Institutions that provide cybersecurity services can rely on them in 2024
Financial services ‘ cybersecurity landscape is changing quickly. Traditional security measures are no longer necessary as a result of cybercriminals ‘ use of cutting-edge technologies and methodologies.
Community banks face additional difficulties because they must protect sensitive financial information from sophisticated threats on par with larger institutions, despite frequently having fewer resources.
Threat Landscape for FinServ
Recent trends indicate a startling rise in sophisticated cyberattacks. Banks are finding it harder and harder to distinguish between legitimate and malicious activities as a result of the sophisticated techniques used by cybercriminals today, such as deep fake technology and AI-powered attacks. A shift toward more sophisticated and adaptable cybersecurity measures is required as a result of these developments. Consider these statistics about the industry.
- Every week, 703 cyberattack attempts are reported by financial companies. 1.
- Financial services saw an increase of 31 % from the previous year in the number of attacks that involved unauthorized access to data, applications, networks, or devices. 2.
- Financial services companies typically take 233 days to find and fix data breaches. 3.
- In the event of a cyberattack, 43 % of senior bank executives do n’t think their institution is well-prepared to safeguard customer data, privacy, and assets. 4.
- Financial services typically cost$ 5.72 million per incident for data breaches. 5.
The financial sector is also at risk from state-sponsored cyberattacks. These attacks, which are frequently well-funded and highly sophisticated, aim to undermine financial institutions or steal sensitive financial data. In order to protect against these serious threats, community banks must be ready to use a different strategy than traditional cybercriminal tactics.
Similar to this, there has been a worrying trend in recent years where major service providers serving small- and medium-sized banks, like FIS, Fiserv, and Jack Henry, have emerged as prime targets for cyberattacks. Threat actors can expand their reach and increase the effectiveness of their efforts by targeting these service providers because doing so could give them access to numerous small banks. This emphasizes how crucial strong vendor management governance is. In order to protect against these serious threats, community banks must be ready to use a different strategy than traditional cybercriminal tactics.
The FinServ industry is in danger, and steps can be taken to protect it. Free Cybersecurity Workshops are offered by businesses like ArmorPoint, where seasoned cybersecurity experts identify particular security gaps and develop suggestions for reducing those risks.
How to Solve the Top 5 FinServ CybersecurityChallenges
1. Advanced methods for cloud security
Financial institutions are adopting cloud computing more and more because of its many advantages, including scalability, flexibility, and cost-effectiveness. This change does, however, bring with it specific security issues that can be difficult to handle. The requirement to safeguard data across various dynamic environments is what makes cloud security so complex. Traditional perimeter-based security methods are less effective in the cloud because data frequently travels between different services and geographic areas. Additionally, the cloud service provider and the bank may have conflicting security roles and responsibilities due to the shared responsibility model of cloud computing.
Banks must use cutting-edge cloud security techniques to deal with these problems. To protect data at rest and during transit, this entails implementing comprehensive data encryption, as well as strong identity and access management systems to regulate who has access to what information and when. Zero-trust security models are becoming more and more important because they demand verification from everyone attempting to access network resources and never assume trust. Effectively tailoring security measures also requires an understanding of the subtleties of various cloud environments, including public, private, and hybrid ones.
2. Beyond Basic Defense: Ransomware
Financial sector ransomware attacks have become more sophisticated, targeting institutions with strategies like” RaaS.” These institutions are especially vulnerable due to the constantly changing nature of ransomware and the high value of financial data. In the face of such sophisticated threats, which can circumvent conventional security measures and encrypt crucial data, resulting in operational disruptions and financial losses, conventional defense strategies are frequently insufficient.
Banks must put in place a multi-layered ransomware defense plan. Advanced threat intelligence systems that can offer real-time insights into new threats and vulnerabilities are included in this. To find and fix any potential weaknesses in the bank’s cybersecurity infrastructure, regular security audits are essential. Preventive threat hunting teams can also be crucial in spotting and eliminating threats before they materialize, adding a second layer of defense against attacks using ransomware.
