Researchers studying the Alpha ransomware payload, modus operandi, discovered, and nbsp are comparing it to the now-defunct Netwalker operation in terms of security.
Between October 2019 and January 2021, Netwalker was a well-known ransomware-as-service ( RaaS ) user. When law enforcement seized its dark web sites, its operators went silent.
In February 2023, the Alpha ransomware operation ( not to be confused with ALPHV/BlackCat ) debuted, but it maintained a low profile, did n’t advertise on hacker forums, and its users only occasionally launched attacks.
When the organization recently launched a data leak site to publish files taken from compromised networks and list victims, this changed.
Alpha currently lists nine victims on its , an extortion portal, and the threat actor has already made the stolen files public for eight of them.
According to a Neterich report from January 29 and nbsp, Alpha has become more sophisticated over time.
The ransomware adds a random 8-character alphanumeric extension to encrypted files in the most recent version.
The most recent ransom note also includes instructions for victims to use a messaging service to get in touch with the threat actor.
Depending on the victim’s business size, the reported ransom demand, according to Neterich, could be as high as$ 100, 000 or as low as 0.27 BTC ($ 13, 200 at the current exchange rate ).
Netwalker links
Based on the tools, strategies, methods, and procedures used in attacks, a new report released today by Symantec’s threat analysts connects Alpha to the outdated Netwalker ransomware.
The following are some of the main parallels that Symantec emphasizes:
- Similar Power Shell-based loaders are used by Netwalker and Alpha ransomware to deliver their payloads.
- The general execution flow of the main functionalities, the termination of processes and services, and the similarity between calling system APIs are all significant code overlaps in the payload.
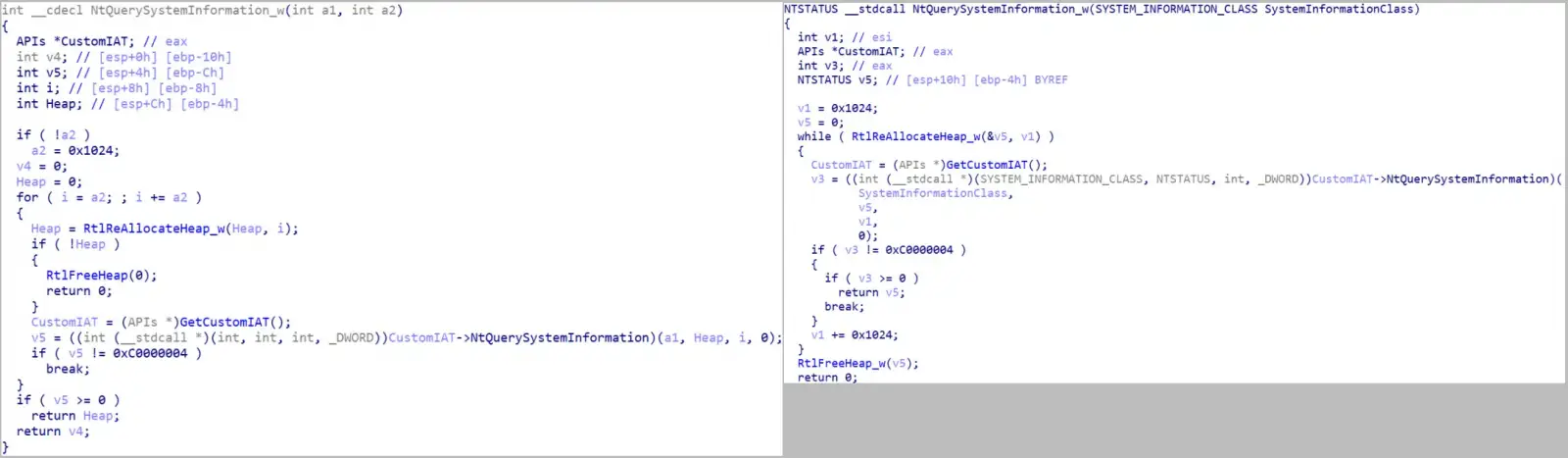
- Similar configurations can be found in the list of processes and services to be killed as well as the folders, files, and extensions that should be skipped.
- After the encryption process is finished, both delete themselves using a temporary batch file.
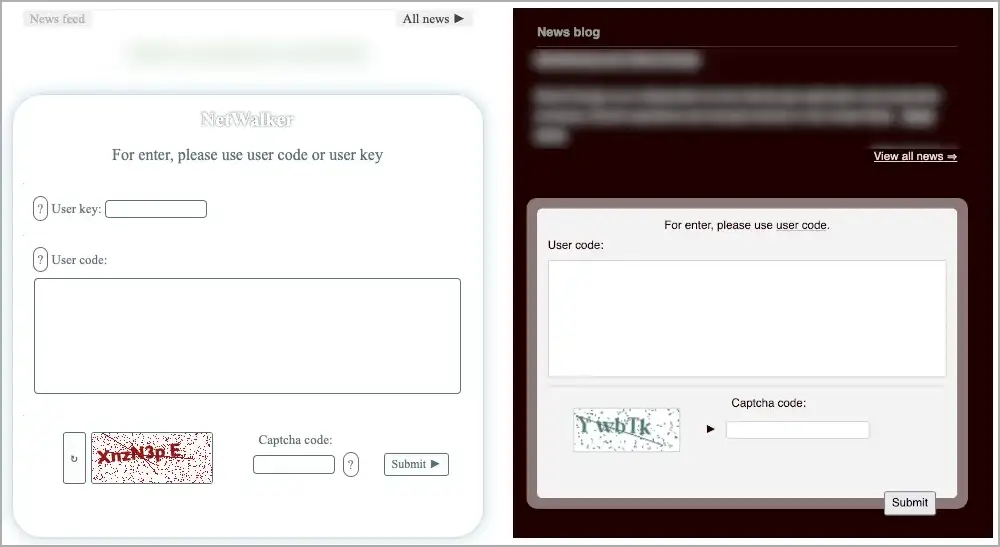
- The same message is displayed on the payment gateways for Netwalker and Alpha:” For enter, please use user code.”
Additionally, Symantec reports that living-off-the-land tools like Taskkill, PsExec, and Net have been heavily used in recent Alpha attacks. Reg. and Exe. For evasion, exe. But many ransomware gangs share this trait.
The aforementioned parallels suggest that NetWalker and Alpha’s developers are closely related, which may indicate that the company will resurrect under the Alpha name or that another threat group will reuse its code.
According to Symantec, the NetWalker payload could have been taken over by a fresh attacker and modified for ransomware purposes.
Alpha is regarded as an , or emerging threat organizations, even though it is not currently a significant player on the ransomware scene.











