In a cyberattack against a sizable business, malicious actors were discovered using the open-source hypervisor platform QEMU as a tunneling device.
Running other operating systems as guests on a computer is possible with the free emulator and hypervisor QEMU.
Threat actors used QEMU to build virtual network interfaces and a socket-type network device to connect to a remote server as part of the attack. With little to no performance impact, the threat actors were able to establish a network tunnel between the victim’s system and the attacker’s server.
This unusual case, which highlights the various tactic( s ) used by attackers to maintain secrecy, was discovered by Kaspersky Analysts, who were called in to look into suspicious activity in the breached company’s systems.
tunnels in a shady network
To communicate with a compromised system through a secret and secure network tunnel created by hackers.
In order to avoid firewalls, intrusion detection systems, and other security measures, these tunnels typically encrypt network traffic.
According to Kaspersky, hackers have created tunnels in 10 % of the cases it has looked into in the past three years using FRP, FRP, and Ngrok, Nbsp, utilities. Among the other tunneling tools used in attacks are  , CloudFlare tunnels, Stowaway, ligolo, 3proxy, dog-tunnel, chisel, gs-netcat, plink, iox, and nps.
Defenders and monitoring tools are suspicious of using these tools because they are frequently used by cybercriminals.
Even if that meant cutting down traffic encryption, the attackers in this unusual case involving QEMU chose to use a less conventional tool to create network tunnels that would unlikely raise alarms.
Additionally, QEMU has unique capabilities, such as allowing malicious activities to blend in with benign virtualization traffic and bridging segmented network parts with purposefully set up VM pivot points. It also emulates a wide range of hardware and virtual networks.
Feather-light backdoor
The hackers used” Angry IP Scanner” for network scanning, “mikmikatz” for credential theft, and QEMU to create a sophisticated network tunneling arrangement that enabled a covert communication channel in the attack seen by Kaspersky.