3. Risk management for all vendors
For a variety of services, including cloud computing and customer relationship management, financial institutions are becoming more and more dependent on third-party vendors. Due to the possibility of managing or having access to sensitive bank data, each vendor relationship entails potential cybersecurity risks. It can be difficult to maintain consistent security standards across all third-party relationships because different vendors ‘ security postures and practices make managing these risks more difficult.
Beyond initial security assessments, effective vendor risk management necessitates ongoing monitoring and assessment of vendor security procedures. To make sure vendors follow agreed-upon security standards and practices, regular security audits are necessary. A unified approach to security is ensured by integrating vendor risk management into the bank’s overall cybersecurity strategy, which lowers the risk of security breaches related to vendors.
4. Navigating a Complex Landscape: Regulatory Compliance
The financial sector’s cybersecurity regulatory environment is complex and constantly changing. Numerous international, national, and regional regulations, each with its own set of requirements and penalties for non-compliance, must be followed by banks. Banks must constantly modify their cybersecurity strategies to meet these changing requirements, making it difficult for them to navigate this complex environment.
Community banks must gain a thorough understanding of pertinent laws, including the GBLA, PCI DSS, SOX, and others, in order to successfully navigate this environment. In order to keep up with regulatory changes and make sure that the bank’s cybersecurity practices comply with these requirements, this entails setting up a dedicated compliance team or even using the virtual Chief Information Security Officer (vCISO ). To ensure widespread understanding and adherence to compliance requirements, all staff members must regularly receive training and awareness programs.
5. 5. Filling the Talent Gap in Cybersecurity
Financial institutions face a significant challenge due to the lack of cybersecurity talent. Experts who are knowledgeable about the most recent technologies and tactics are necessary due to the rapidly changing nature of cyber threats. Banks find it challenging to find and keep the talent they need to effectively manage their cybersecurity risks due to a lack of such professionals on the market.
To close this talent gap, banks must implement innovative solutions. The creation of internal training programs can improve the skills of current employees, enabling them to handle more challenging cybersecurity tasks. A pipeline of qualified professionals can be built by working with educational institutions to create customized cybersecurity curricula. Utilizing AI and automation for routine security tasks can also maximize the use of talent by freeing up human resources for more difficult and strategic cybersecurity challenges.
Outsourcing is also a workable approach to filling the talent gap. Financial institutions may think about hiring outside security personnel and working with specialized companies to deliver skilled cybersecurity services. With this strategy, banks have access to a pool of seasoned experts who can effectively monitor, identify, and address security threats. To improve the bank’s overall cybersecurity posture, outsourcing executive-level insights like a virtual Chief Information Security Officer (vCISO ) can also offer strategic guidance and governance. Banks can more effectively fill talent gaps while keeping a strong emphasis on cybersecurity excellence by outsourcing specific talent needs.
Recently, ArmorPoint published a self-assessment of security maturity. To identify the gaps in your security posture, take the 15-question quiz.
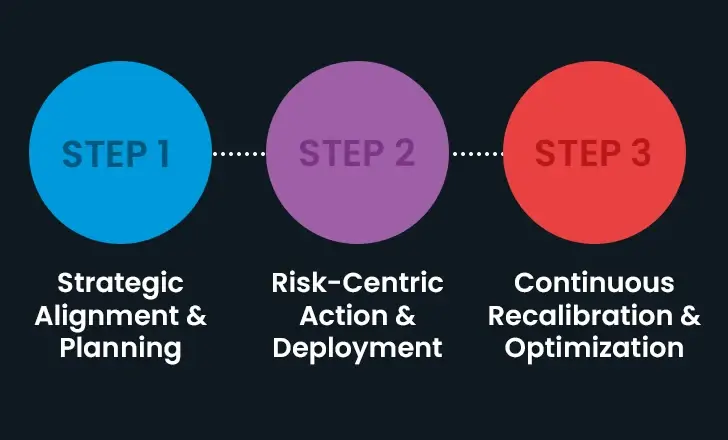
Implementing a Strong Cybersecurity Framework in Three Steps
For these various challenges to be effectively managed, cybersecurity must be approached holistically. This entails developing a unified framework that combines cutting-edge technology solutions, in-depth policies and procedures, routine risk assessments, ongoing monitoring, and proactive incident response planning.
