The creation and spread of the ransomware-as-and-service model, a method of giving cybercriminals simple, affordable tools with which to carry out and manage ransomeware campaigns, has been one of major factors in the explosion in runsom malware attacks over the past five years and beyond. Developers avoid directly engaging in criminal activity while still receiving a steady stream of income from subscription sales. This model has taken on a new twist thanks to the recently discovered Kryptina Raas, an openly accessible tool rather than being available for purchase.
In this article, we examine Kryptina RaaS’s evolution, technicalities, and effects as well as its transition to open-source crimeware. In order to defend against the most recent Linux ransomware and the risks that open source threats pose to organizations, we delve into what defenders must be aware of.
Kryptina RaaS’s Growth
The Kryptina RaaS, a lightweight, quick, and highly customizable ransomware solution for Linux systems, first appeared on underground forums in December 2023. It was written in C and made a compelling case for cybercriminals looking to target the cloud workloads and Linux servers that make up the networks of many organizations.
At first, there were only two ways to buy: a$ 20 standalone build ( encryptor and decrypter ), or if you wanted$ 500, you could buy the entire package, including the source code, builder, and documentation. In January, the developer added new features right away, including support for Monero (XMR ) and Bitcoin ( BTC ) payments, an updated web interface, and 32 and 64-bit targets. With the addition of these new features, the total package cost increased to$ 800. The creator’s intention to serve a variety of actors in the cybercriminal ecosystem was clear from this pricing strategy.
The creator,” Corlys,” published the entire source code on BreachForums in February, effectively removing any financial barriers to entry.
The source code for Kryptina was made public by the developer for apparent reasons, including the fact that it was unsuccessful in luring customers. Some people might not find this credible given the short time between the open source code’s release and its initial appearance as a paid offering. Other reasons might include a desire to gain respect from the cybercrime community, rivalries with other criminals, or the worry that law enforcement will take notice.
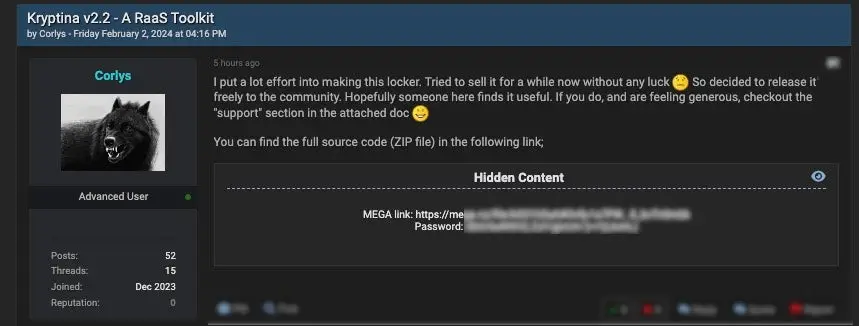
Whatever the motivation, the widespread distribution and impact of ransomware attacks on Linux systems could be significantly impacted by the release of the RaaS source code, which includes extensive documentation. It will probably make the ransomware builder more appealing and usable, which will attract more low-skilled users to the cybercrime ecosystem. Additionally, there is a sizable chance that it will result in the creation of numerous spin-offs and an increase in attacks, as was previously seen following the source code leak for Babuk ransomware.
Technical Information About Kryptina Payload
Kryptina, as previously mentioned, is a Linux-only ransomware that provides payloads for the elf64- and 32-architecture architectures. The directories and files specified in the builder during the configuration stage are the targets of the ransomware when it is executed.
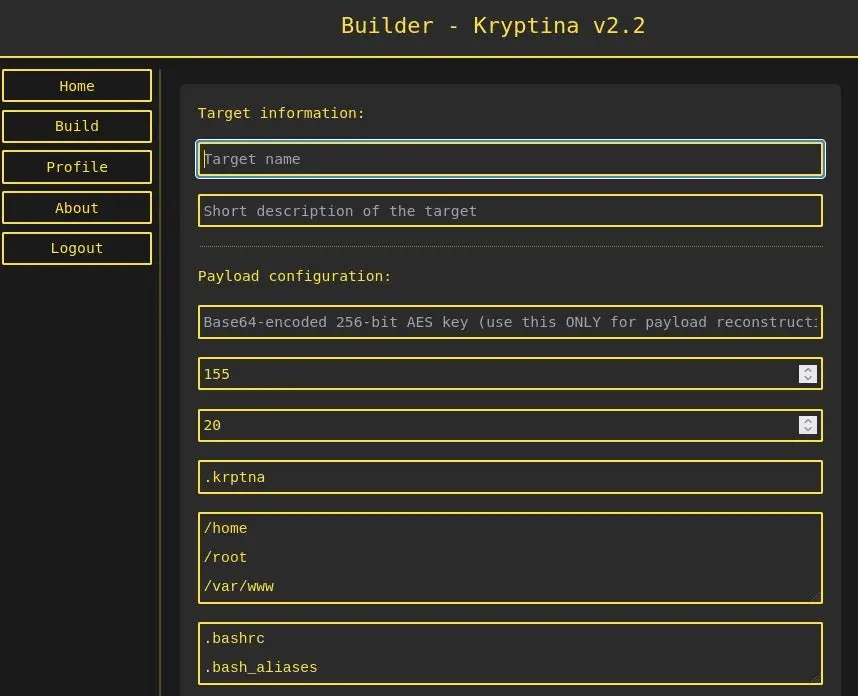
The encryption process uses multiple parallel threads and depends on OpenSSL’s libcrypto library. It uses the AES256 algorithm in CVC mode. The keys and configuration data are obfuscated via XOR using a custom value defined at build time, and then base64 encoded.
