A remote access Trojan called Konni RAT ( also known as UpDog ) has been backdoored by an installer for a tool that is probably used by the Ministry of Foreign Affairs ‘ ( MID ) Russian Consular Department.
German cybersecurity firm DCSO published the findings and claimed that the Democratic People’s Republic of Korea ( DPRK)- Russian nexus actors were responsible for the activity.
Attacks against MID have been linked to the Konni ( also known as Opal Sleet, Osmium, or TA406 ) activity cluster since at least October 2021, and the threat actor has a history of being used against Russian entities.
Microsoft Word documents written in Russian were used by Fortinet FortiGuard Labs to deliver malware that could collect sensitive data from compromised Windows hosts in November 2023.
According to DCSO, the group previously used the packaging of Konni RAT within software installers in October 2023 after discovering that it used Spravki BK, a backdoor Russian tax filing program, to distribute the trojan.
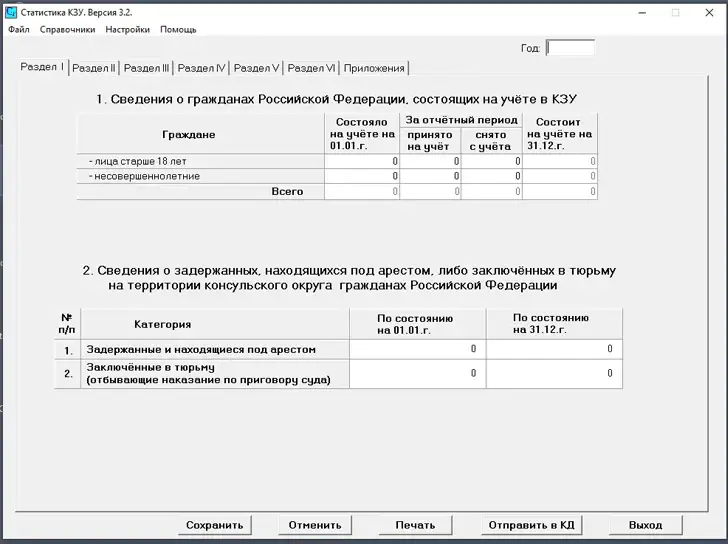
According to the Berlin-based company,” In this case, the backdoored installer appears to be for a tool called” Statistika KZU” ( Cтатистика ).
The software is designed for internal use within the Russian Ministry of Foreign Affairs ( MID), specifically for relaying annual report files from overseas consular posts ( консулские арануредени ) to the Consular Department of the MID via a secure channel, on the basis of install paths, file metadata, and user manuals bundled into the installer.
An MSI file called the trojanized installer starts the infection sequence when it is launched in order to make contact with a command-and-control ( C2 ) server and wait for further instructions.
It is thought that Kimsuky and ScarCruft ( also known as APT37 ), two other North Korean threat actors, have used the remote access trojan, which has features for file transfers and command execution, since 2014.
Given that the installer is not currently available to the public, it is unclear how the threat actors were able to obtain it. However, it’s possible that they were able to identify potential targets for future attacks thanks to their extensive history of espionage operations against Russia.
Although North Korea has been targeting Russia for some time, the two nations ‘ geopolitical proximity is growing. This week, Kim Jong Un received a luxurious Russian-made car from Russian President Vladimir Putin, according to state media from the Hermit Kingdom.
The DPRK continues to need to be able to assess and verify Russian foreign policy planning and objectives, so this should not come as a surprise, according to DCSO. Increasing strategic proximity is also not expected to completely override current needs.