First, strategic alignment and planning
A successful cybersecurity program’s strategic alignment and planning are its pillars. Setting clear cybersecurity goals that are closely related to the organization’s business objectives is a crucial first step. It is crucial to incorporate security controls into organizational strategy to guarantee that strong security measures support every aspect of business operations. The development of a framework for risk prioritization, which is crucial for locating and concentrating on the most serious threats, is another component of an effective strategy. Additionally, it is essential to create a security architecture that is tailored to the organization’s unique requirements and risk profile. The evolving landscape of cybersecurity threats and business requirements must be accompanied by a dynamic architecture.
Risk-Centered Action and Deployment, Step 2
Risk-centric action and deployment are the main focus of the second stage of creating a cybersecurity program. This entails creating a productive team structure that is committed to meticulously carrying out the cybersecurity strategy. The implementation of the tools and technologies required to carry out the strategic plan is a crucial part of this phase. Effective execution depends on turning high-level strategies into actionable, realistic steps. Critical network components are prioritized and strengthened through strategic resource allocation, particularly in areas with higher perceived risks. Furthermore, it is impossible to overstate the significance of ongoing security system monitoring and management because they are essential for preserving the effectiveness of security measures and quickly responding to new threats.
Step 3: Optimization and continuous recalibrating
The cybersecurity program’s continuous recalibration and optimization are the main priorities in the final phase. To ensure quick and efficient responses to threats, this phase necessitates maintaining accountability at all organizational levels and improving incident response capabilities. The foundation of this phase is the development of a cybersecurity-aware culture through the education of stakeholders and employees about security best practices and risks. For an environment of continuous improvement, regular evaluations and open disclosure of the program’s effectiveness to key stakeholders are essential. Based on ongoing assessments, the cybersecurity strategies should be constantly reviewed and improved. In keeping with the constantly changing business environment and the evolving landscape of cyber threats, this adaptive approach makes sure that cybersecurity measures remain both effective and relevant.
Getting ready for future threats and emerging trends
Emerging technologies and changing threat landscapes are likely to have an impact on cybersecurity’s future in the financial sector.
Cybersecurity using AI and machine learning
Threat detection and response will be completely transformed by the integration of AI and machine learning into cybersecurity tools. These technologies provide a level of speed and effectiveness unmatched by human analysts alone, allowing them to analyze enormous amounts of data to spot patterns indicating cyber threats.
Blockchain’s Function in Increasing Security
Financial transactions and data integrity may benefit from improved security features provided by blockchain technology. It is a desirable option for protecting transaction records and preventing fraud because it is decentralized and immutable.
Community banks must continue to be vigilant and proactive in their cybersecurity efforts because cyber threats are constantly changing. To protect against the various and sophisticated threats in the cyber environment, comprehensive and integrated cybersecurity strategies, a focus on cyber resilience, and preparation for future technological advancements are essential. Financial institutions can ensure the security and continuity of their operations while preserving customer trust and confidence by staying ahead of these difficulties.
Explore ArmorPoint’s solutions and feel the benefits of a coordinated approach to managing cybersecurity programs for more details on how to improve the security of your local financial institution.
Resources
1 https ://blog.checkpoint.com/security/check-point-research/cyber-attacks-increased by 50 % annually
2 https ://www.accenture .com/us-en/security/state-cybersecurity
3 Financial Data Risk Reports for 2021 at https ://info.varonis.com/hubfs/docs ?hsLang=en
4 https://kpmg.com/us/en/articles/2022/cybersecurity .html
5 https://www.ibm.com/reports/data-breach