File encryption is handled by the krptna_process_file() function. This initializes an OpenSSL cipher context EVP_CIPHER_CTX_new() before processing file streams via EVP_CipherUpdate() to transform unencrypted file data to the encrypted data in the output buffer. EVP_CipherFinal finalizes the processes and handles any required CBC padding.
Payloads can be configured to securely delete files before encryption, further hampering any data recovery efforts. When enabled, multiple steps are taken to overwrite individual file data and inhibit recovery. The secure_delete_file() function determines the file size using the stat function. It then creates a buffer filled with random bytes. The file to be encrypted is then opened in write mode, and the buffer of random bytes is written into the file, completely overwriting its original content, until it matches the file’s original size. Once this is achieved, the file is permanently removed using the unlink function.
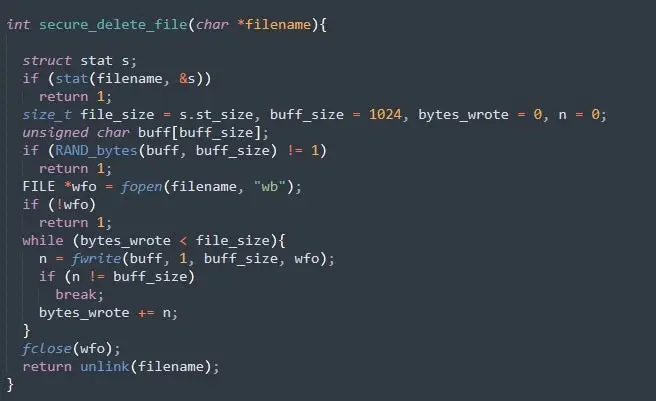
The secure_delete_file() function utilizes a single-pass method, overwriting each byte of the file just once, avoiding using multiple overwrites with varying patterns seen in other ransomware. A single pass is generally adequate for rendering the original data unrecoverable and increases the speed of encryption.
Builder and Kryptina Web Interface
Kryptina’s architecture is built on a foundation of Python scripts for the payload builder and web server components, requiring dependencies like pycrypto, termcolor, flask, and others for full functionality. The tool’s source code is well-documented, reflecting an intent to provide Kryptina as a turnkey solution.
As previously mentioned, Kryptina has undergone a number of quick revisions since its release, with version 2.0 introducing important improvements, such as an interface. The Flask-powered web server makes it simple for users to view and manage campaigns, create encryption and decryptors, and communicate with victims using the” Chast” option. Victims can contact the attacker by following the instructions in the ransom note if the operator sets up” Enable Public View” for the campaign.
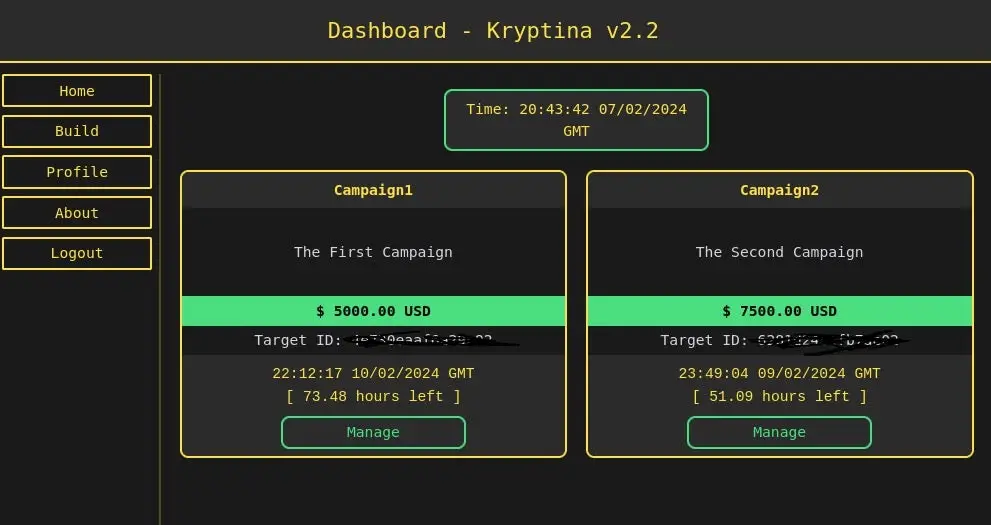
For specifying target names, descriptions, encryption keys, directories or files to target, and more, the builder supports a wide variety of command-line arguments. The versatility and granular control Kryptina provides to users are emphasized by this level of customization.
