The difficulty of securing software supply chains has once again been highlighted by a reverse engineering of the firmware running on Ivanti Pulse Secure appliances.
The Utah-based software company’s base operating system for the device is CentOS 6.4, according to Eclypsiusm, which acquired firmware version 9.1.18.2- 24467.1 as part of the process.
According to a report provided to The Hacker News,” Pulse Secure runs an 11-year-old version of Linux that has n’t been supported since November 2020.”
Threat actors are taking advantage of several security flaws found in ZTA, Ivanti Connect Secure, and Policy Secure gateways to deliver a variety of malware, including web shells, stealers, backdoors.
The vulnerabilities that have been actively exploited in recent months include CVE-2023-46805, CCE-2024-21887, and CVP-21893. Another software bug that could allow threat actors to access otherwise restricted resources without any authentication was also disclosed by Ivanti last week (CVE-2024- 20224 ).
Following the release of a proof-of-concept ( PoC ) by watchTowr, web infrastructure company Akamai reported yesterday that it had seen” significant scanning activity” targeting CVE-2024-22024 starting February 9, 2024.
Eclypsium claimed that in order to obtain a reverse shell for the PSA3000 device and export the device image for follow-up analysis using the EMBA firmware security analyzer, Rapid7 released the PoC exploit for CVE-2024-21893 earlier this month.
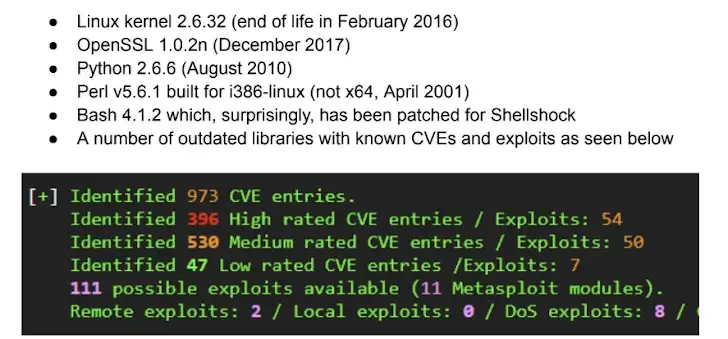
This revealed numerous outdated packages, supporting earlier research by security researcher Will Dormann, as well as numerous weak libraries that are collectively vulnerable to 973 flaws, of which 111 have exploits that have been made public.
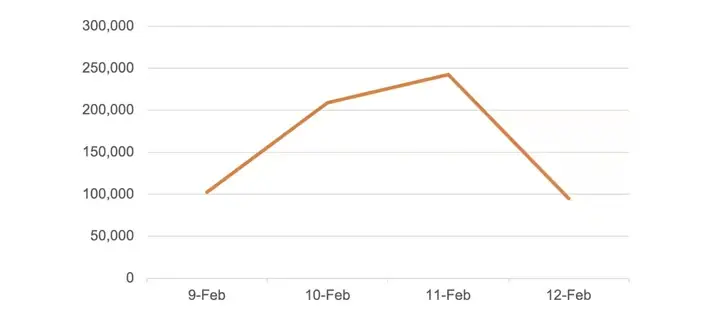 |
| daily scanning requests for CVE-2024-22024 |
For instance, Perl has n’t received an update since its 23-year-old April 9, 2001 release of version 5.6.1. As of March 2016, the Linux kernel version, 2. 6.32, had reached end-of-life ( EoL ).
The Ivanti Connect Secure product includes these outdated software packages, according to Eclypsium. This is the ideal illustration of the significance of digital supply chain visibility and the rising demand for SBOMs from business customers.
Additionally, a closer look at the firmware revealed 133 out-of-date certificates, 5, 218 vulnerabilities in 5, 392 Python files, and 1,216 issues in 76 shell scripts.
The problems do n’t stop there; Eclypsium discovered a” security hole” in the Integrity Checker Tool’s logic, which Ivanti had advised its users to use to check for compromise indicators ( IoCs ).
In particular, it has been discovered that the script prevents the scanning of more than a dozen directories, including data, etc., tmp, and var, which could theoretically allow an attacker to place their persistent implants along one of these paths and still pass the integrity test. However, the tool scans the home partition where all configuration files and product-specific daemons are kept.
Eclypsium found that the Sliver post-exploitation framework offers a “false sense of security” by deploying it to the /data directory and running ICT reports without problems.
It’s important to note that in an effort to avoid detection, threat actors have also been seen altering the ICT on compromised Ivanti Connect Secure devices.
A threat actor could abandon their next-stage tooling, store the information they collected in the /data partition, and then abuse another zero-day flaw to access the device and exfiltrate the data they had previously staged, all the while the integrity tool picks up on any indications of anomalous activity, as demonstrated by Eclypsium.
According to the company, there needs to be a system of checks and balances that enables both customers and outside parties to verify the security and integrity of the product. We can validate the digital supply chain, or the hardware, firmware, and software components used in their products, more effectively the more transparent this process is.
Validation and visibility are challenging when vendors do n’t share information and/or run a closed system. Attackers will undoubtedly take advantage of this circumstance and exploit the system’s lack of controls and visibility, as recent evidence has shown.