The attackers made an effort to minimize their footprint by only dedicating 1MB of RAM to the created virtual machine, which significantly reduces resource consumption.
The following statements are included in the configuration of the VM, which was started without a LiveCD or disk image:
- In user mode, a network backend named “lan” is configured in -netdev user, id=lan, restrict=off, and enables unrestricted network access through the host’s network stack.
- Creates a direct network link for the backend” sock” with -netdev socket, id=sock, connect=<, IP>, and: 443.
- -netdev hubport, id=port- lan, hubid=0, netdev=lan/sock: facilitates network connectivity between various backends by linking a network device (either lan or sock ) to a virtual hub hubid=0.
- -nographic: Reduces QEMU’s visibility and resource footprint by choosing command-line interaction instead of a graphical interface.
The attackers ‘ specific use of QEMU was replicated by Kaspersky in simulated tests, leading to the conclusion that the setup resembled the one in the diagram below.
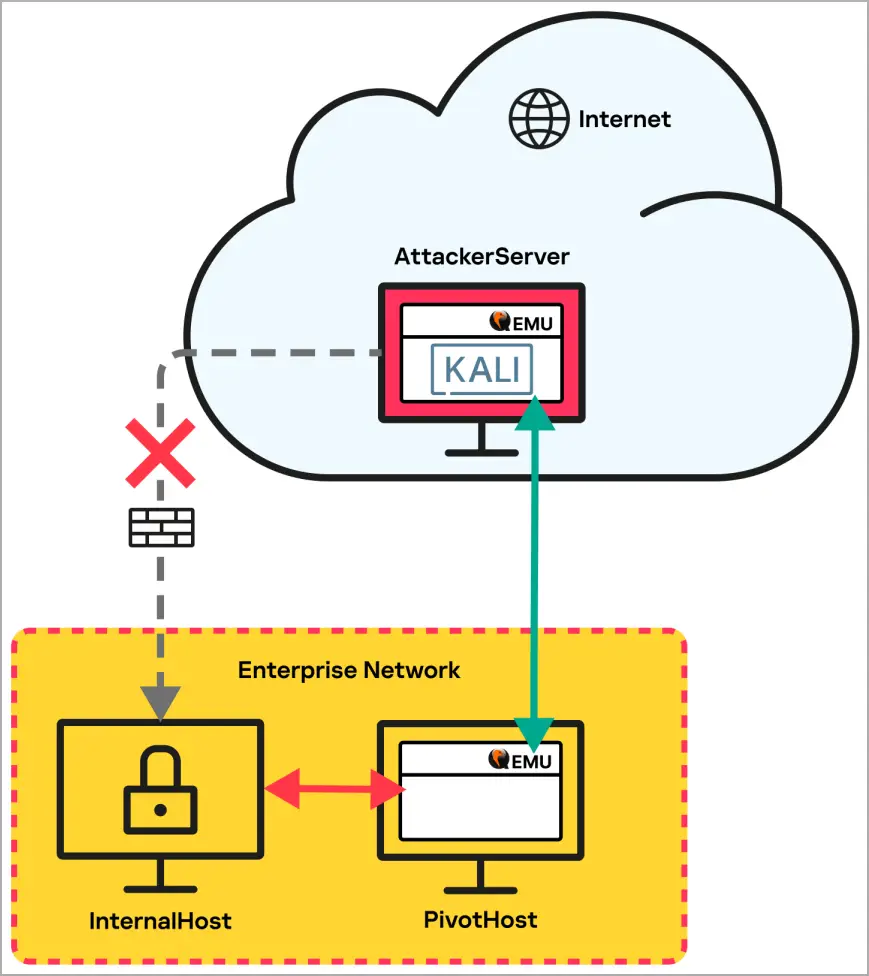
The attackers used QEMU to establish a network tunnel between the targeted internal host and a pivot host that does n’t have internet access and connects to the attacker’s cloud server running a Kali Linux VM.
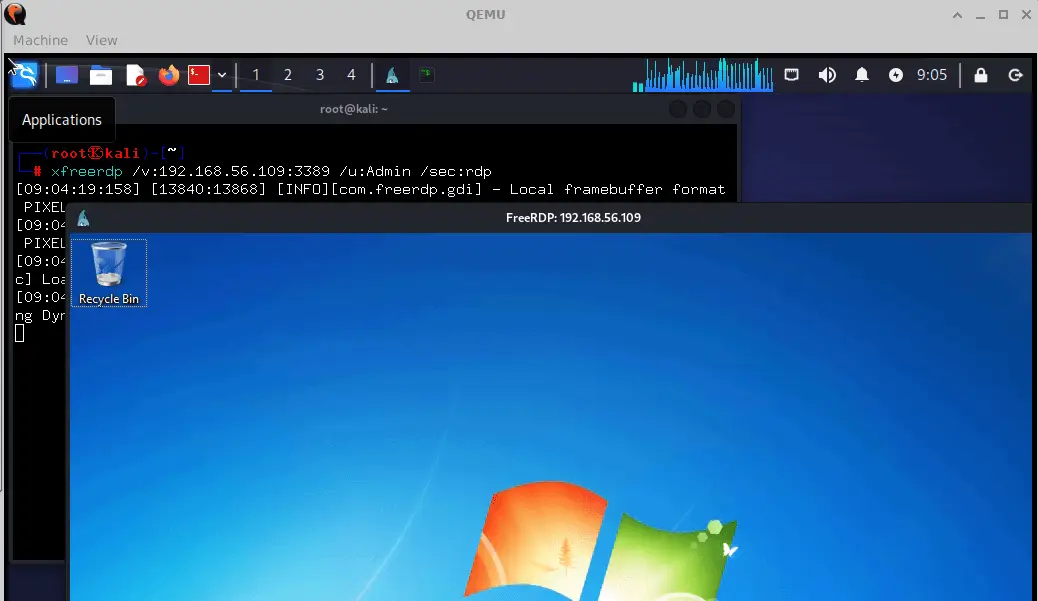
QEMU VMs’ ability to seamlessly connect and bridge segmented network components is crucial for avoiding security measures, which can also be leveraged laterally to further the breach.
According to Kaspersky, the enterprise should implement multi-level security, including 24/7 network monitoring, which may not be available to many small businesses.
This supports the idea of multi-level protection, which includes both trustworthy endpoint protection and specialized defenses against complex and targeted attacks, including those carried out by humans, in Kaspersky’s opinion.
According to SOC experts, “only comprehensive security that includes 24/7 network ( NDR, NGFW) and endpoint ( EDR, EPP ) monitoring can detect anomalies in a timely manner and stop an attack in its initial stage.”