The following command-line parameters are supported by the builder, which can also be scripted with Python.
| Arg | Description |
| -n | Your target’s name |
| -a | About, a brief explanation of your objective |
| -k | Use a base64-encoded 256-bit key ( default: random ) |
| -t | Target directories or files ( comma-separated ) |
| -i | To ignore files or extensions ( comma-separated ) |
| -e | Use a custom extension ( default :.krptna ) |
| -j | Maximum number of jobs ( threads ) allowed ( default: 20 ) |
| –arch32 | Make a 32-bit binary ( x86 ) file. |
| –xor_key | Using the XOR key ( default: 155 ) to encode encrypted configuration data |
| –note | the local file with the default note/template encryption notice text. ( txt ) |
| –note_name | The target’s absolute/relative filename for the encryption notice |
| –nonote | Avoid leaving an encryption note on the target. |
| –bitcoin | Address for receiving payments in a bitcoin wallet |
| –monero | Address for receiving payments in a Monero wallet |
| –amount | The USD amount to request ( default: 100.0) |
| –deadline | The payment due date in hours ( default: 72.2 ) |
| –tox | the Tox chat ID you’d like to be contacted with |
| –session | the chat ID for the session you want to be contacted. |
| –debug | Debug output is enabled. |
| –demo | Make a demo payload that does n’t actually encrypt/decrypt files. |
| –symbols | Debug symbols (-ggdb3 ) are used to build binary. |
| –nolog | Payload configuration should not be recorded in the output or directory. |
| –persist | Disable self-detect payload |
| –secdel | When encrypting files, enable secure delete, which is very slow but makes recovery much more difficult. |
| –maxsize | Maximum file size ( in megabytes ) for the target ( default: unrestricted ) |
| –recommend | Auto-set suggested values for parameters that are not specified. |
| –static | Create static binaries for the payloads. |
| –verbose | Commands and output of the print compiler |
Kryptina ransomware is protected by SentinelOne.
Kryptina ransomware is detected by SentinelOne Singularity, which also safeguards Linux systems. Kryptina’s malicious actions and indicators can be seen in the Management console when she is permitted to run in” Detect Only” mode for observational purposes.

Identifying the Kryptina Threat to Linux Systems
The complexity of threats facing network defenders is demonstrated by Kryptina RaaS’s transformation from a paid underground tool to an open-source project that is freely available. It’s likely that a variety of Kryptina variants will proliferate similarly to how we saw Babuk variations multiply and diversify as other actors iterate on the provided code, which offers everything from customizable ransomware payloads to campaign management and victim communication.
The appeal of Linux as a target for cybercriminals increases as the transition to cloud and cloud workloads and containers accelerates. Modern enterprise environments depend on Linux systems, which power everything from edge devices to servers, orchestration technologies like Kubernetes, and cloud infrastructure like AWS, Azure, or Google Cloud. Securing these systems is crucial.
Contact us or ask for a free demo to find out how SentinelOne can assist in defending your company’s Linux systems against ransomware and other threats.
Compromise Indicators
the original files
03bbfdbad1d1fd93d6c76de9a61e9cfc49e7e319
095538ff7643b0c142335c978bfe83d32a68cdac
1f08d9d0fe90d572a1bb0488ffe60e9f20c11002
226aea1e37bc2d809115ceb6ac5ea99e62d759c9
2aa6a1019c16f4142888278098f0c3263e95e446
33306b854770f95d0a164932d72bec1f78de54bf
51acdb8f29726fe7d5b6207f106e7138b564fd39
5413adf32129d50c4984e406d5a3804435d1cfc1
60b5beffaf738f5112233ed9b36975822c1f7bfc
6f3c3129fc2ac56b61fa4df21e723f3dd2aceb70
8ec866aa48a9bb8d6df7fbbe1a073390f4b0098c
d0231ce29ea7a63bea7451c42d69e93c83babb48
d41b8a7bc9bc444372e06e67585a8086d6ae8cfc
d46fbc4a57dce813574ee312001eaad0aa4e52de
ddcf4a6bc32afe94e3ea955eead9db179d5394c2
e3e8ed6ac01e6edb8d8848b1472882afb0b36f0b
f84ffe172f9d6db18320ad69fc9eade46c41e9da
Sample Payloads
355d70ffe98e6f22b6c3ad8d045e025a5ff78260
63580c4b49d350cf1701fb906c94318a683ae668
63ff8359da29c3ba8352ceb4939f2a3e64987ab6
dd495839a4f4db0331c72a4483071a1cef8da17e
CK MITREATT&
Defense EvasionT1014 
T1059.006 Command and Scripting Interpreter: Python
T1068 Privilege Escalation
T1070.003 Indicator Removal: Clear Command History
T1070.004 Indicator Removal: File Deletion
T1070.002 Indicator Removal: Clear Linux or Mac System Logs
T1140 Deobfuscate/Decode Files or Information
T1222.002 File and Directory Permissions Modification: Linux and Mac File and Directory Permissions Modification
T1485 Data Destruction
T1486 Data Encrypted for Impact
T1562.001 Impair Defenses: Disable or Modify Tools
T1562.012 Impair Defenses: Disable or Modify Linux Audit System
T1573.002 Encrypted Channel: Asymmetric Cryptography











