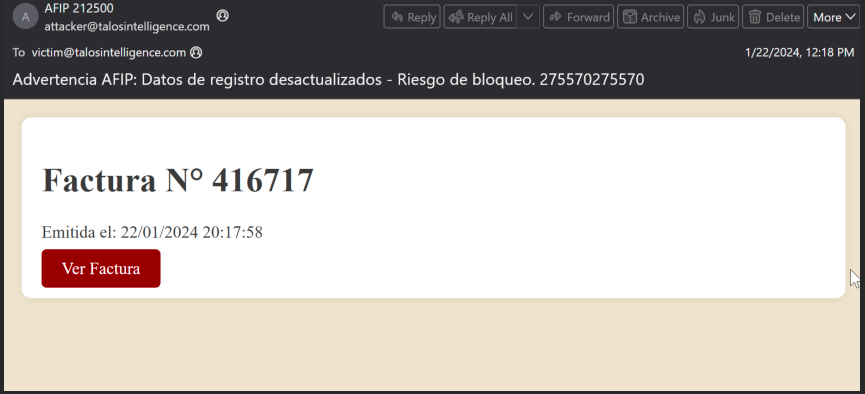
Links and nbsp in the emails point to malicious websites hosted on Google Cloud Run.
The delivery of payloads may occasionally use MSI files.  , In other instances, the service sends a 302 redirect to the location of Google Cloud Storage, which houses an malicious MSI file-containing ZIP archive.
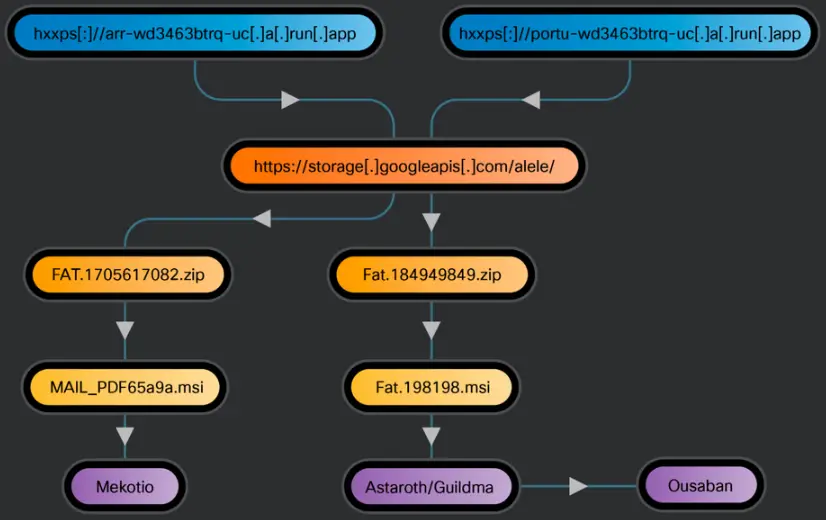
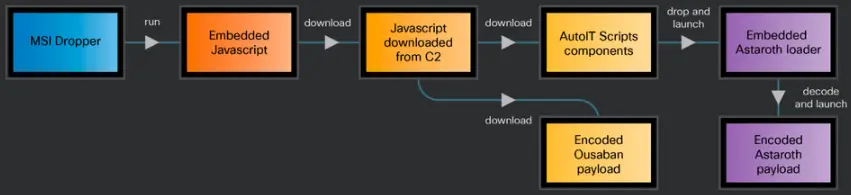
New components and payloads are downloaded and run on the system when the victim executes malicious MSI files.
In the cases mentioned, the legitimate Windows tool” BITSAdmin” is used to deliver the second-stage payload.
Finally, by adding LNK files (‘ sysupdates ‘ ), the malware creates persistence on the victim’s computer to withstand reboots. random_string>, setup<. lnk ‘ ) in the Startup folder, set up to run the AutoIT infection script ( PowerShell command ).
information on malware
Three banking Trojans—Astaroth/Guildma, Mekotio, and Ousaban—are used in the campaigns that misuse Google Cloud Run. Each one aims to covertly infiltrate systems, create persistence, and extract private financial information that could be used to seize control of bank accounts.
Astaroth has cutting-edge evasion methods. Initially concentrating on Brazilian victims , it now focuses on more than 300 financial institutions in 15 Latin American nations. The malware recently began gathering information for cryptocurrency exchange services.
Astaroth uses keylogging, screen capture, and clipboard monitoring to intercept and manipulate internet traffic in order to obtain banking credentials in addition to stealing sensitive data.
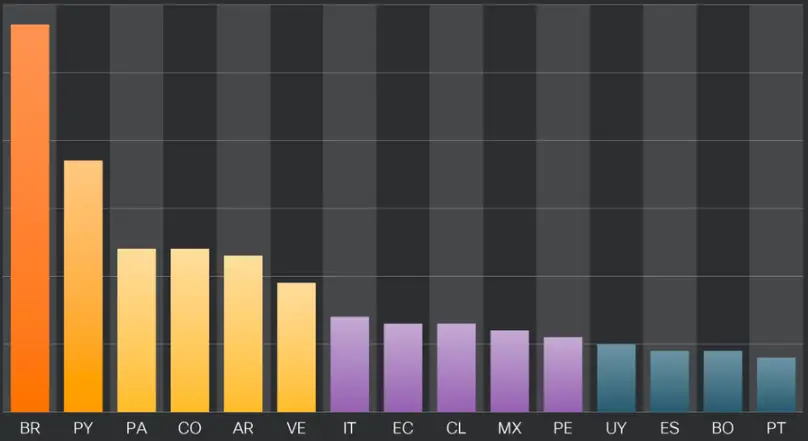
Mekotio, which focuses on the Latin American region, has been active for a while as well.
It has a reputation for committing fraud, stealing personal information, and banking credentials. Additionally, it has the ability to change web browsers so that users are taken to malicious websites.
Finally, Ousaban is a banking Trojan that uses fictitious ( i .e., cloned )  , banking portals, to keylogger, screenshot, and phishing for banking credentials.
Ousaban is delivered at , a later stage of the Astaroth infection chain, according to Cisco Talos, suggesting that the two malware families ‘ operators may have collaborated or that one threat actor may be in charge of both.
By the time this article was published, we had not received a response from Google regarding the company’s plans to counteract this threat.











