Applications could be prevented from accessing the internet for an extended period of time using a serious vulnerability called  , KeyTrap in the Domain Name System Security Extensions ( DNSSEC ) feature.
KeyTrap, also known as CVE-2023-50387, is a DNSSEC design flaw that affects all widely used Domain Name System ( DNS ) implementations and services.
A single DNS packet can be sent by a remote attacker to render vulnerable resolvers permanently denial of service ( DoS ) conditions.
By entering domain names rather than the IP address of the server that our computer must connect to, humans can access online locations.
A DNS feature called DNSSEC adds cryptographic signatures to DNS records, giving responses authentication. This verification makes sure that DNS data originates from the DNS’s authoritative name server and has n’t been altered while being sent to a malicious site.
Request for significant damage in one attack
Researchers from the National Research Center for Applied Cybersecurity ATHENE, Fraunhofer SIT, Goethe University Frankfurt, and the Technical University of Darmstadt all contributed to the discovery of KeyTrap, which has been included in the DNSSEC standard for well over 20 years.
The issue, according to the researchers, is caused by DNSSEC’s requirement to send all necessary cryptographic keys for supported ciphers along with their corresponding signatures in order for validation to take place.
Even if some DNSSEC keys are incorrect, misconfigured, or come from unsupported ciphers, the procedure remains the same.
The researchers created a new class , of DNSSEC-based algorithmic complexity attacks, which can slow down the DNS resolver’s response by 2 million times the CPU instruction count.
According to the researchers, a single attack request can hold the response for up to 16 hours, but the duration of this , DoS state varies depending on the implementation of the resolver.
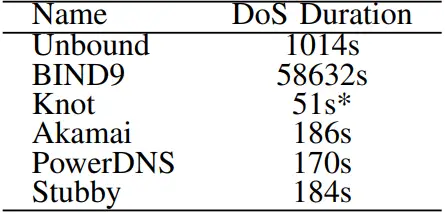
According to ATHENE’s disclosure, using this attack would have serious repercussions for any Internet-based application, including the inaccessibility of technologies like web browsing, e-mail, and instant messaging.
According to the researchers, KeyTrap could completely disable a significant portion of the global Internet.  ,
The technical report , which was released earlier this week, contains all the information you need to know about the vulnerability and how it might show up on contemporary DNS implementations.
Since early November 2023, the researchers have shown how their KeyTrap attack can affect DNS service providers like Google and Cloudflare, and they have collaborated with them to create mitigations.
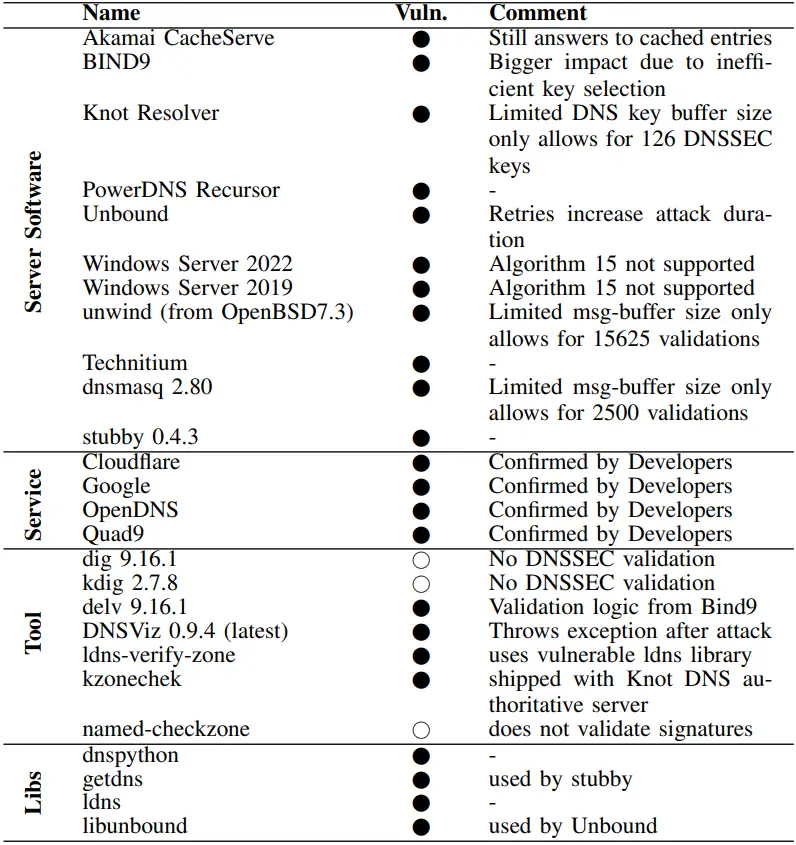
According to ATHENE, KeyTrap has been a part of frequently used standards since 1999, but due to the complexity of DNSSEC validation requirements, it went unnoticed for almost 25 years.
Although affected vendors have already pushed fixes or are working to reduce the KeyTrap risk, ATHENE warns that the DNSSEC design philosophy may need to be reevaluated in order to address the problem fundamentally.
Between December 2023 and February 2024, Akamai created and implemented mitigations for its cloud and managed solutions as well as its DNSi recursive resolvers, CacheServe and AnswerX, in response to the KeyTrap threat.
A highly effective denial-of-service ( DoS ) attack could have been launched against one-third of DNS servers worldwide as a result of this security gap, potentially affecting more than one billion users. – Akamai
According to Akamai, KeyTrap is vulnerable to DNS resolvers that use DNSSEC validation and account for about 35 % of U.S. and 30 % of internet users worldwide, according to APNIC data.
The ATHENE paper describes Akamai’s solution as restricting cryptographic failures to a maximum of 32, making it nearly impossible to deplete CPU resources and result in stalling, even though the internet company withheld many specifics about the actual mitigations it implemented.
Google and Cloudflare’s DNS services already have fixes.











