Threat actors are using a backdoor code called DSLog to target vulnerable devices by using the recently discovered security flaw that affects ZTA gateways, Ivanti Connect Secure, and Policy Secure.
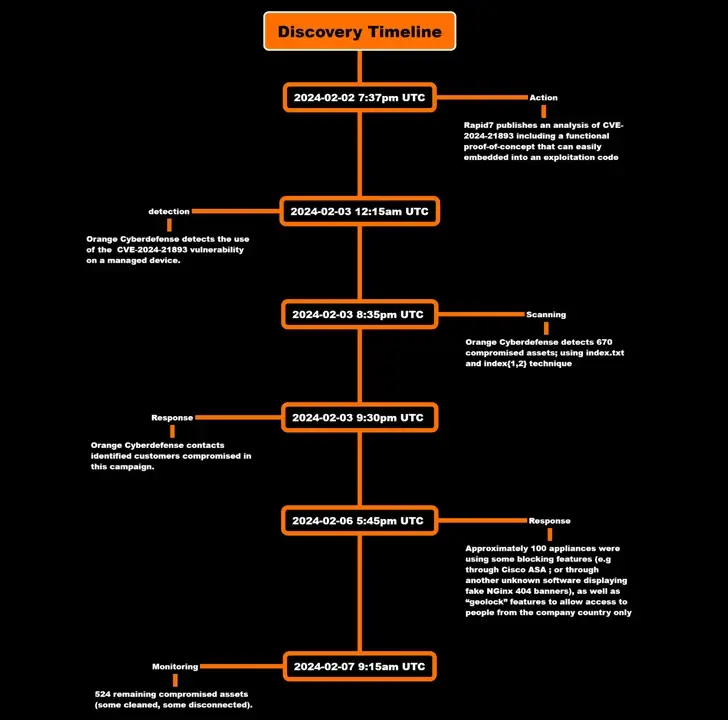
That is consistent with Orange Cyberdefense’s findings, which claimed to have seen CVE-2024-21893 exploited just hours after the proof-the-concept ( PoC ) code was made available to the public.
A server-side request forgery ( SSRF ) vulnerability in the SAML module is known as CVE-2024-21893, and if successfully exploited, could allow access to otherwise restricted resources without any authentication. This vulnerability was made public by Ivanti late last month along with CCE- 2024- 21888.
Although the precise scope of the compromises is unknown, the Utah-based company has since acknowledged that the flaw has only limited targeted attacks.
Following the sharing of additional technical details by Rapid7 and AssetNote, the Shadowserver Foundation last week reported an increase in exploitation attempts aimed at the vulnerability originating from more than 170 distinct IP addresses.
According to Orange Cyberdefense’s most recent analysis, compromises were found as early as February 3, when an unnamed customer was attacked and given persistent remote access via a backdoor.
” The backdoor is added to the” DSLog” Perl file that already exists. The company highlighted a persistent pattern of adding malicious code to already-existing, legitimate components, in this case, logging modules.
The implant, DSLog, has its own methods for impeding analysis and detection, such as embedding a distinct hash for each appliance, making it impossible for that device’s backdoor to be used on another device.
To enable malware to extract the command to be executed from a query parameter called” cdi,” attackers enter the same hash value into the User-Agent header field of an HTTP request to the appliance. The root user then executes the decoded instruction.
When attempting to contact the web shell, it does not return status or code, according to Orange Cyberdefense. ” Direct detection of it is not known to exist.”
Additionally, it found proof that threat actors were erasing” .access” logs on “multiple” appliances in an effort to evade detection and hide the forensic trail.
However, the company claimed that it was able to identify 670 compromised assets during a preliminary scan on February 3—a number that has since decreased to 524 as of February 7—by looking at the artifacts that were produced when the SSRF vulnerability was activated.
It is strongly advised that” all customers factory reset their appliance before applying the patch to prevent the threat actor from gaining upgrade persistence in your environment” given the ongoing use of Ivanti devices.